Introduction
In a recent article we asked What Is Ransomware?What Is Ransomware? In summary, it's a relatively modern cyber threat that strikes fear into the heart of IT professionals all over the globe — thanks to its ability to encrypt an entire computer file system rendering it useless unless a hefty fee is paid to the criminals. In this article, we will be discussing a handful of simple best practices that could help an individual or organization prevent and detect ransomware before it's too late.
The Foundation
Before we consider how to detect and stop a ransomware attack, we must first understand its mechanics. How does it work exactly?How does it work exactly? Although there are many strains many strains, their core functionality remains the same:
- Infect a system
- Encrypt files
- Display a ransom note explaining how fees can be paid to decrypt files
These three steps are a simplification of the process, but an important simplification to make because they are in fact crucial for the cybersecurity defender as they actually offer opportunities for detection. If we look closer at each stage of the MITRE ATT&CK framework, we can find these opportunities.
Opportunities Hiding in Plain Sight.
It's best to start from the beginning so we should first analyze the common techniques found in TA0001 Initial Access. Ransomware, like most malware, are commonly delivered via the following vectors
- T1566 Phishing – The number one delivery for ransomware infections referring to a malicious document containing a macro or Dynamic Data Exchange (DDE) code.
- T1189 Drive-by Compromise – While there are many definitions of this technique, the focus will be on Drive-by downloads. An attacker would drive the target to a fake or compromised website, which would attempt to download and execute the malware.
- T1133 External Remote Services – Attackers use Remote Desktop Protocol (RDP) and exploit weak passwords to gain access to computer networks from the outside — no fancy hacking required. Just connecting to the server as administrator and deploying ransomware on the victims' network, as popularized recently by Ryuk.
Scenario One: Phishing
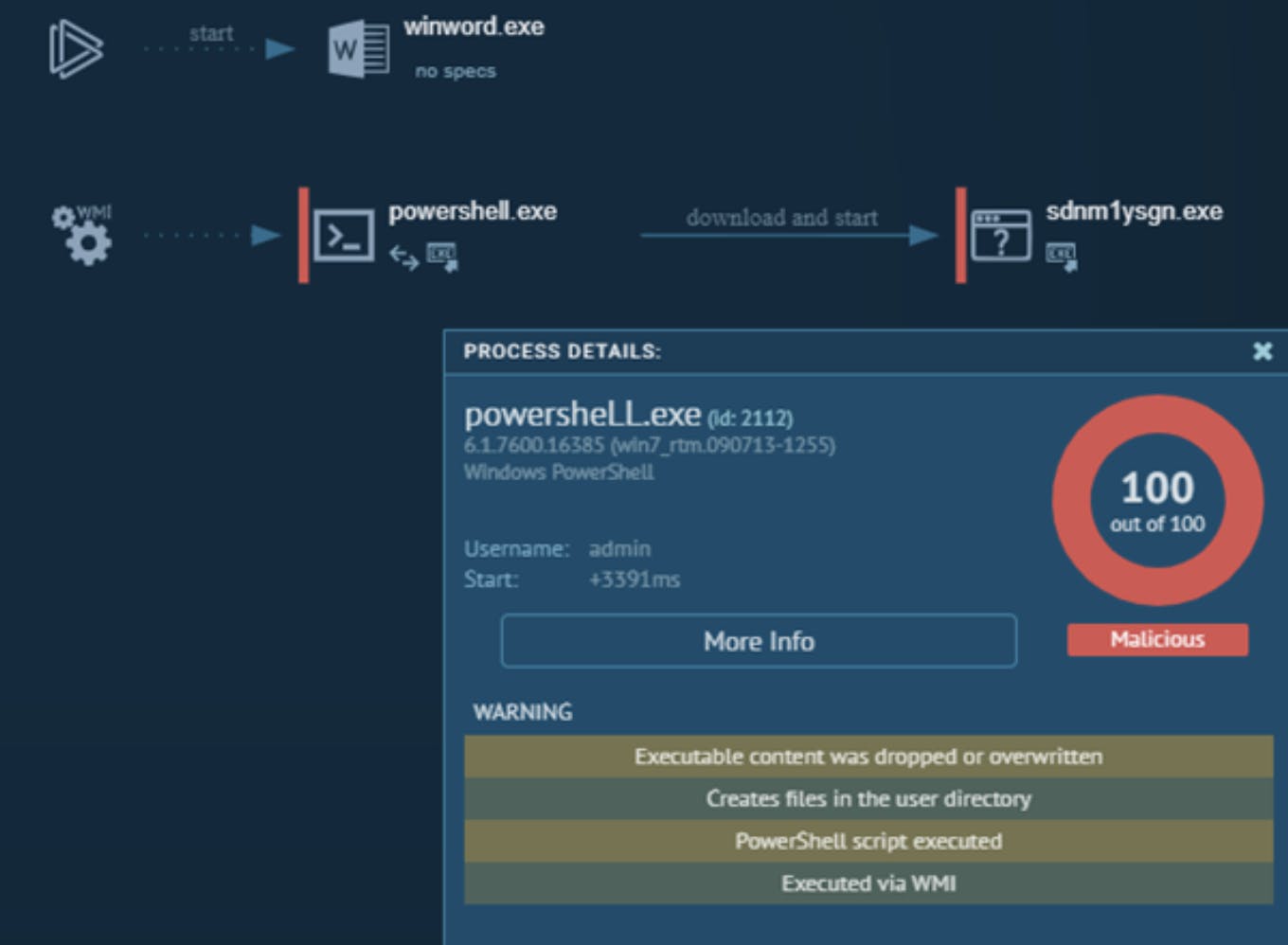
Firstly, let's examine the most popular method of delivery, phishing. Ransomware can be delivered via malicious office files cloaked as business documents. The office files can contain macros or DDE code which often download a stager and execute a payload. In this sample of Emotet, we see winword.exe has a macro containing obfuscated VBA. Running this in a sandbox environment shows that it uses WMI to start PowerShell which in turn downloads and executes the Emotet malware.
Scenario Two: Drive-by Compromise
In the recent Garmin Attack, victims would visit a compromised site presented with fake Google Updates downloading a SocGolish zip malware. Within the zip file contains a JS file which calls wscript and performs reconnaissance and runs a PowerShell loader to inject a Cobalt Strike beacon. The beacon makes use of the Donut project to create independent shellcode from VBScript, JScript, EXE, DLL files and .NET assemblies. The malware also attempts to run lateral movement tools such as PsExec and WMI, along with post exploitation attacks such as removing logs and shadow copies.
Scenario Two: Drive-by Compromise
In the recent Garmin Attack, victims would visit a compromised site presented with fake Google Updates downloading a SocGolish zip malware. Within the zip file contains a JS file which calls wscript and performs reconnaissance and runs a PowerShell loader to inject a Cobalt Strike beacon. The beacon makes use of the Donut project to create independent shellcode from VBScript, JScript, EXE, DLL files and .NET assemblies. The malware also attempts to run lateral movement tools such as PsExec and WMI, along with post exploitation attacks such as removing logs and shadow copies.
Scenario Three: External Remote Services
Recently there has been an uptick in human-operated ransomware deployments that abuse simple security holes in the form of open remote desktop connections and other permissive network controls. System administrators can take advantage of vulnerability scanners or other network probing tools like Shodan to help paint a picture of their external façade. Doing so will help illuminate soft spots like servers with remote access, missing patches and weak passwords that are exposed to the internet and therefore an attack. If an attacker is successful, they could use this vulnerable server as a stepping stone to infiltrate deeper into the network. These tactics have most recently been showcased by the Ryuk campaign.
Defensive Controls
So what detection opportunities can we draw from each of these attack vectors?
Preventative Control 1 – Email Filtering
Most email gateways can be configured to tightly control which attachment types are allowed through. Blocking or at least holding potentially malicious attachments types will reinforce your ransomware controls by halting delivery altogether. Email gateways will be unable to scan encrypted documents and containers (.zip, .7z, .rar, .tar.gz, .tar, .gz). Macro file types to consider filtering out:
- .docm
- .xlsm
- .pptm
- .dotm
- .xltm
- .potm
- .xlm
- .xlam
- .ppsm
- .sldm
Other files types:
- .hta
- .vbs
- .xml
- .js
- .com
- .bat
- .exe
- .pif
- .scr
- .msi
- .ps1
- .jar
- .sh
- .py
- .dmg
Preventative Control 2 – Macro Control
If macros are not a business requirement, then disable them across Office applications, and ensure users cannot re-enable them. This can be configured through Group Policies for Windows or a Mobile Device Management (MDM) for macOS.
If parts of the organisation still need them, then consider reviewing this control and disable where they are not needed. Where they are needed, then follow these recommendations:
- Configure Windows Defender Exploit Guard Attack Surface Reduction (ASR) to run in audit mode. Consider enabling and blocking content with the rules listed here.
- Allow macro from a trusted source or location.
undefinedundefinedundefined
Note that macOS can only enable or block macros. Other security settings can be controlled in com.microsoft.office.
Preventative Control 3 – Endpoint and Network Security
Recently, the term Endpoint Detection Platform (EDR) and Endpoint Protection Platform (EPP) has evolved from traditional AV into a more advanced, comprehensive system. An EDR can provide malware detection with AV/NGAV, manage policies, application control, cloud protection, data encryption, firewall control, process monitoring, and signature and behaviour detections.
A great feature of an EDR is the ability to detect suspicious parent-child relationships. We know that macros call on other system utilities to do their dirty work so monitoring such behaviour often provides high fidelity alerts from security telemetry. We often see winword.exe being the parent process to system utilities like PowerShell, CertUtil and WMI. Most EDR solutions should be able to spot this suspicious parent-child relationship a mile away and should be configured as such. But what happens if it utilizes another system utility to call the process. In our previous example, Emotet avoided this parent-child relationship by using WMI to call PowerShell. When we decode the PowerShell command, we find Emotet uses more obfuscated PowerShell code to perform a DownloadFile to write a malware on-disk. This is an artifact and a well-known behaviour that can be detected by an EDR which did not exist for traditional AVs.
Other features for ransomware detection include process monitoring, arguments monitoring for raw and obfuscated script, userland API hooking on common functions in Windows DLL, and more.
If the ransomware could not be detected by the endpoint security, then Intrusion Detection/Prevention Systems (IDS/IPS) and Security Information Event Managers (SIEM) can play a huge role in detecting and even stopping the spread of the infection. Many of these technologies now come with HTTPS inspection that can be used to detect malicious domains, unusual traffic and perform content inspection. HTTPS inspection can prevent the drive-by downloads attack by analyzing the domain reputation and content for malicious behaviour. These can work at the Network and Transport layer such as IP, ICMP, TCP and UDP to the Application layer such as DNS, SMB, FTP, and SSH. SMB is commonly used in a Windows environment, if a ransomware attempts to infect shared drives or attack neighbouring and public SMB ports, notoriously used in WannaCry, this can be detected with an IDS/IPS/SIEM.
Preventative Control 4 – Harden Build
Another preventative measure is to harden the builds against a security baseline consisting of recommendations and best practices. Ultimately, it comes down to the individual organization and the level of risk they are willing to accept. Threat modelling can help in determining the type of threat actors, assets, mitigations, and acceptable risks. Benchmarks such as Microsoft Security baseline and CIS benchmarks are a good start in creating a secure build. In fact, CIS provides further recommendation beyond the operating system on commonly used software such as Office and Chrome.
This is not the end as there are many areas that require special attention such as firewall policies, patching cycle with automatic updates, application whitelisting, password policy, logging, physical protections and more.
For a comprehensive list visit the CIS Benchmarks.
Preventative Control 5 – User Security Awareness training
Moving away from the technical controls, another aspect that should be incorporated within an organization on an ongoing basis is user security awareness training. The reality is that even with all the aforementioned security control, there will still be phishing emails that crawl its way through the defenses or users may inadvertently visit compromised websites and download malware. It is important that staff are educated in identifying suspicious emails or websites and report them to the IT department for investigation in a timely manner.
The following are some indicators of a phishing attack:
- Poor grammar
- Recognizing typosquatting in domains
- Asking for sensitive information or to visit a suspicious domain, especially when it is not owned by the organization
- Urgent actions
- Unexpected emails
- Additional actions such as decrypting the zip file especially when these emails are unexpected, or enabling macro to view the content
Encryption — Is All Lost?
Our final detection opportunity is again sadly when it’s far too late, the encryption phase. At this stage, the attack has taken a firm grip on its target system and started to encrypt or even destroy files. Instead of looking for classic Indicators of Compromise (Ioc) for this infection, we should instead — once again — look for suspicious behaviour. Can any of your tools look for a large volume of file modification events? Often a SIEM and EDRs are capable of doing so. This same mantra should be used throughout our security detection thought process; look for behaviours not fingerprints. We know what a crime looks like but we do not know every criminal’s fingerprint.
For on-prem servers, perform backups and use a physical or cloud-based Disaster Recovery (DR) site. For cloud and virtualized environments, create snapshots and backups. For standard users, Windows has a Ransomware Protection folder feature which can be used to protect changes to certain folders by unauthorized programs. Similarly, shadow copies can be used to create full backups. Equivalently, macOS has time machines to do this. However, if a ransomware were to obtain administrative privileges, they could render this obsolete as it can just remove the backup copies! Depending on the level of security, consider performing cloud backups or copy to a NAS server.
Start With Education & Regulation
Oftentimes, having the necessary cyber hygiene will reduce your organization’s cyber risk significantly. And it is consistent with what we preach to our customers. Horangi conducts Security Awareness Training and helps organizations to create ransomware prevention and incident response policies that have organization-wide benefits.
Begin building true Defense in Depth today against bad actors and malicious insiders.




