“You are your data.”
It’s a no-brainer to say that data is an everyday part of an average person’s lifetime. People of all ages and backgrounds are connected to the cybersphere doing things like communicating with others, getting work done, and even having some fun. Technology has evolved and advanced exponentially, enabling people to get things done more easily and efficiently.

However, with technology getting more sophisticated, so are the corresponding cybersecurity attacks. Big Data has allowed people to profile people based on their cyber-history, which is how targeted advertising came to be. This also means unscrupulous attackers would be able to have a clear map of where to go and what weaknesses to exploit without their target even knowing it.
One can build complex, sophisticated system of defenses to protect themselves, but just one hole, and the game’s up before it even started. The good news is there are many simple ways users can protect themselves and their data. Here are 10 of those ways:
Think before you click.

One of the most common ways attackers get inside their target is through email links. If you don’t know who sent that email, don’t open it. Especially be careful if there are links and attachments inside that email.
Common signs of malicious emails include:
- Use of a link shortener (like bit.ly or tinyurl.com). Be sure to check the link using a tool like unfurlr to know the long URL without clicking on the link itself.
- Intentional misspellings. Attackers typically craft the email address they use to send the email such that a user will think it’s from a legitimate source at first glance. Inspect all email addresses closely.
- Unsolicited requests for personal information. Malicious emails will typically request you for your personal information for “security purposes”. This is a red flag.
Also think before you click on advertisements. Especially those that tell you that you won a raffle draw you didn’t join, or those that claim that you have a virus and you should click on the link for them to clean it.
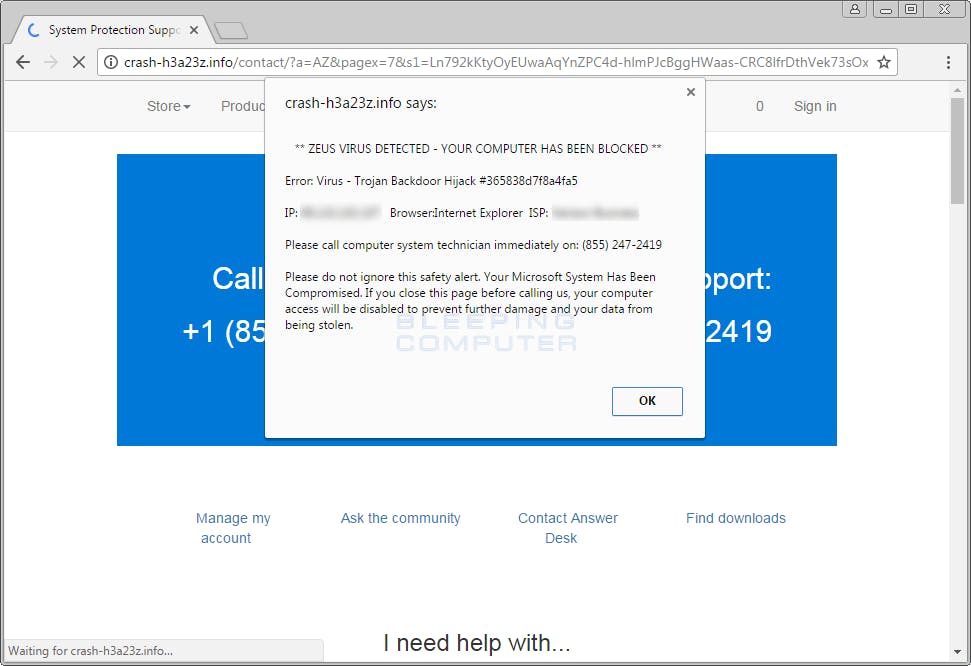
image source: https://www.bleepingcomputer.com/virus-removal/remove-zeus-virus-detected-popups
Trust no one.
Social engineering is perhaps the most insidious form of cybersecurity attack there is, mainly because it’s a social attack that takes advantage of human (the weakest link in the cybersecurity chain) weaknesses. Don’t give out your credentials to anyone (even your well-meaning best friend), don’t write them down on a piece of paper, don’t give the attacker ideas.
This also means avoid oversharing on social media. Many attackers have guessed passwords and other credentials through trial and error of common information. The United States Computer Emergency Readiness Team (US-CERT) advises, "Do not post information that would make you vulnerable, such as your address or information about your schedule or routine. If your connections post information about you, make sure the combined information is not more than you would be comfortable with strangers knowing. Also be considerate when posting information, including photos, about your connections,"
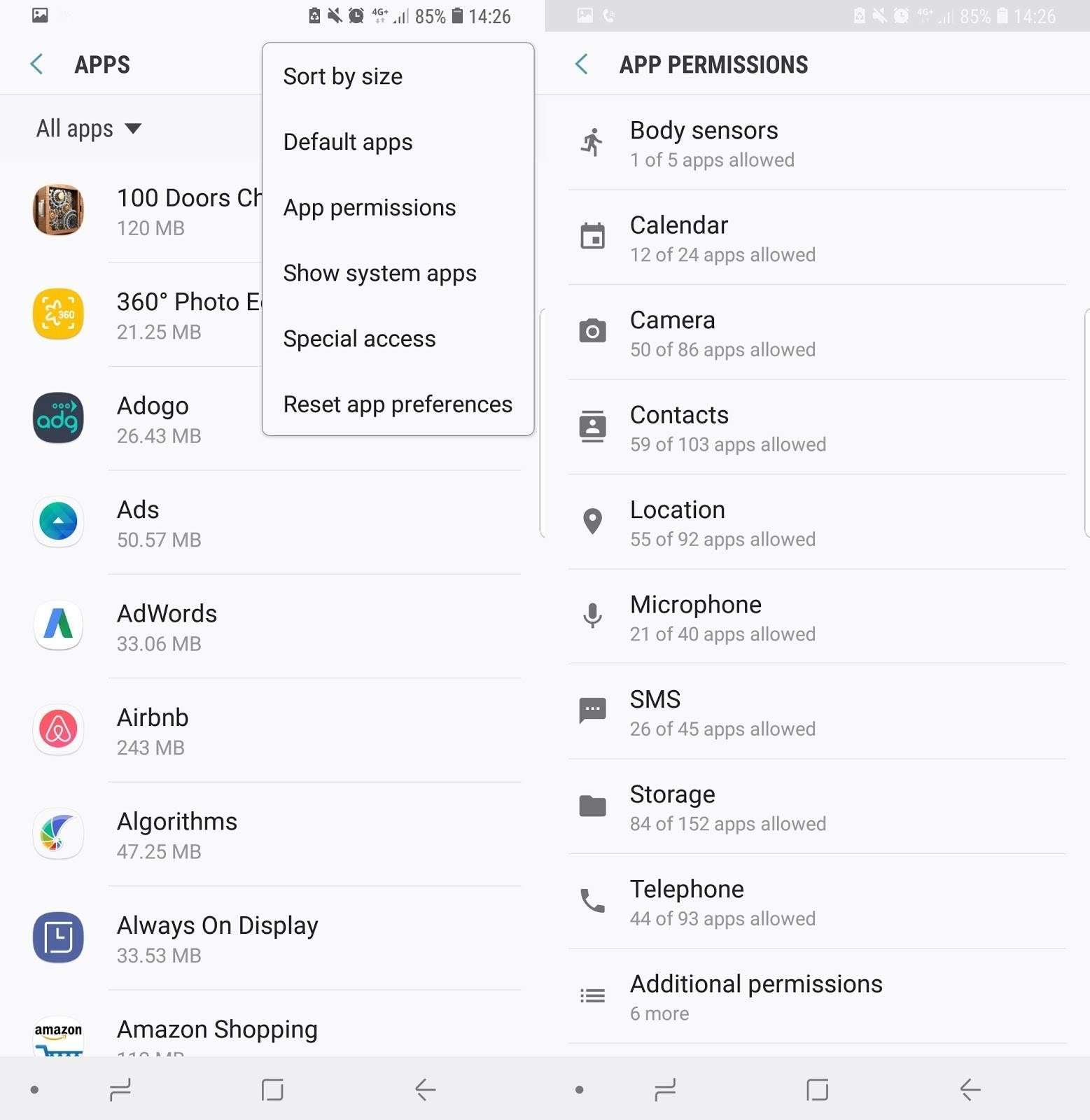
Be mindful of installing mobile apps.
Check the app’s permissions to see what data do they want to access. Think twice if a seemingly harmless smartphone game wants to access your call logs, for example.
To check the app’s permissions, do the following:
On Android devices: Open the Settings app, then Apps & notifications, App info, and the app you're interested in. The permissions it has are contained in the Permissions entry.
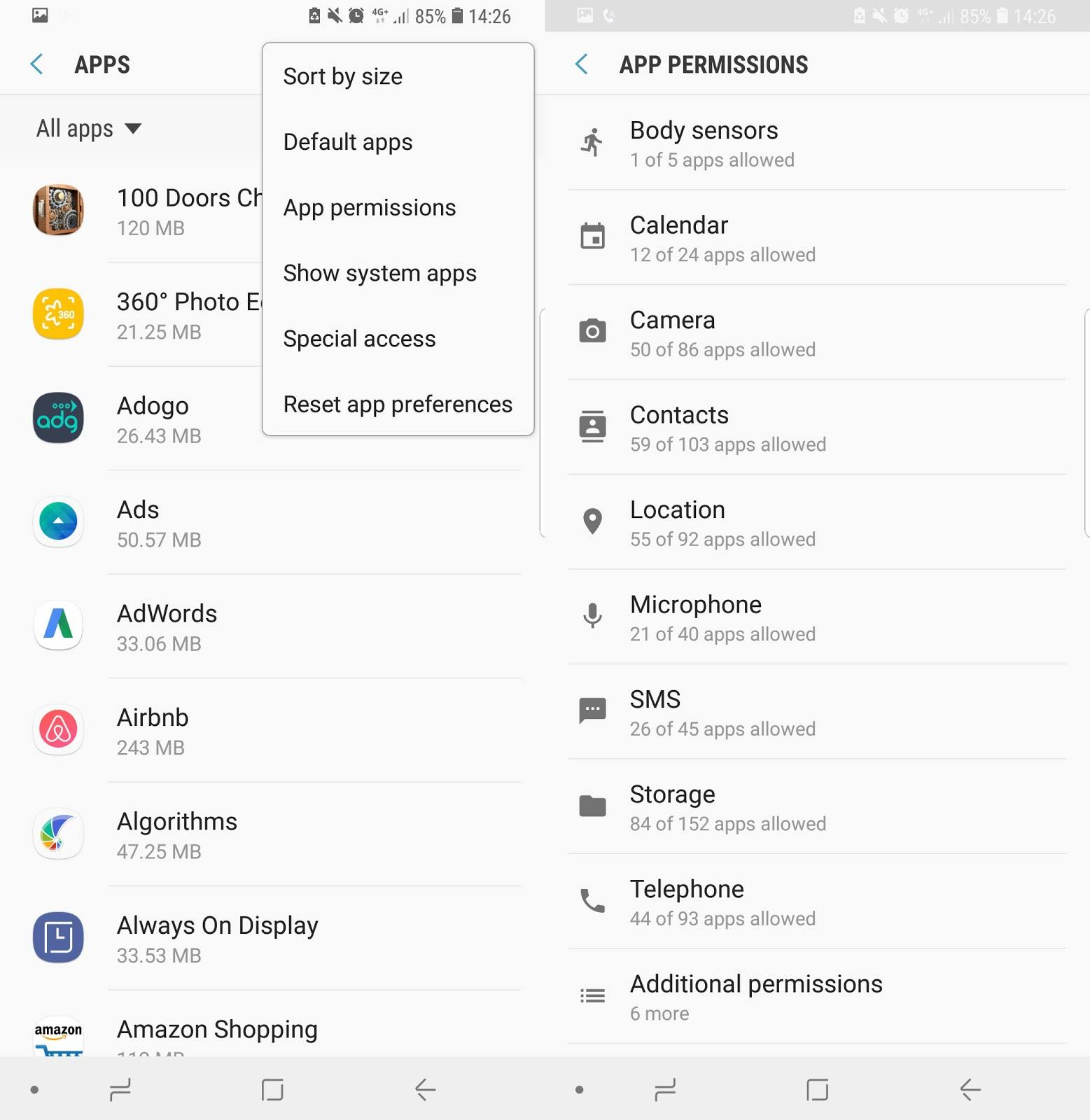
screenshot of privacy settings on Android
On iOS devices: Open the Settings app, then tap Privacy. In iOS, permissions are grouped by type
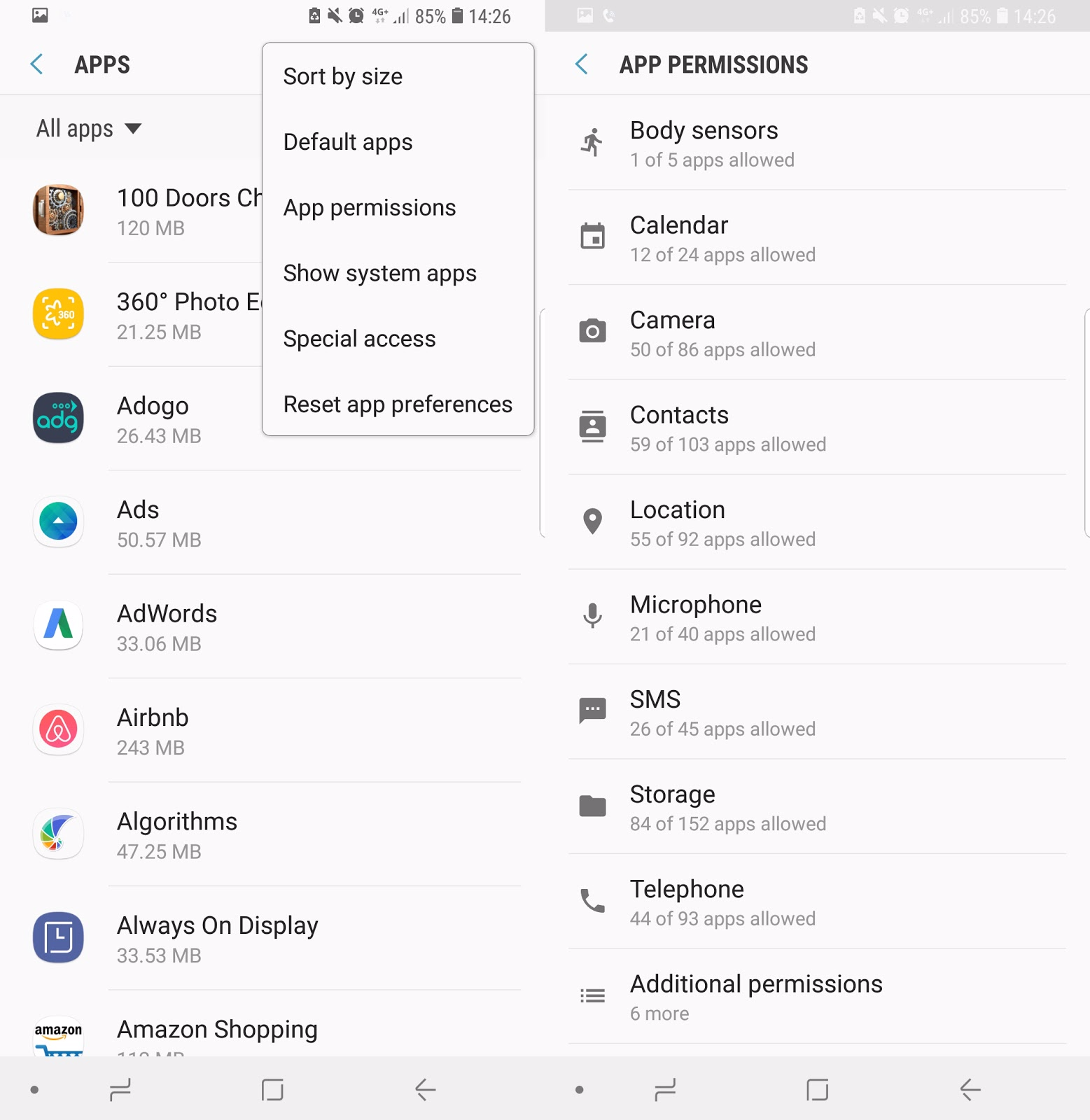
screenshot of privacy settings on Android
Think in phrases and sentences, not words.
Don’t use passwords that are easy to guess, nor use passwords that are linked to your personal information. With computers getting smarter and more sophisticated, it’s easier for the attackers to crack passwords the shorter and sweeter they are. And you won’t want to tempt them with treats, right?
It’s going to be much easier for you to remember the passphrase if you associate them with a sentence. To give out an example, the phrase “My passphrase is more secure than yours.” Could be translated as: m3P@$$>>>urZZZ
Keep your enemies close, but your (multi-factor) devices closer.
Ensure that you enable multi-factor authentication (MFA) in all your accounts whenever you can.
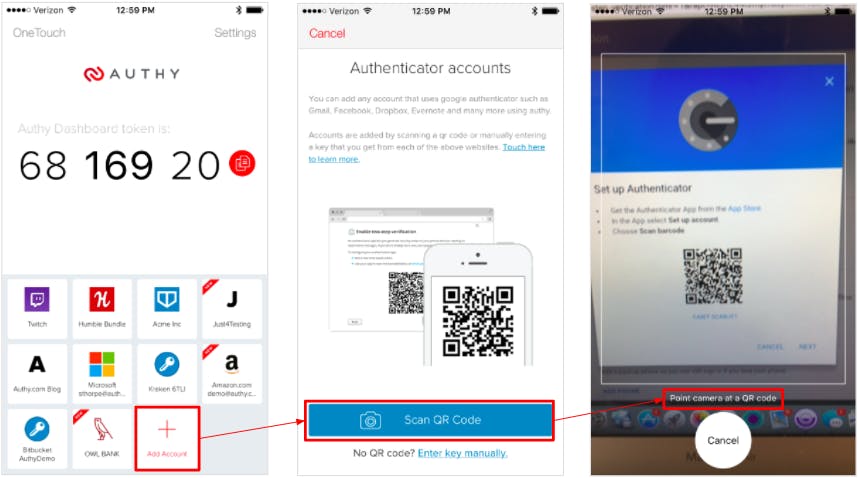
MFA is an authentication system that combines two or more independent credentials: what the user knows, what they have, and what they are. It’s goal is to create more barriers and make it more difficult for unauthorized parties to access a target.
Sometimes, the MFA functions use text messages and emails to send authentication codes, but in most cases, it uses an authenticator app to facilitate the process. Examples of authenticator apps include Google Authenticator and Authy.
Avoid using public wifi, if possible. Take precautions if you need to.
Public, unsecured WiFi is a hacker’s goldmine. One can simply sit between you and the rest of the network (figuratively speaking) and simply watch and observe what you send and what you receive.
If your work simply could not wait, it’s vital to take precautions. Do not transact with personally identifiable information (PII) or any confidential information when on public wifi. If you have access to a virtual private network (VPN), connect through your VPN,
Use HTTPS whenever you can.
When browsing the web, ensure that you enable the "Always Use HTTPS" option on websites that you visit frequently, especially any and all sites that require you to enter any type of credentials. For those pesky websites that are still on HTTP, install the HTTPS Everywhere extension, which rewrites requests to many sites to HTTPS.
Sign out after every session.
This is especially vital when using your credentials on a public place. Don’t rely on the browser signing you out when you close the window. Click the sign out option.
Stay on top of those updates.
It’s tempting to forego updating software, especially if it involves restarts or lots of usability changes that could mean relearning how to use a particular program all over again. But updates also frequently contain security hotfixes that patch vulnerabilities that can allow an attacker an opportunity to get inside, so it’s better to make sure your OS and applications are up to date..
Call for backup(s).
Regularly back your important data up on a regular basis. At the very least if an attack or any unforeseen incident happens, it will only set you back a few days or even hours worth of work (depending on how often you backup).