What is UEBA and why do you need it?
Getting breached is a nightmare scenario, and most organizations put smart people and technologies to work as a defensive barrier against hackers. But cloud security is an ongoing process—not a guarantee. Within the context of an organization's security program, the concept of "threat detection" is multifaceted. Even the best security programs must plan for worst-case scenarios, when someone or something has slipped past their defensive and preventative technologies and becomes a threat. This can become less hasslesome with UEBA.
UEBA stands for User and Entity Behavior Analytics. It analyzes various behavior patterns with large amounts of data within a sufficient time period to understand normal user behavior. And by defining these baselines, it can identify suspicious behavior, potential threats, and attacks that traditional methods may not detect. The key thing in UEBA is it identifies anomalous activities by looking at context information from a series of activities and establishing correlation between them.
Warden Threat Detection analyzes logs from your infrastructure to perform UEBA to detect anomalies after learning the normal behavior of the users in the organization. It establishes a baseline for each organization or each user based on their previous activity patterns. It can detect any anomalous behavior when there are deviations from these “normal baseline” patterns. It can be due to a credential compromise, cryptojaking, or an early sign of insider threats.
Anomaly Detection with UEBA
Case 1: Detect unusual user access from new geolocation
It is possible that the attacker may not always use malicious sources to get into infrastructure, then the attack may not be flagged by the normal malicious detector. However, with UEBA, Warden could observe every single user in the organization and establish baselines for each user who is accessing your infrastructure and identify anomalous user behavior.
For example, an identity (credential) used by an engineer is always connecting from Singapore in the last 30 days, but all of a sudden the user accessed it from Russia, which is suspicious enough to be flagged and investigated. Once you get the alert, it will elaborate on why this activity was flagged as an anomaly and provides summarized context to help you take action. On your dashboard you can also see a graphical visualization for further investigation on all activities from that specific identity.
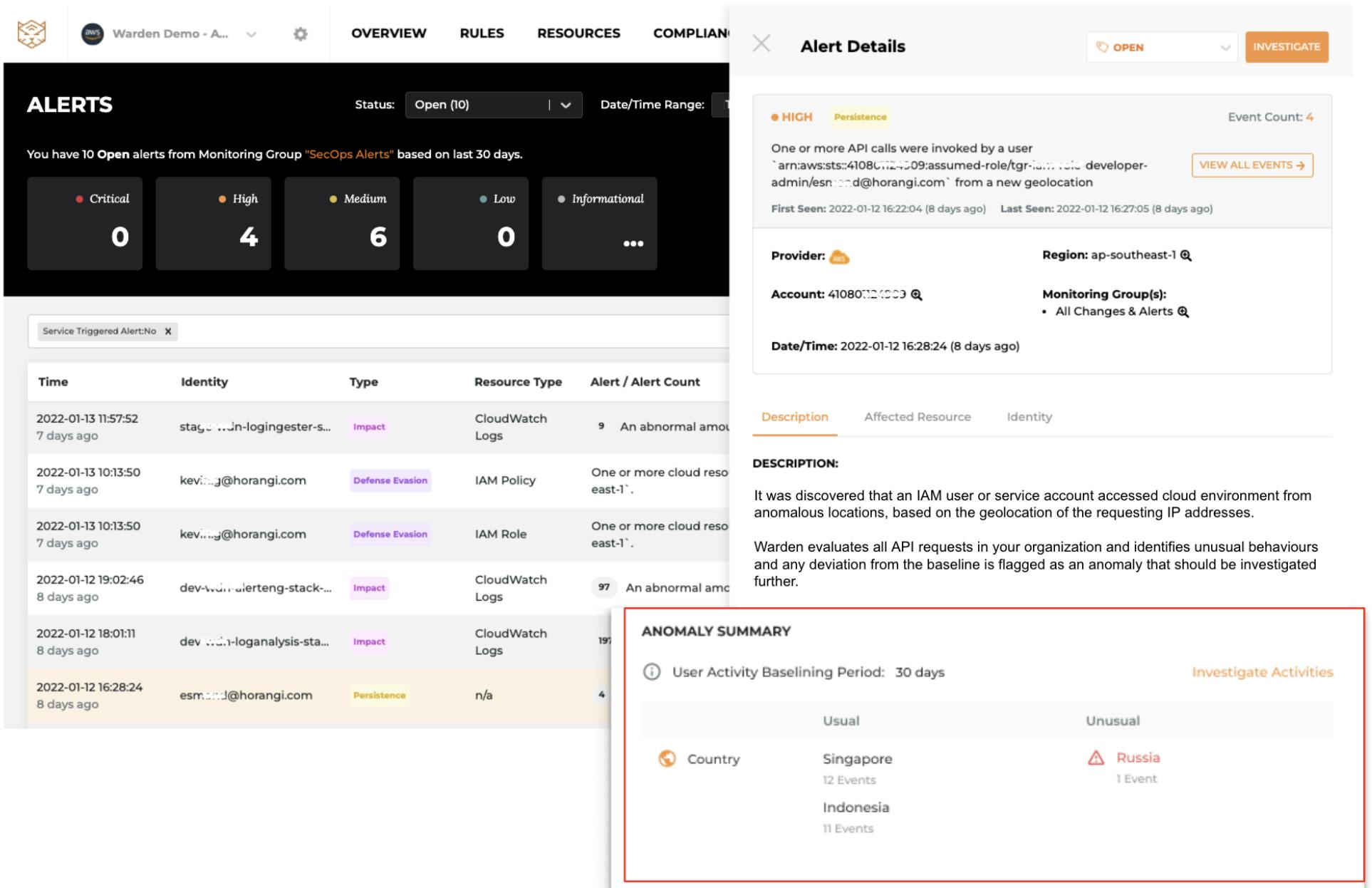
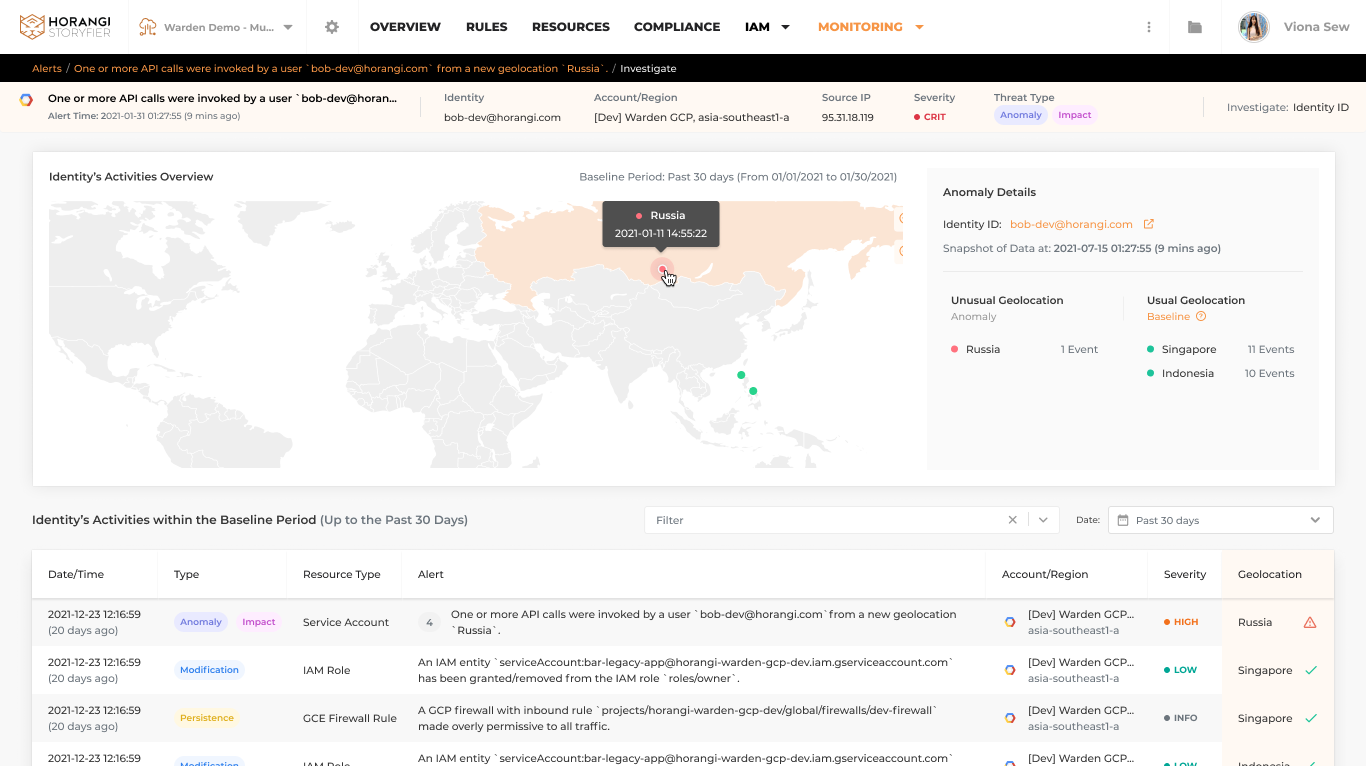
Pro Tip: A great thing with Warden UEBA is that it can automatically adjust the baseline of individual users with their latest patterns instead of a one-size fits all approach. Thus, if the user relocates to a new country, it will consider it as a new normal after gathering sufficient baseline data and will automatically eliminate the false alarm.
Case 2: Detect anomalous resource provision
Cyberattacks towards compromised instances are most common in cloud based infrastructure. According to Google's latest Threat Horizons report, 86% of compromised instances were used for cryptocurrency mining. In crytojacking attacks, miners steal compute resources for cryptocurrency mining, which may cost you billions of dollars if not found out early enough!
Together with threat intelligence source and correlation information, Warden Threat Detection can identify malicious or accidental compute resource provisioning. You can be alerted immediately when a user creates a compute instance in a new region that your organization rarely uses and flag early signs of abnormal number of instances created in a short period of time which is highlikely a cryptojaking event.
The image below shows an example of anomaly detection on compute instance.
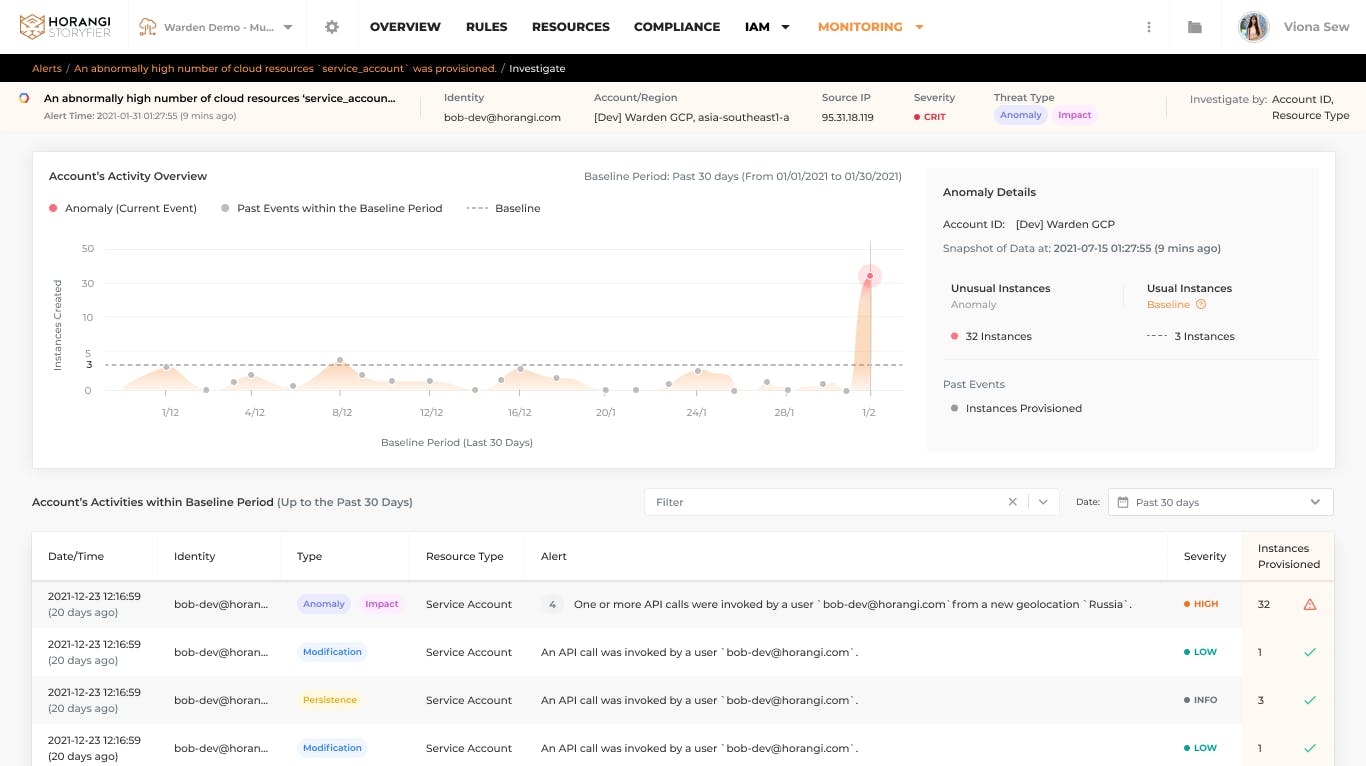
When an attacker starts to spin up compute instances that deviate from the baseline, it is flagged as an anomaly and immediately gets flagged before the attacker might use the credentials to continue this unwanted activity.
Conclusion
In today’s complex threat landscape, an attack is no longer a single malicious action or something that a single threat detector can help flag and protect your infrastructure. The attackers are using more advanced techniques and processes to get into your environment and it can only be flagged by looking at contextual information, using advanced capabilities like UEBA. Warden Threat Detection continuously provides more effective and valuable detection use cases to enhance your company’s overall security posture. If you are curious to see this live in a 15 min demo, drop us a line here.




