Cloud Security
Top Cloud Computing Security Threats To Watch For
Cloud computing provides users the convenience to spin up workloads without dealing with the overhead that comes with maintaining physical infrastructure, driving up adoption rates. With more and more organizations using the cloud in some form or another, it brings along with it a fair share of security threats.
Samantha Cruz . Jun 15 2022

Cloud Security
Top Cloud Computing Security Threats To Watch For
Cloud computing provides users the convenience to spin up workloads without dealing with the overhead that comes with maintaining physical infrastructure, driving up adoption rates. With more and more organizations using the cloud in some form or another, it brings along with it a fair share of security threats.
Samantha Cruz . Jun 15 2022

Cloud Security
Cloud Migration and Security Risks: The Good, the Bad, and the Ugly
With business operations shifting to a distributed, decentralized way of working, the need for organizations to migrate to the cloud has become acute in recent years. Here’s our take on what you need to know as cloud migration becomes the next step to scale your business.
Samantha Cruz . May 6 2021

Cloud Security
Cloud Migration and Security Risks: The Good, the Bad, and the Ugly
With business operations shifting to a distributed, decentralized way of working, the need for organizations to migrate to the cloud has become acute in recent years. Here’s our take on what you need to know as cloud migration becomes the next step to scale your business.
Samantha Cruz . May 6 2021

Cloud Security
Top 5 Cloud Security Controls You Should Be Using
With cloud environments increasing in size and number and cloud service providers releasing new services and features each year, it pays for organizations to shore up their cloud defenses with these top cloud security controls.
Samantha Cruz . Feb 22 2021

Cloud Security
Top 5 Cloud Security Controls You Should Be Using
With cloud environments increasing in size and number and cloud service providers releasing new services and features each year, it pays for organizations to shore up their cloud defenses with these top cloud security controls.
Samantha Cruz . Feb 22 2021

Cloud Security
General Data Protection Regulation (GDPR) Compliance: Horangi Warden's Newest Standard
Organizations that need to be compliant to the General Data Protection Regulations (GDPR) can now report on compliance posture in just one click.
Samantha Cruz . Feb 8 2021

Cloud Security
General Data Protection Regulation (GDPR) Compliance: Horangi Warden's Newest Standard
Organizations that need to be compliant to the General Data Protection Regulations (GDPR) can now report on compliance posture in just one click.
Samantha Cruz . Feb 8 2021

Cloud Security
One-click Remediation is now available on Horangi Warden!
Warden can now enable even faster reaction times, where failed findings are rectified and remediated swiftly with a single command.
Samantha Cruz . Jan 25 2021

Cloud Security
One-click Remediation is now available on Horangi Warden!
Warden can now enable even faster reaction times, where failed findings are rectified and remediated swiftly with a single command.
Samantha Cruz . Jan 25 2021

Cloud Security
Top 3 GCP Configurations To Watch For
The cost of a security breach can have severe financial and reputation impact. Still, your organizations can avoid mistakes like these by configuring your GCP resources in a way that minimizes your security risks.
Samantha Cruz . Dec 21 2020

Cloud Security
Top 3 GCP Configurations To Watch For
The cost of a security breach can have severe financial and reputation impact. Still, your organizations can avoid mistakes like these by configuring your GCP resources in a way that minimizes your security risks.
Samantha Cruz . Dec 21 2020

Cloud Security
IaaS vs PaaS vs SaaS: Know Your aaS-es
Whether you’re starting a Cloud-native solution from the ground-up or migrating existing on-premise workloads to the Public Cloud, one crucial decision to make is what cloud delivery model you want to use for your organization.
Samantha Cruz . Dec 14 2020

Cloud Security
IaaS vs PaaS vs SaaS: Know Your aaS-es
Whether you’re starting a Cloud-native solution from the ground-up or migrating existing on-premise workloads to the Public Cloud, one crucial decision to make is what cloud delivery model you want to use for your organization.
Samantha Cruz . Dec 14 2020

Compliance
Ensuring Continuous Cloud Compliance with ISO 27001
Continuous compliance isn’t just ticking all checkboxes on a list. It’s a conscious building of a business culture that continuously monitors compliance posture. What are the sections that apply to the cloud?
Samantha Cruz . Jul 27 2020

Compliance
Ensuring Continuous Cloud Compliance with ISO 27001
Continuous compliance isn’t just ticking all checkboxes on a list. It’s a conscious building of a business culture that continuously monitors compliance posture. What are the sections that apply to the cloud?
Samantha Cruz . Jul 27 2020

Cloud Security
Unboxing CSPM As The Answer To IaaS Security Risks
With more organizations migrating to the cloud, the risks stemming from misconfiguration and rapid scaling increases along with it. How do CSPMs help address these cloud security risks?
Samantha Cruz . Jun 22 2020

Cloud Security
Unboxing CSPM As The Answer To IaaS Security Risks
With more organizations migrating to the cloud, the risks stemming from misconfiguration and rapid scaling increases along with it. How do CSPMs help address these cloud security risks?
Samantha Cruz . Jun 22 2020

Cloud Security
13 Compliance Frameworks For Cloud-Based Organizations
The need for cloud compliance begins as soon as you build on the cloud. Considering the shared responsibility of cloud security, which are the regulatory frameworks that you need to be aware of?
Samantha Cruz . May 15 2020

Cloud Security
13 Compliance Frameworks For Cloud-Based Organizations
The need for cloud compliance begins as soon as you build on the cloud. Considering the shared responsibility of cloud security, which are the regulatory frameworks that you need to be aware of?
Samantha Cruz . May 15 2020

Release Notes
Release Notes Jan 2020: New Compliance Standards Supported
We previously released new features to drive automated cloud compliance on Warden. This time, we added two new compliance standards and more ways to action on compliance check results.
Samantha Cruz . Jan 31 2020
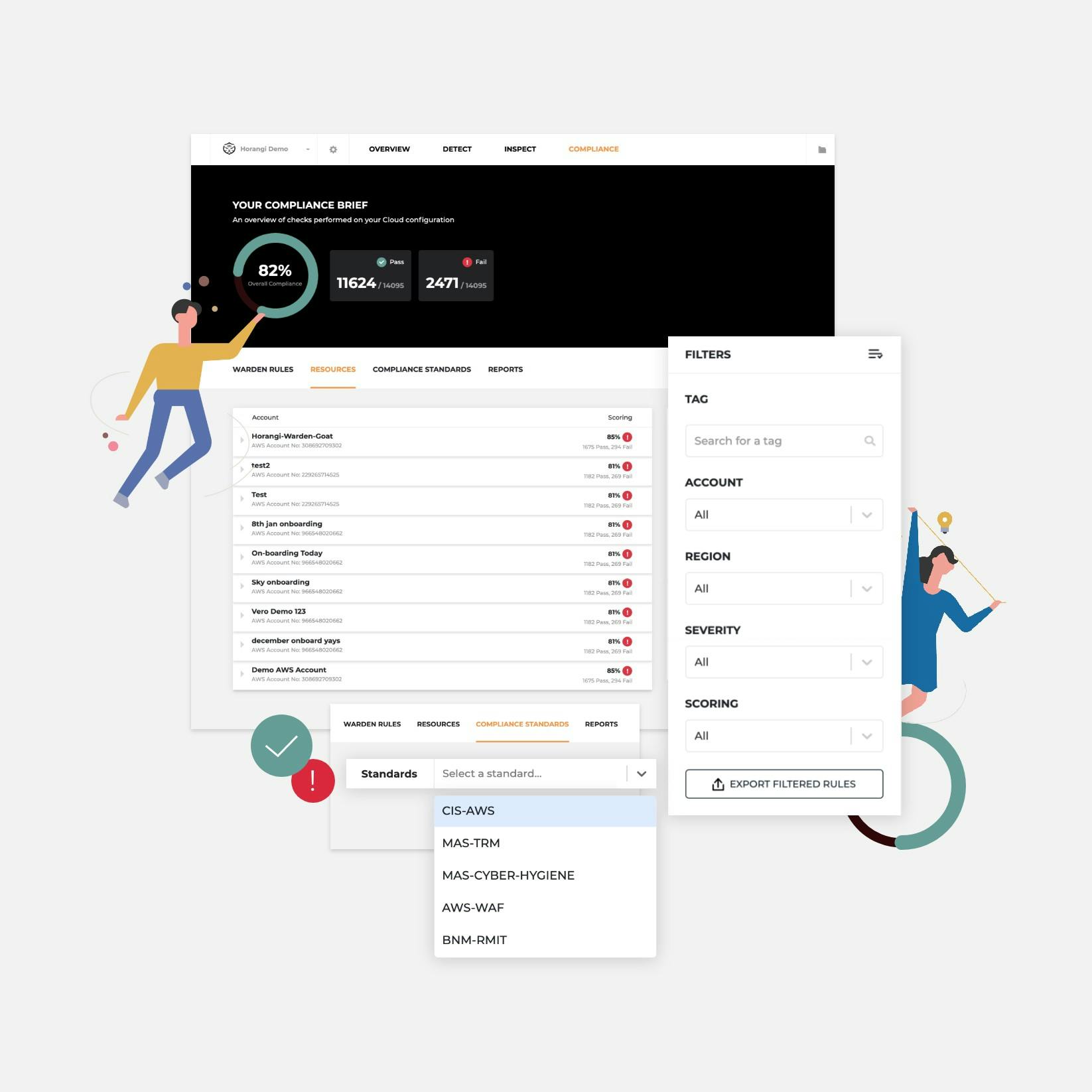
Release Notes
Release Notes Jan 2020: New Compliance Standards Supported
We previously released new features to drive automated cloud compliance on Warden. This time, we added two new compliance standards and more ways to action on compliance check results.
Samantha Cruz . Jan 31 2020

Release Notes
Release Notes Nov 2019: Compliance Now Supported
We’re excited to tell you about a new set of features to help you with compliance. Also in this release are the ability to manage vulnerabilities in bulk and export findings.
Samantha Cruz . Nov 22 2019
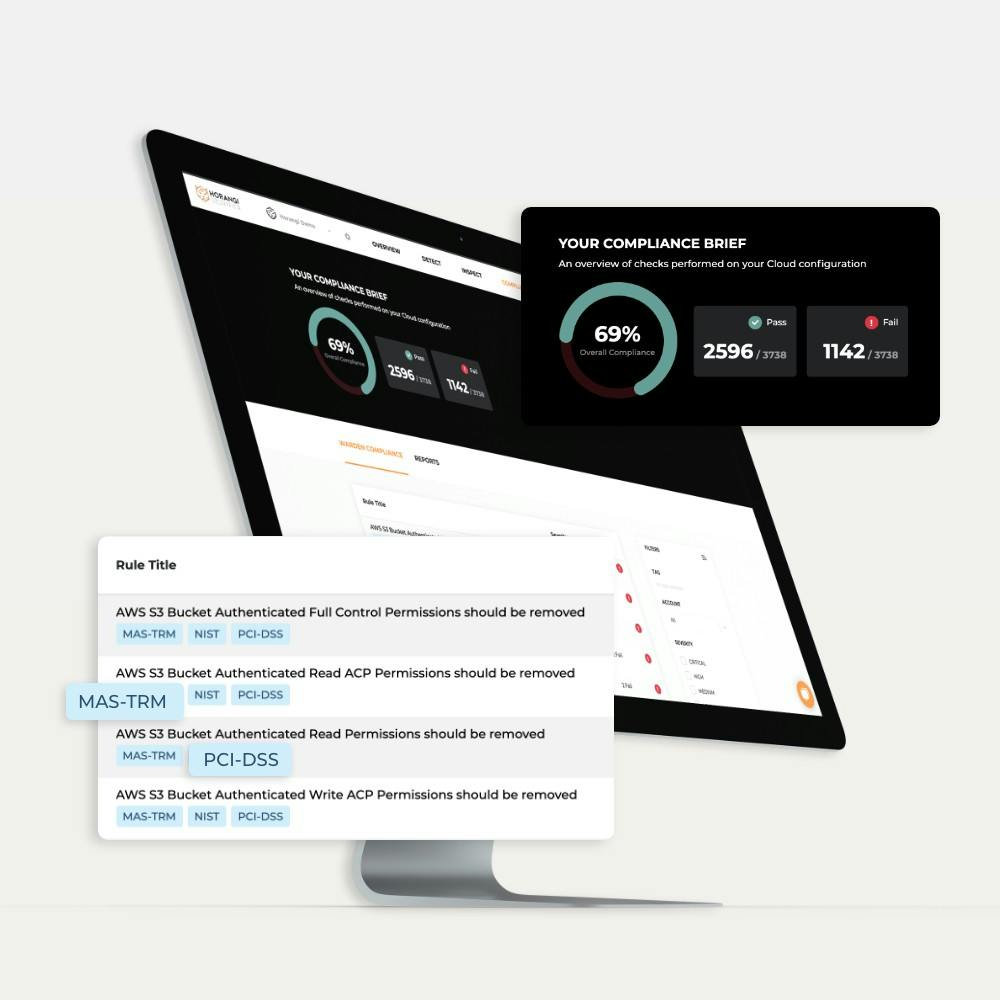
Release Notes
Release Notes Nov 2019: Compliance Now Supported
We’re excited to tell you about a new set of features to help you with compliance. Also in this release are the ability to manage vulnerabilities in bulk and export findings.
Samantha Cruz . Nov 22 2019

Compliance
The Real Cost of Cloud Compliance (or Lack of It)
Gearing up for cloud compliance happens the second you deploy your data to the cloud. Here, we explore what it is, why it matters, and how to make sure your cloud infrastructure is compliant with the latest standards.
Samantha Cruz . Nov 8 2019

Compliance
The Real Cost of Cloud Compliance (or Lack of It)
Gearing up for cloud compliance happens the second you deploy your data to the cloud. Here, we explore what it is, why it matters, and how to make sure your cloud infrastructure is compliant with the latest standards.
Samantha Cruz . Nov 8 2019

Release Notes
Release Notes Sep 2019: Vulnerability Management Beta
Introducing our newest beta feature — Vulnerability Management. Also in this release — the first look at the CIS Benchmark integrated into Warden findings and a new way to filter your findings.
Samantha Cruz . Sep 24 2019
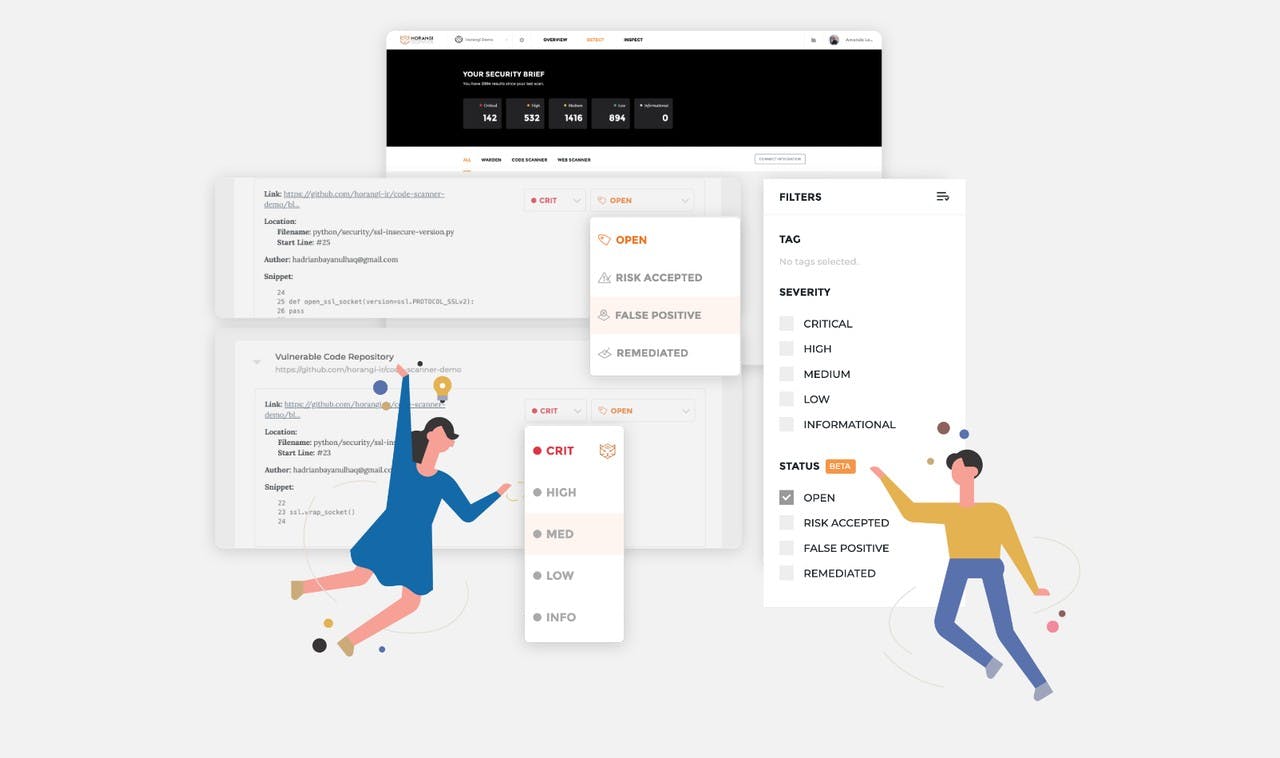
Release Notes
Release Notes Sep 2019: Vulnerability Management Beta
Introducing our newest beta feature — Vulnerability Management. Also in this release — the first look at the CIS Benchmark integrated into Warden findings and a new way to filter your findings.
Samantha Cruz . Sep 24 2019

Release Notes
Release Notes Jun 2019: Storyfier Now Integrated With Slack
Horangi Storyfier is now integrated with your Slack account so you never miss a notification.
Samantha Cruz . Jul 9 2019
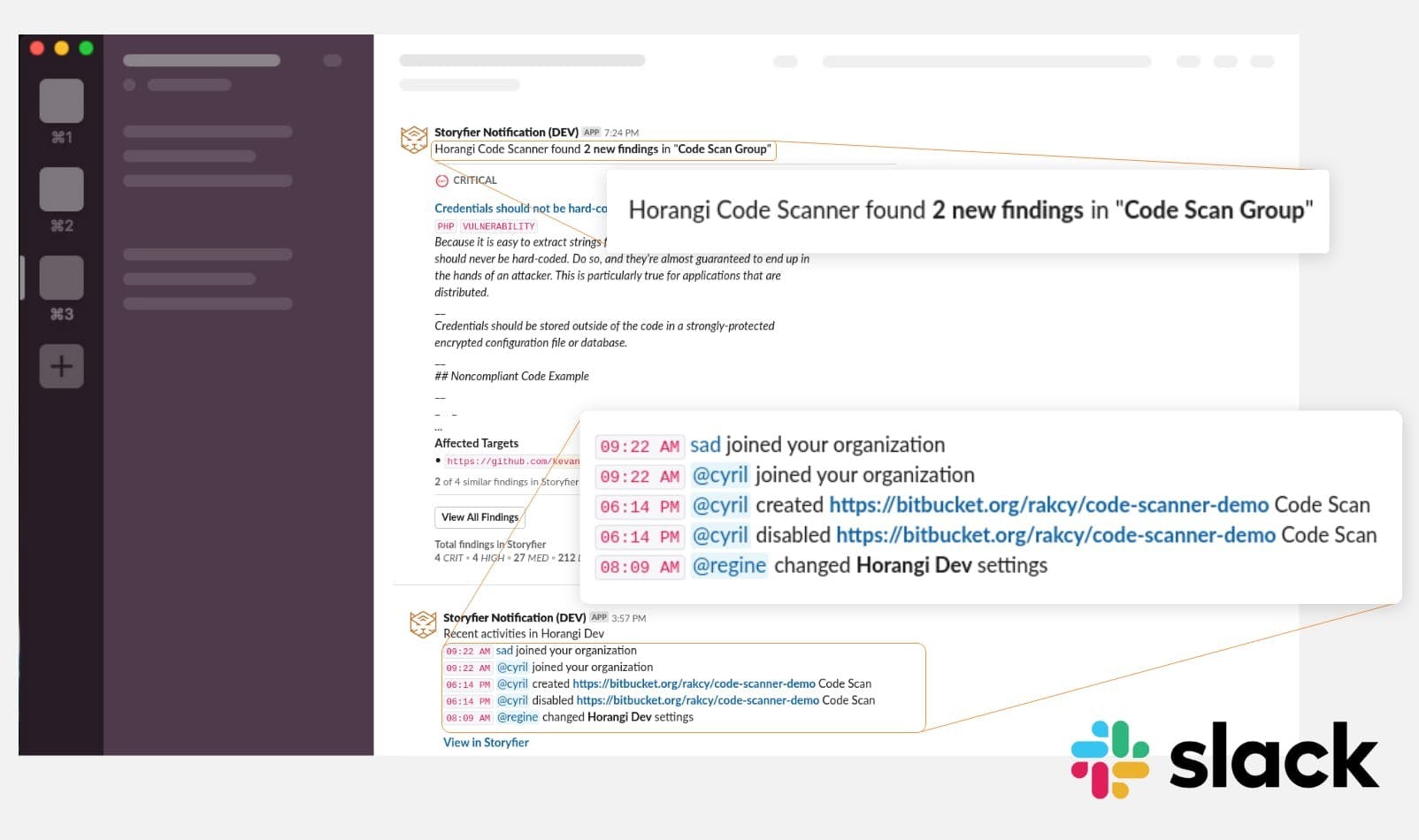
Release Notes
Release Notes Jun 2019: Storyfier Now Integrated With Slack
Horangi Storyfier is now integrated with your Slack account so you never miss a notification.
Samantha Cruz . Jul 9 2019

Release Notes
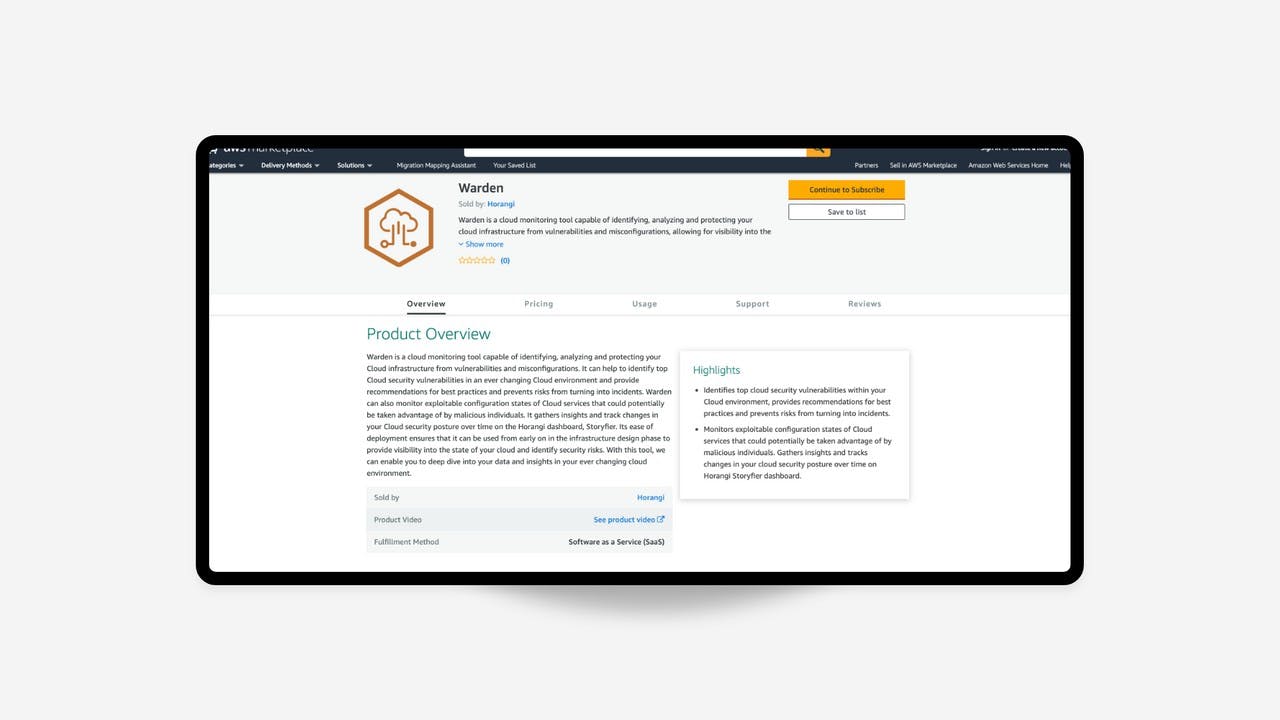
Release Notes May 2019: Horangi Warden on AWS Marketplace
Horangi Warden is now on AWS Marketplace!
Samantha Cruz . Jun 7 2019
Release Notes
Release Notes May 2019: Horangi Warden on AWS Marketplace
Horangi Warden is now on AWS Marketplace!
Samantha Cruz . Jun 7 2019

Release Notes
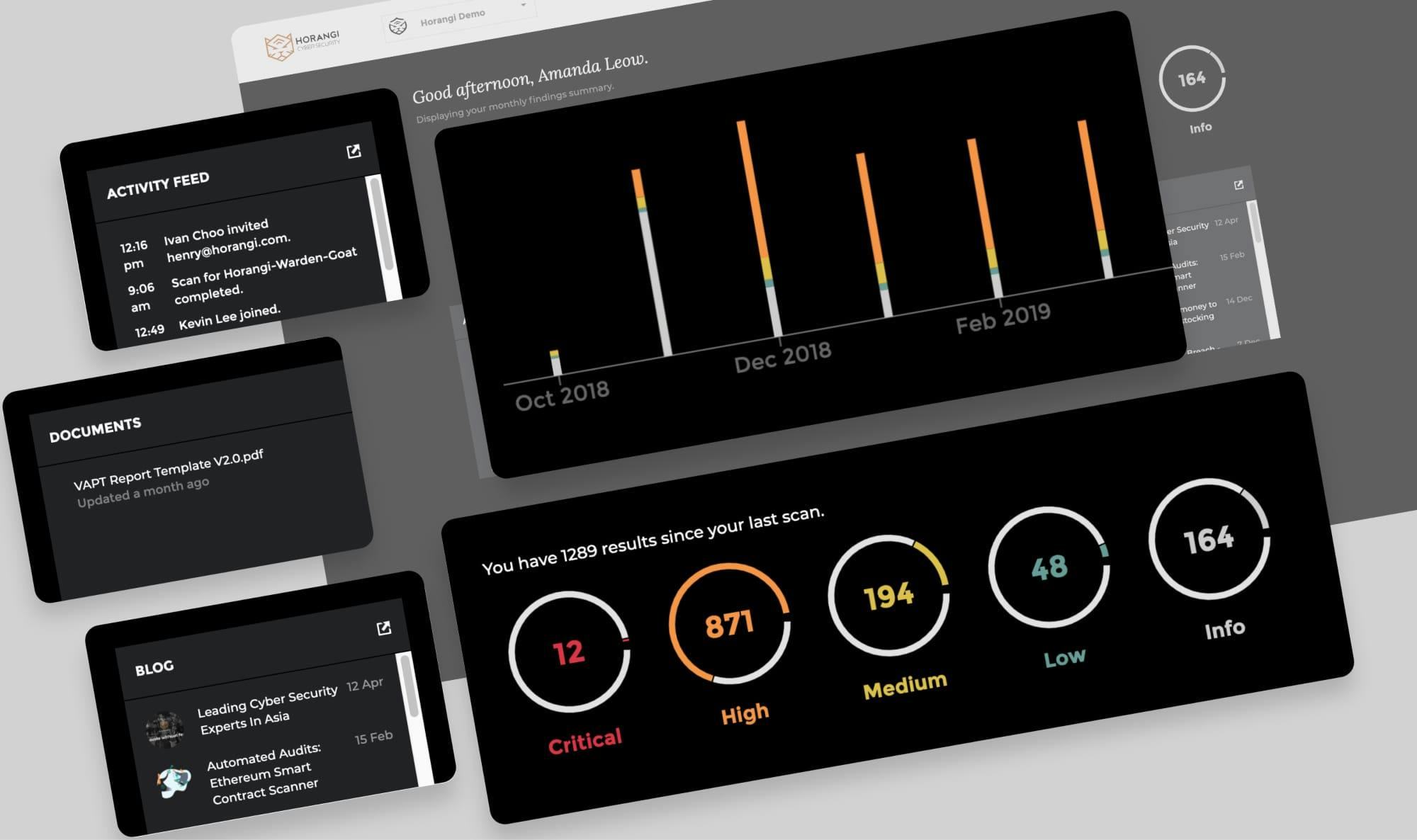
Release Notes Apr 2019: Horangi Storyfier Updates
We’re excited to introduce to you a new series called Release Notes, where we’ll highlight all the improvements we’ve launched so you can easily stay up-to-date on what’s new.
Samantha Cruz . Apr 17 2019
Release Notes
Release Notes Apr 2019: Horangi Storyfier Updates
We’re excited to introduce to you a new series called Release Notes, where we’ll highlight all the improvements we’ve launched so you can easily stay up-to-date on what’s new.
Samantha Cruz . Apr 17 2019

Cybersecurity Strategy
How to lose money to (credential) stocking stuffers
Credential Stuffing is an emerging form of attack that uses automated scripts to try out username or password pairs to gain access to a system.
Samantha Cruz . Dec 14 2018

Cybersecurity Strategy
How to lose money to (credential) stocking stuffers
Credential Stuffing is an emerging form of attack that uses automated scripts to try out username or password pairs to gain access to a system.
Samantha Cruz . Dec 14 2018

Crypto Security
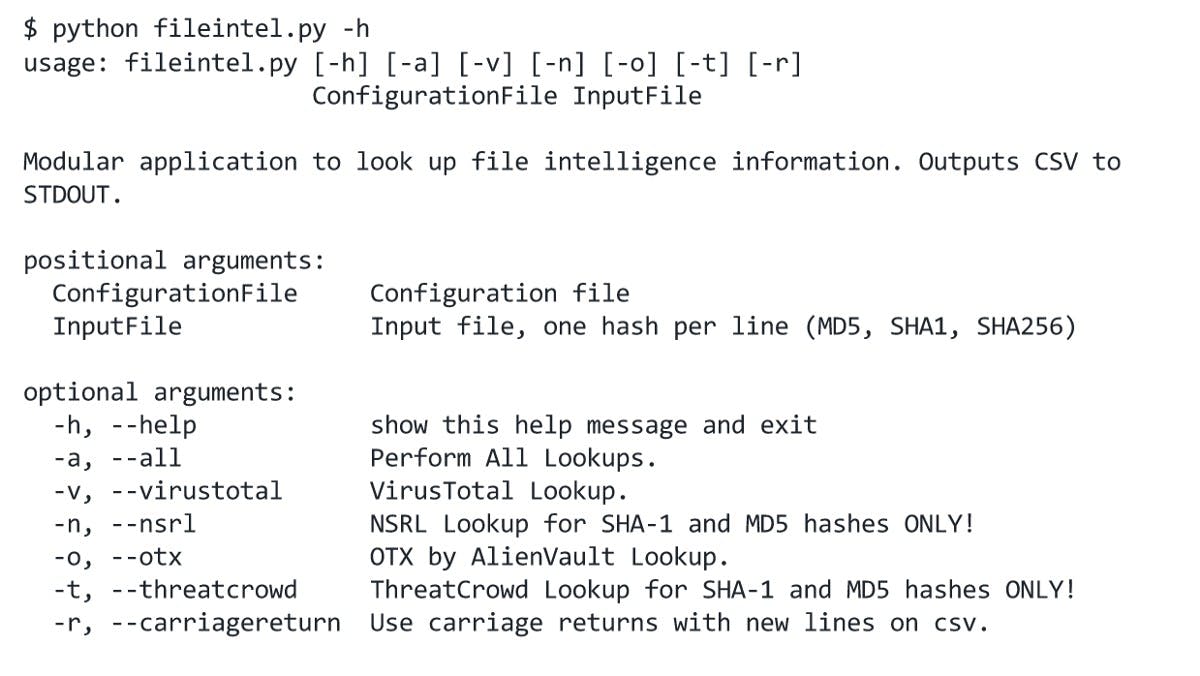
Hash Lookup Using FileIntel
Why do Hash Lookups? Looking up cryptographic hashes of files is done for various reasons.
Samantha Cruz . Jun 8 2018
Crypto Security
Hash Lookup Using FileIntel
Why do Hash Lookups? Looking up cryptographic hashes of files is done for various reasons.
Samantha Cruz . Jun 8 2018

Cybersecurity Strategy
10 Effective Ways to Boost your Cybersecurity Defenses
One can build complex, sophisticated system of defenses to protect themselves, but just one hole, and the game’s up before it even started. The good news is there are many simple ways users can protect themselves and their data
Samantha Cruz . Jun 1 2018
Cybersecurity Strategy
10 Effective Ways to Boost your Cybersecurity Defenses
One can build complex, sophisticated system of defenses to protect themselves, but just one hole, and the game’s up before it even started. The good news is there are many simple ways users can protect themselves and their data
Samantha Cruz . Jun 1 2018























