In part 1 of this seriespart 1 of this series, we discussed open-source intelligence (OSINT), how it’s being used, and how it can help an organization in their information security operations.
In this part will be discussing a few tools and techniques used to gather open source intelligence and then some examples of analysis to make sense of the information collected.
Polish Your Google-Fu
Believe it or not, search engines are a vast source of OSINT, and you don’t need special tools to access them. Google Hacking is an information gathering technique used by attackers by entering “advanced” Google queries.
These search queries can be used to identify vulnerabilities in web applications, gather information for a particular target or targets, discover messages disclosing sensitive information, or discover files containing credentials and other sensitive data.
In short, Google will reveal many things, if one knows what to look for.
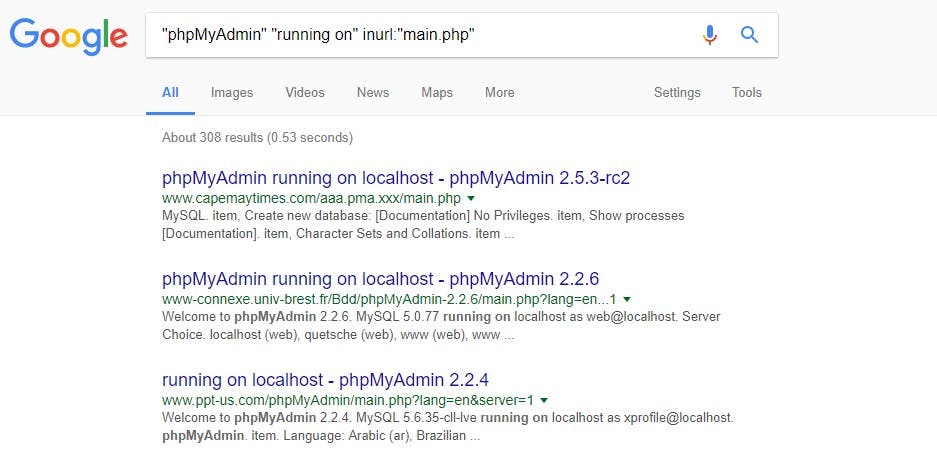
For example, someone can access publicly accessible phpMyAdmin installations by typing this query on Google.
“phpMyAdmin” “running on” inurl:”main.php”
This is a snapshot of the Google search result.
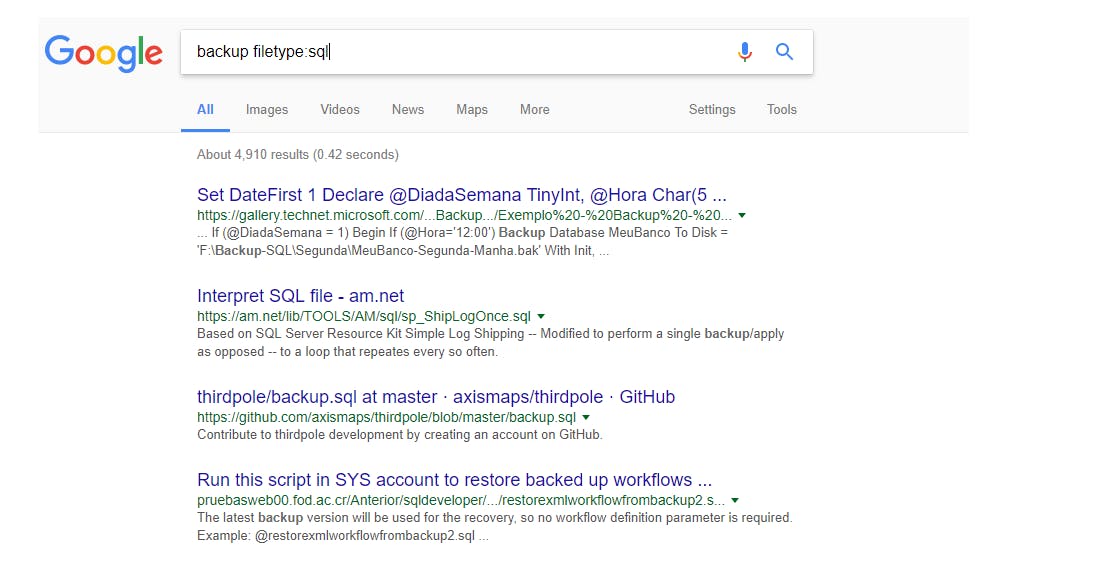
Another example is using the filetype parameter to limit search to specific file extensions. For example, one can find numerous SQL file backups using the following query.
Backup filetype:sql
Note that there should be no space between “filetype:” and “sql”
This site has several examples of Google search parameters that will uncover a lot of interesting detail, if one has an idea of what to look for.
Spiderfoot! Spiderfoot!
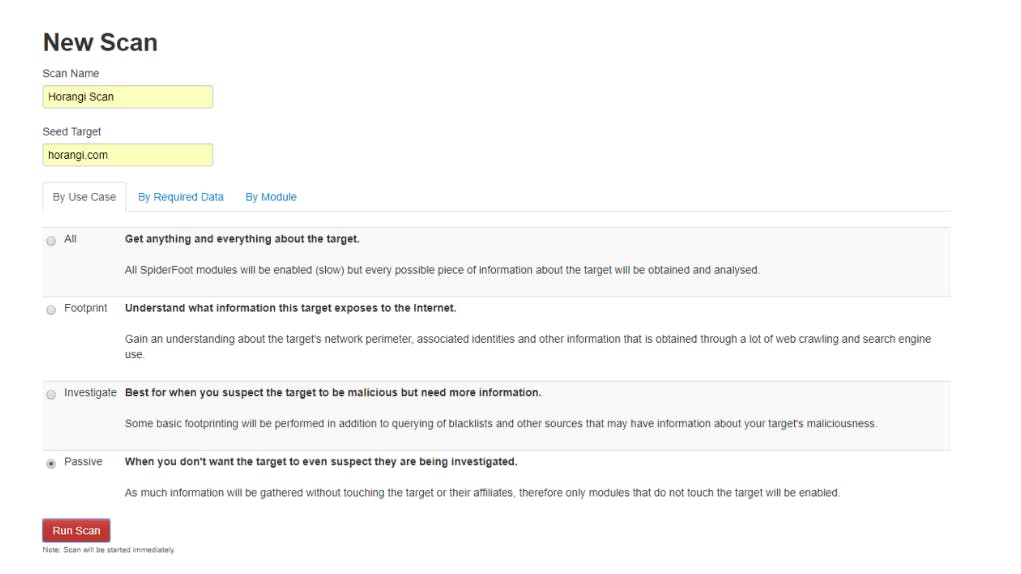
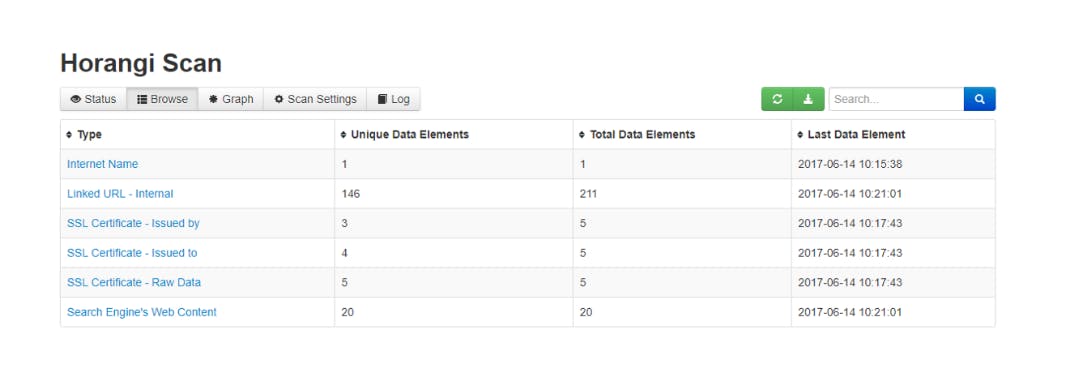
SpiderFoot is an OSINT gathering automation tool. Its goal is to automate the process of gathering intelligence about a given target.
Once the program is installed and running, start a new scan by entering a descriptive name and the target you want to scan before clicking New Scan.
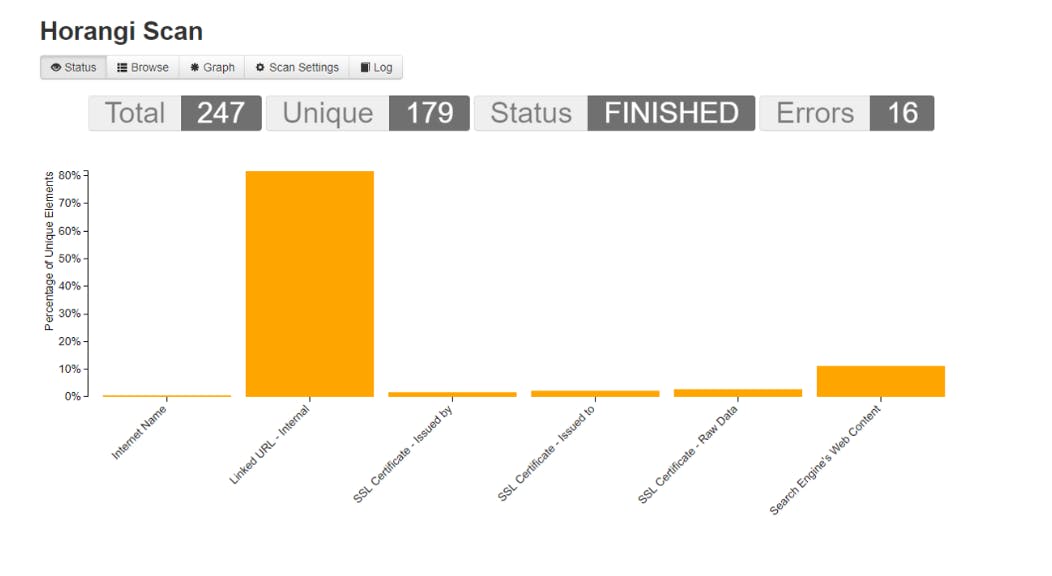
Spiderfoot will run and will visualize all the elements that have been found. This allows someone to get a general idea of a target’s infrastructure.
This data can also be exported to CSV format for further analysis.
Hold the Onions!
Another OSINT gathering tool available is OnionScan. OnionScan is a tool used to search for hidden services in the dark web looking for potential data leaks. The question in mind when this was made was: Are dark web sites as anonymous as people think they are?
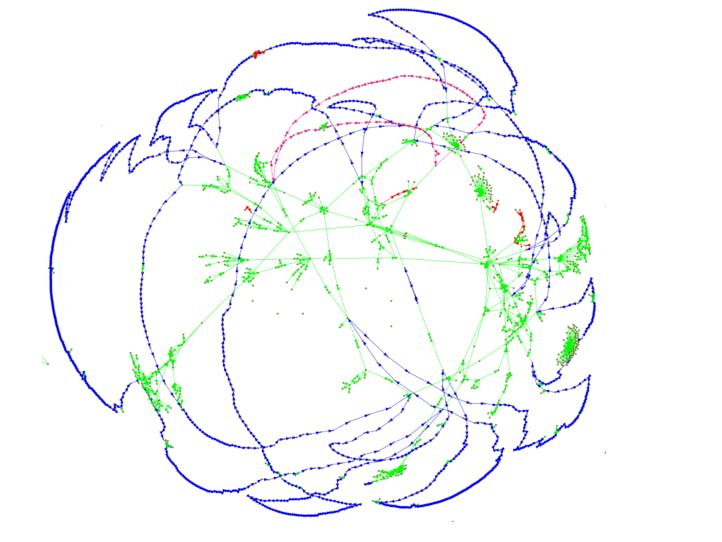
To answer this question, Mascherari Press released OnionScan reports visualizing the scan results, and they discovered that the Dark Web is less anonymous than they thought it was.
Apart from links (green) they also looked at relationships detected through SSH public keys (blue), FTP banners (pink) and Apache mod_status leaks (red). Below is their visualization of the different connections between dark web sites.
(Image source: https://mascherari.press/onionscan-report-june-2016/)
For example, of the 5600 active sites that they scanned during June 2016–23% shared a single unique SSH Key, which means they can all be linked to one hosting group — Freedom Hosting II.
This lack of diversity did not bode well for the dark web as Freedom Hosting II was compromised last February 2017.
This only shows how OSINT tools can used to create relational maps of the web and, with the proper link analysis, show the relationships between seemingly unconnected resources and show a clearer picture.
Now what?
These are just a few of the common OSINT tools available online; many more tools and methods exist and are ready for you to use. In the next and final part of this series, we will close out the topic with a demonstration on how OSINT can be integrated with an internal security program and help with beefing up security for both infrastructure and operations.
References:
https://www.acunetix.com/websitesecurity/google-hacking/
http://resources.infosecinstitute.com/google-hacking-the-hidden-face-of-google-2/
https://nakedsecurity.sophos.com/2016/07/06/the-dark-web-just-how-dark-is-it/
https://www.darknet.org.uk/2015/11/spiderfoot-open-source-intelligence-automation-tool-osint/
https://mascherari.press/onionscan-report-june-2016/
https://mascherari.press/onionscan-report-fhii-a-new-map-and-the-future/