This is a co-written blog post with CardUp.
Across the world, many countries are opening back up their borders and most of us enter into the ‘new normal’‘new normal’ way of life. However, some countries are once again activating their lockdown procedures as new cases of COVID-19 arise. Businesses can maintain their continuity despite the continued uncertainty by cultivating a remote workforce. But how do you kickstart this cultivation? What operational and security considerationsoperational and security considerations should be taken into account? And how can a remote working culture be secured-by-design?
The importance of maintaining social distancing as part of countermeasures against the COVID-19 pandemic has been a consistent trend across the globe, critical in limiting the rate of infections. However, this has had adverse effects on businesses across many sectors, with Travel, Hospitality and Retail badly affected by the global restrictions over the past few months. As a result, businesses in today’s post-pandemic economy now face immense cash flow pressure from both low inflows (reduced sales and increased number of late payments) and high outflows (high overheads such as rent, payroll). Cash flow management has thus also become one of the most important topics in the world now amongst business leaders, with many understanding that business recovery is beyond just surviving, but adapting and learning from this crisis.
However, the gradual decrease in numbers has allowed partial reopening of public and office spaces, albeit operating under strict social distancing and sanitation requirements. In some countries, some businesses are able to return to normal but only to be closed again due to new waves of infections. This uncertainty has led to many emptied office spaces and becoming, in some cases, an expensive financial blackhole.
The simple, cost-saving solution is thus to go remote.
Across the world, not all services are reopened. But services that will result in the congregation of people, like restaurants and retail stores, are required to implement strict social distancing and sanitation countermeasures. In the Republic of Singapore, where Horangi and CardUp are headquartered by the way, businesses who have the capacity to ‘go remote’ are nonetheless encouraged to do so. If that’s the case, where do we ‘securely’ start?
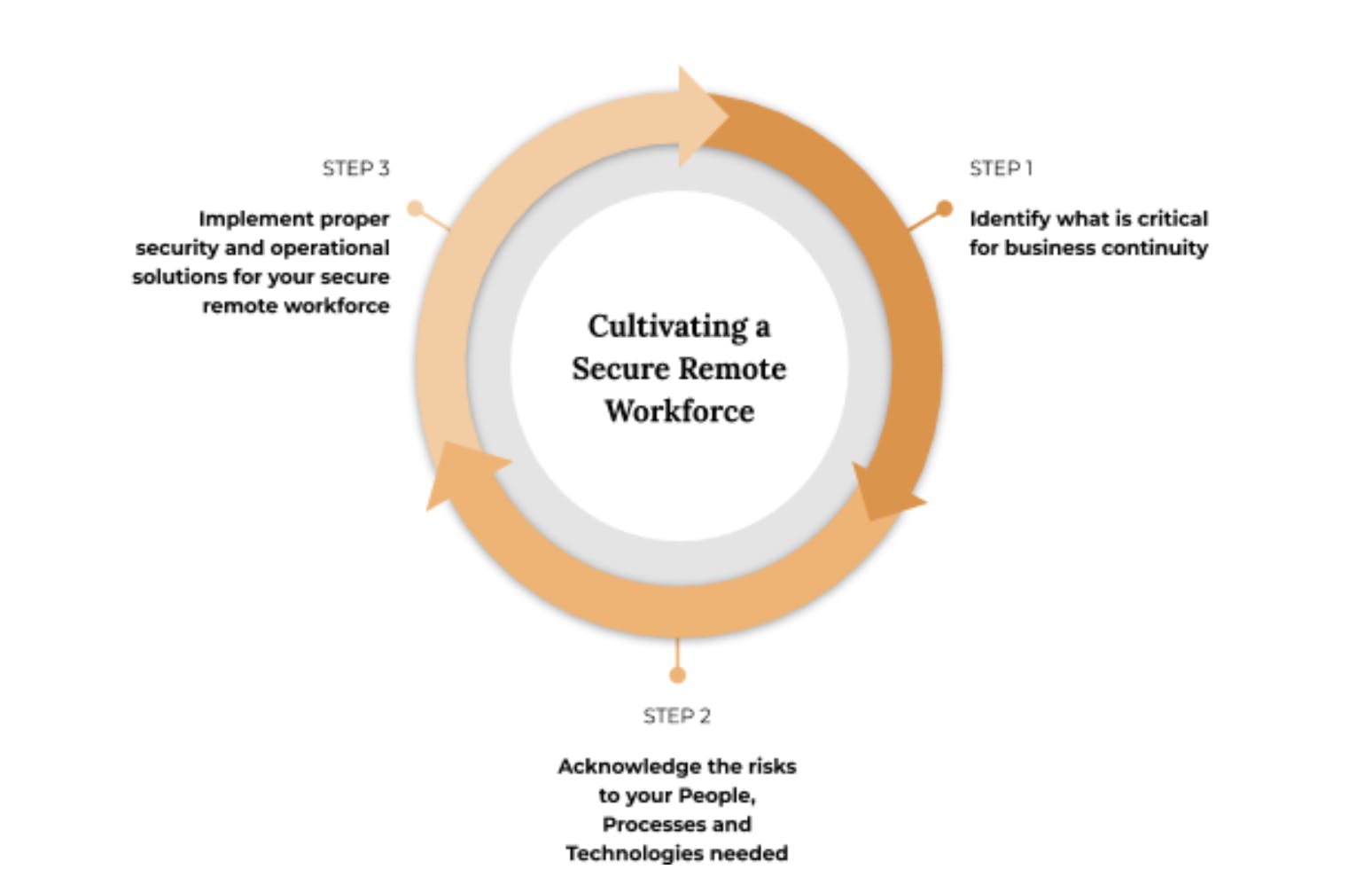
The trick is to identify what is critical to your business continuity, acknowledge the risks associated, and implement proper solutions to continuously mitigate discovered and emerging risks.
STEP 1: IDENTIFY
The first step is to IDENTIFY. As the old saying goes, ‘knowing is half the battle’. And in this case, it is all about being aware of the critical pillars that your company is built on. A simple way to look at this is through the People, Processes, and Technology approach.
To start, gather your executive and managerial teams and ask these questions in the table below - alongside their objectives and bonus security benefits.
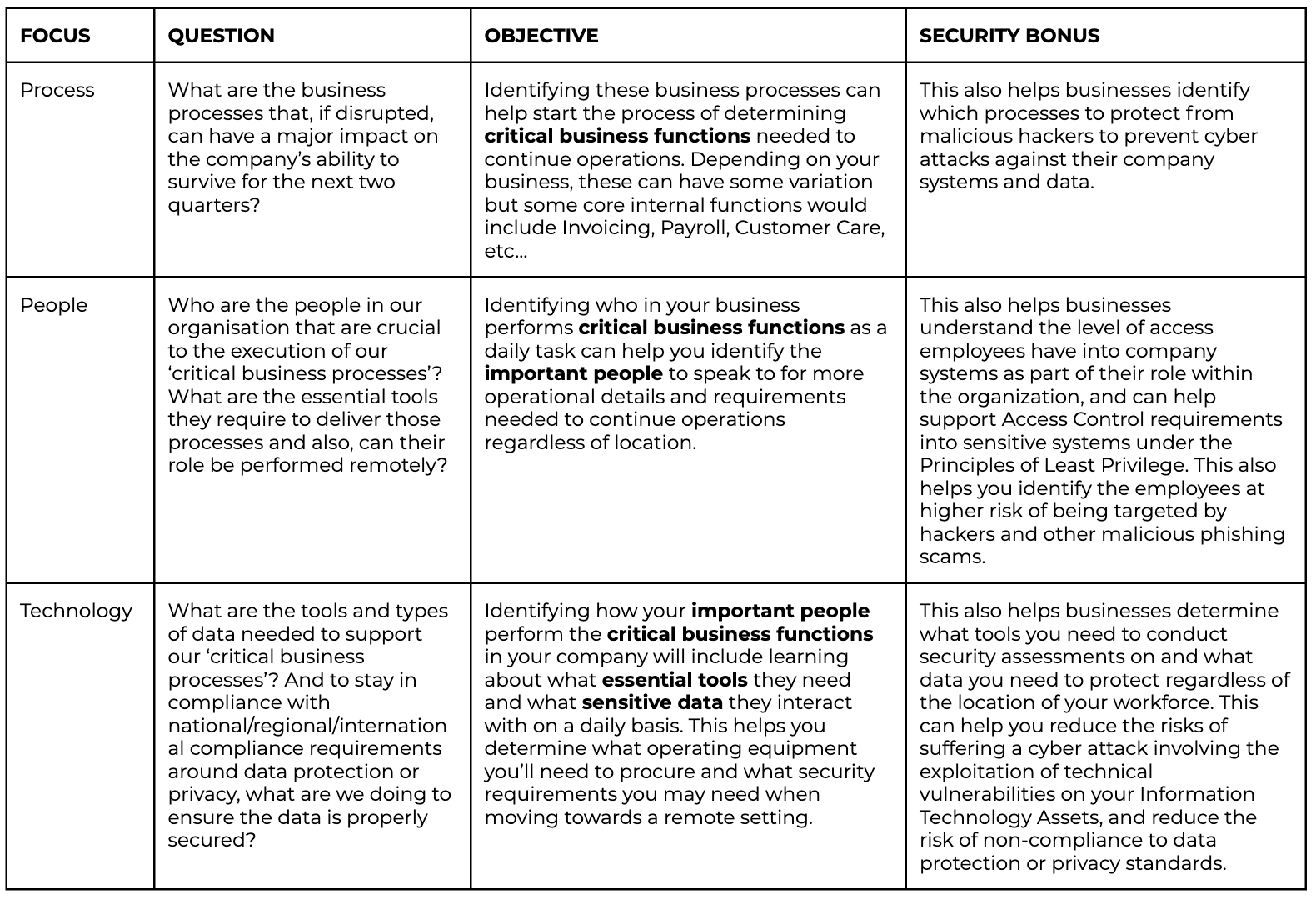
What these questions do is identify your Critical Functions, Important People, Essential Tools and Sensitive Data needed to maintain business continuity in any circumstance. You can collect most of this information by simply talking to your staff. The finance department, for instance, typically receives more phishing emails than other departments. How will the shift to remote work affect the risk posture of such teams? There are also many processes that can be shifted completely online, improving not just the efficiency of how things are done, but also fully embracing this shift to remote working.
Alternatively, you can:
- Conduct Business Impact Analysis to determine the business critical processes. This is usually performed as part of a broader Business Continuity Preparedness and supplements the development of a Business Continuity Strategy and accompanying plans. For more information, take a look at ISO 22301 – Business Continuity for an internationally recognized standard on business continuity best practices.
- Performing Data Discovery Exercises either through employee interviews or conducting technical reviews can help you determine what types of data flow throughout your business. This is where an updated Network Diagram, Logical Data Flow Map and Workflow Diagrams come in very handy. If you haven’t updated or created one, start now. Alternatively, you can also use different Endpoint Scanners to help you gain a better understanding of your technological footprint and layout. What connections are flowing into and around your organization? Where do those connections go? Employing Endpoint Scanners, Traffic Monitoring and Security Incident and Event Management (SIEM) tools can help you map out your digital kingdom.
- To determine what Information Technology (IT) Assets your company owns, review your Inventory Lists. If you don’t have one, consider starting one. Not only is this a requirement under different security standards such as ISO 27001 and NIST 800-53, it’s also good practice to know what you’ve spent your revenue on.
And as with all the questions recommended, the added security bonus is that you’re now more aware of what data, technologies, processes and people to secure as part of your cybersecurity program!
STEP 2: ACKNOWLEDGE
The second step is to ACKNOWLEDGE. Knowing what you need is not enough, you need to also be truly aware of the security and operational risks associated. And by ‘truly aware’ ‘truly aware’ we mean cataloguing the risks with proper metrics to help you manage it later on. Then, and only then, can you claim to acknowledge the risks to your Company and continue with implementing solutions to mitigate them.
A simple means of acknowledging these risks is to collate them into one place using a Risk Register. A risk register is a document used as a risk management tool and acts as a repository for all risks identified with additional information about each risk (ie. nature of the risk, reference and owner, mitigation measures). This may seem daunting, but it can be as simple as an Excel spreadsheet.
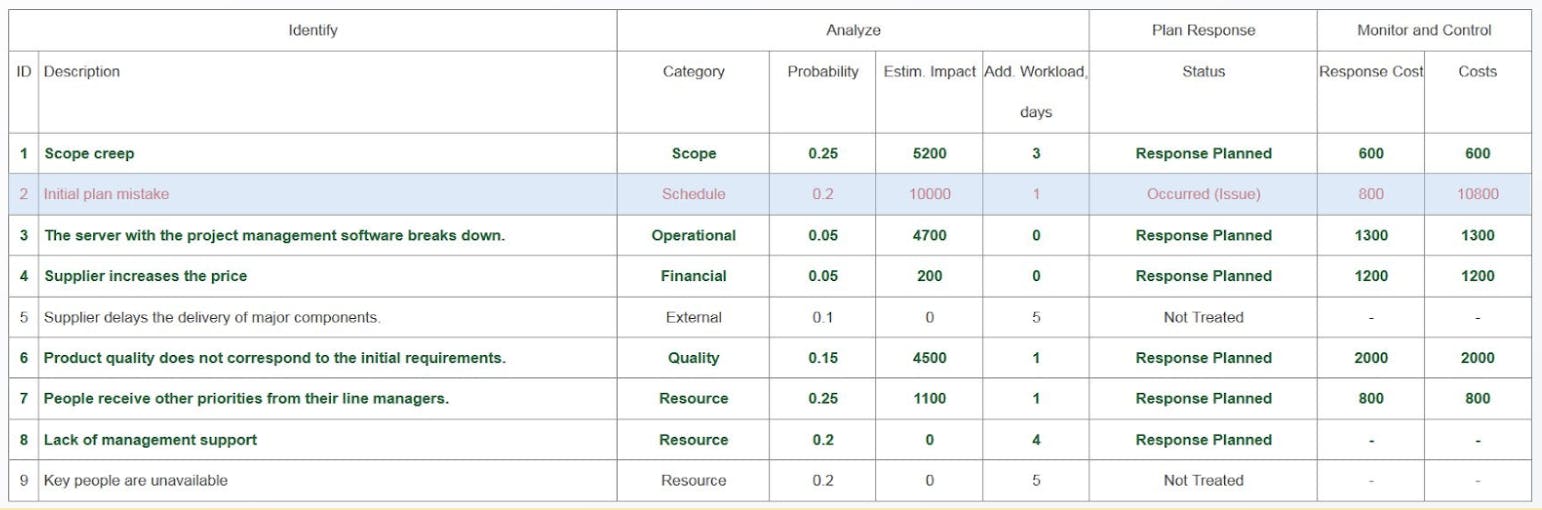
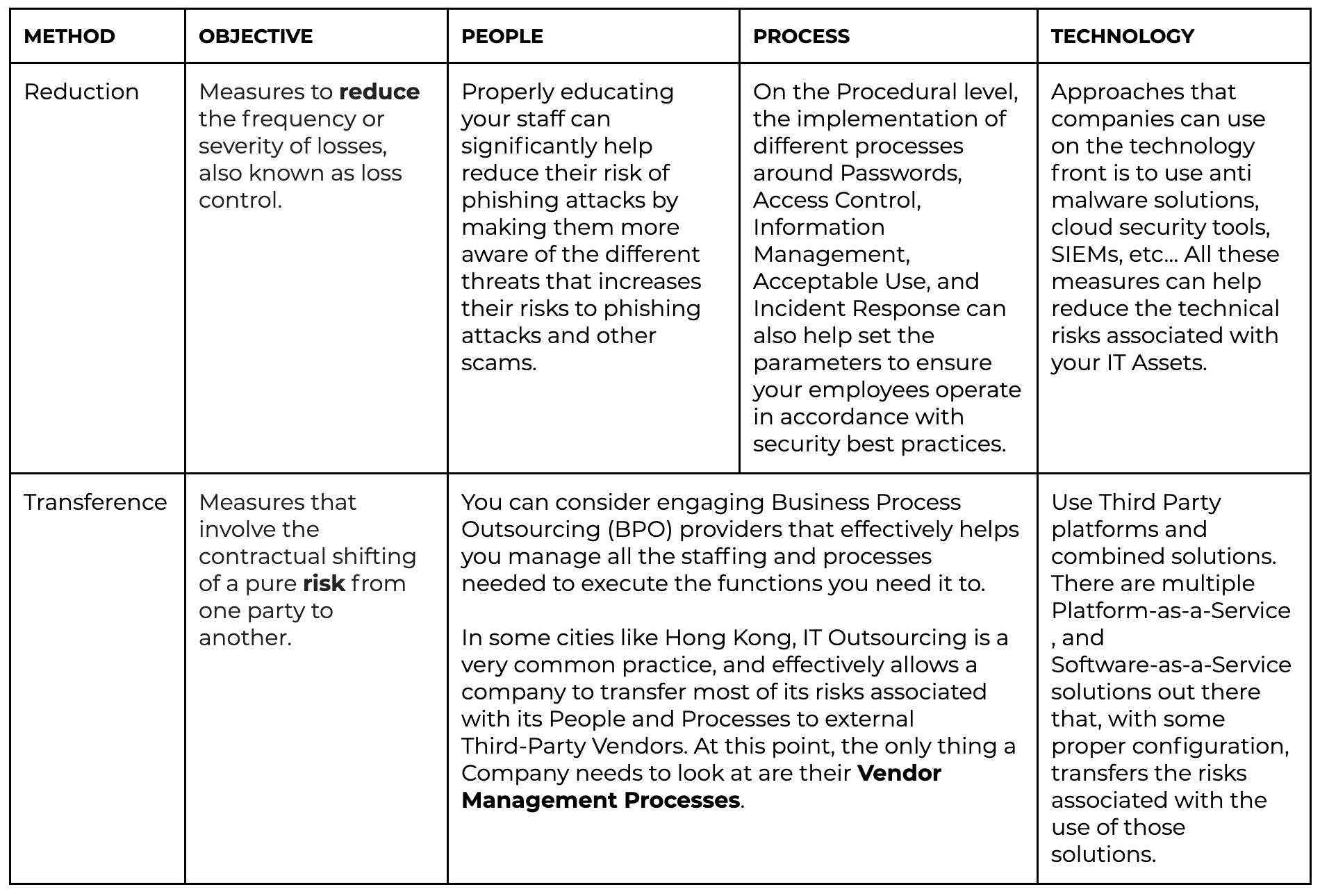
The value of creating and maintaining a risk register is to become more aware of the potential negative events that can occur. Within the context of cultivating a remote workforce, this tool will be very useful in helping you determine the reality of threats against your business and what actions can be taken to reduce their impact, be they security or cash flow-related. When looking to risk mitigation, there really are just two ways. You either reduce it or transfer it. We’ve created a simple table below to help you understand what these mean.
STEP 3: IMPLEMENT
The third step is to IMPLEMENT. Now that you know what you need and the risks against them, you now need to put this information into action and start the cultivation of your remote workforce.
At this point we have identified which processes can be performed remotely and which processes cannot. We would’ve determined the mandatory requirements of your local government on Remote Operations from cybersecurity, insurance, employee rights, data privacy and anti-COVID standpoints. We should have also identified the IT Assets, both Hardware and Software your employees need to execute their tasks, in addition to the risks associated with each process and technology. Along with these identified risks, we should have a list of risk mitigation measures with accompanying tools and/or processes.
The last step is to implement these security solutions and processes you need to protect your assets and employees when they are out of the office. Depending on your budget and other resources (ie. Specialists), it would be a smart move to prioritize tasks based on their security and operational importance using the simple table below to help you add some metrics to determine what should come first.
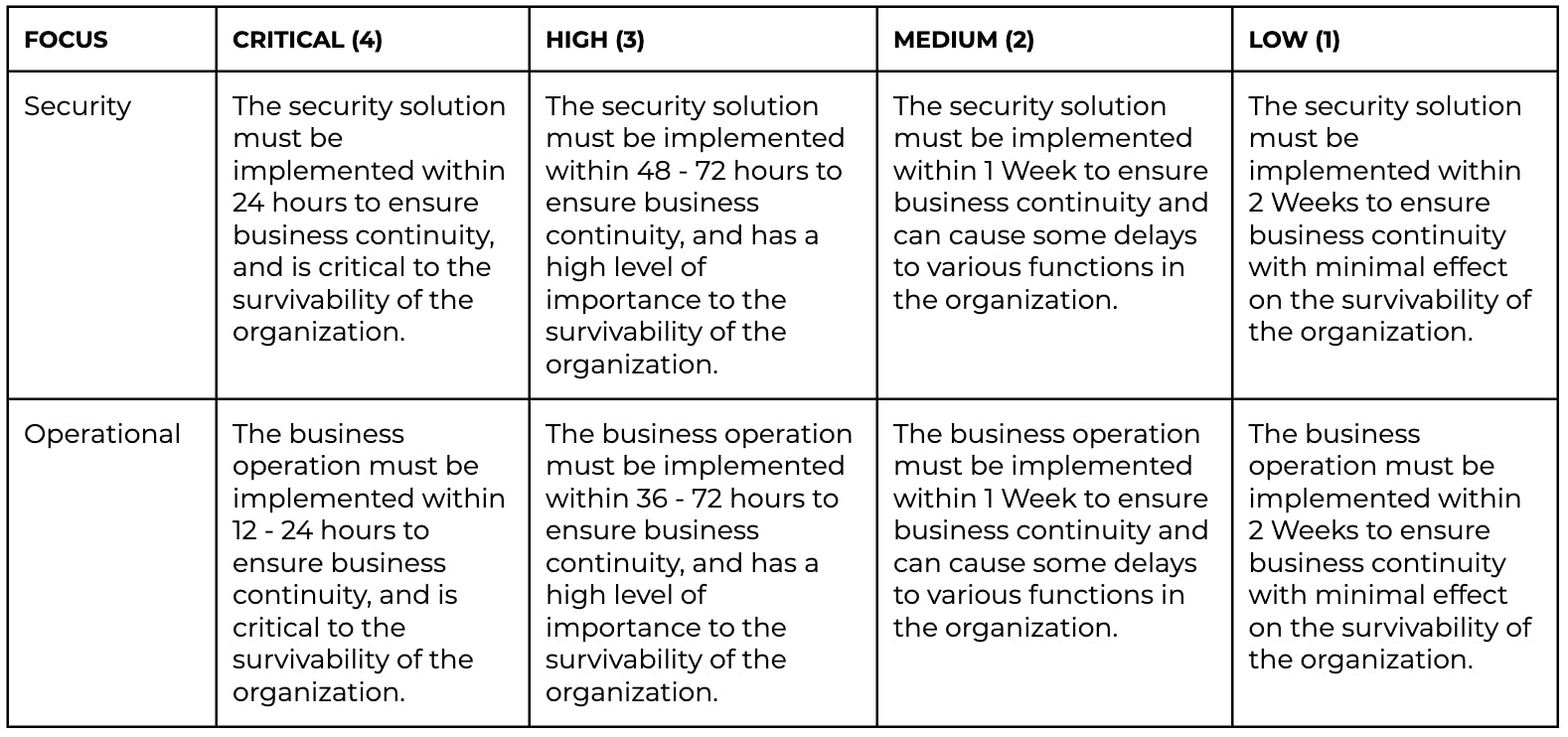
The value of security importance + operational importance is a simple formula you can use to help place some metrics around the prioritization of tasks based on their importance. The timings and metrics we’ve suggested are estimates, and can be adjusted based on your realities for implementation.
Maintaining Remote Security
After determining who and how your employees are to work remotely, you also need to ensure that they follow procedure. Depending on how your organization is run, and the leadership culture, you can choose to set up different countermeasures that can help secure your remote teams. Using the People, Processes and Technologies approach, there is a lot that companies can do to secure their remote workforce while maintaining productivity levels.

Secure Your Start to Secure Your Future
Here, we’ve only just scratched the surface of what it means to cultivate a secure and remote workforcecultivate a secure and remote workforce. Using the 3-step cycle we’ve shown you, you should be able to get a good start on learning more about your organization and acquiring the right tools to properly secure your organization. For more information on what tools you can use really depends on how you want to migrate your IT assets and the nature of your business.
But remember, going remote securely is NOT a one-and-done. It's a continuous process that you should review on a regular basis once started to ensure that your remote workforce is properly protected.
CardUp is increasing support for businesses affected by COVID-19. Get lowered fees starting at 0.8% (u.p. 2.6%) on your rental and 1.45% on your payroll, supplier invoice and business tax payments. These support initiatives will help businesses with cash flow, and allow them to tide through this period of time. Learn more here.




