Introduction
Network Penetration Testing (Network Pentest) is one of the common security assessments that companies perform to assess the security posture of their infrastructurecompanies perform to assess the security posture of their infrastructure. Depending on the scope of work, network penetration testing can range from Red TeamingRed Teaming to targeted host Penetration TestingPenetration Testing, the latter seen in countries such as Singapore. The list of IP addresses permissible for a pentester to attack is typically pre-scoped and provided by the client, and this could range from addresses within an internal network to a list of public servers.
In this article, we focus on how a typical network penetration testing is performedhow a typical network penetration testing is performed within a client network environment, from scoping of requirements to reporting. Even as you understand how a Network Pentest is typically conducted, it important to note that there is no one silver bullet approach to your assessments. Experienced pentesters need to tailor and adjust the approach according to the client's environment.
Scope of Work
Before any penetration testing is performed, always establish the scope of work and rules of engagement agreed upon between both parties. The scope of work sets the boundaries of the assessment, while the rules of engagement define the dos and don’ts of the assessment. Under the Computer Misuse Act, it is illegal to perform any form of computer hacking activity without authorization. Therefore, ensure the client has provided the green light before performing any security assessment.
The scope of work for targeted host penetration testing generally requires the following details to be established:
- Will it be a Black-box, Gray-box, or White-box pentestBlack-box, Gray-box, or White-box pentest?
- In what environment will the test take place? (Production, Staging etc.)
- The list of in-scope subnets
- The location of each subnet
- The list of in-scope IP addresses and its relevant network information, such as subnets
- Exclusions
The rules of engagement then sets the expectations of the security assessment. For instance, the client may not want the pentester to exploit certain vulnerabilities, perform lateral movement, or privilege escalation. When the assessment can be conducted would also be established, in the event the client prefers it to be done outside of working hours to reduce the risk of downtime.
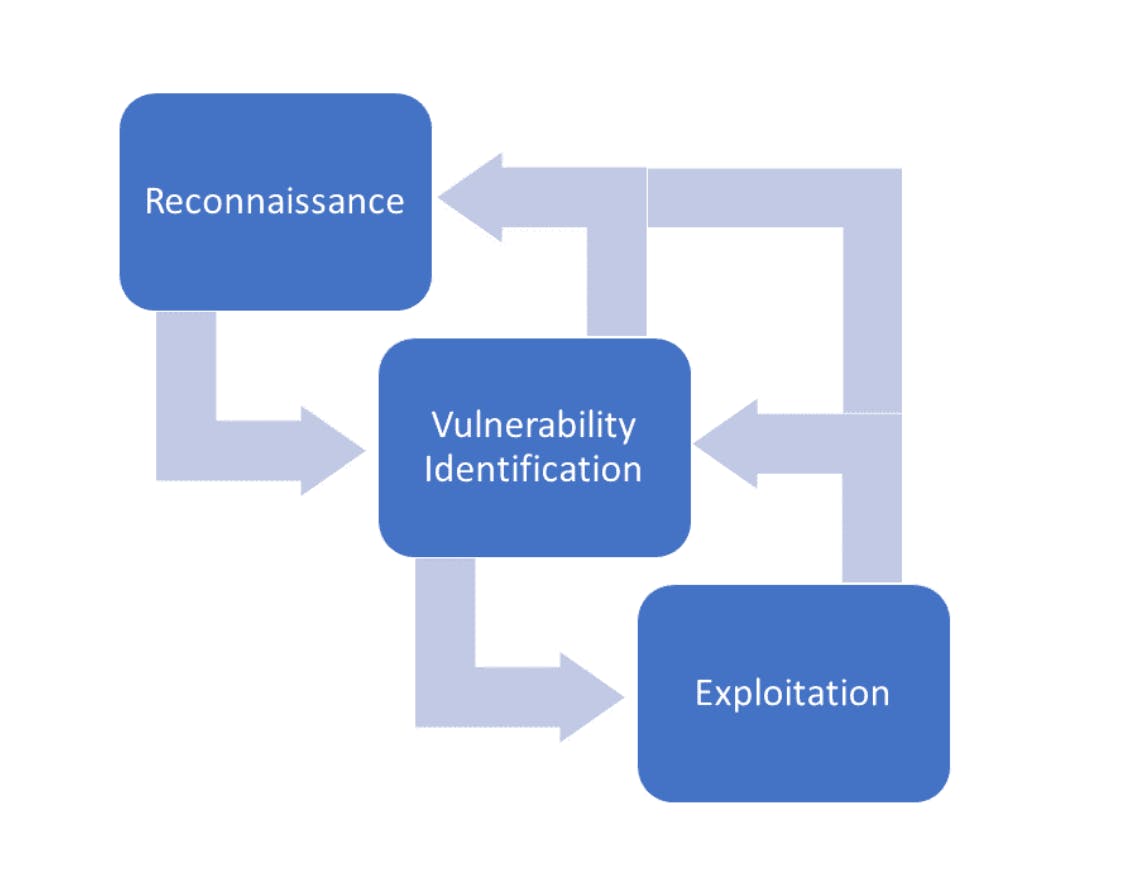
Fig 1.1 The standard Network Pentest sequence graphically represented, in the stages below.
1. Reconnaissance: Where Might The Target Be Weak?
At the beginning, you are expected to gather as much information about the targets as possible, using methods such as port scanning and service detection. Try to fingerprint the services running on each service and gather as much data on each service as possible. Active and passive reconnaissance will be performed on the targets. Open-source Intelligence (OSINT)Open-source Intelligence (OSINT) methods may also yield interesting information on the targets.
Diligently take notes to ensure you cover all the targets and scans. Commercial network scanners such as Tenable Nessus are viable options for scanning the targets. After that, you should perform more enumeration on the detected services. For example, if the server is running a web server, you could run additional scanners — web scanners, directory busting tools, CMS vulnerability scannersweb scanners, directory busting tools, CMS vulnerability scanners etc. Do the requisite research on things to look out for in different network services so that crucial information that may aid you on your vulnerability identification and exploitation phase is not missed.
If you manage to get access to the targets, be it from exploitation, gray-box, or white-box testing, more enumeration on the system should be done to find ways to escalate privilege or access more restricted networks.
Do take down any interesting observations you see, such as unexpected behavior and sensitive information including credentials, backup files, and configuration files.
With reconnaissance done, you should have the following target information:
- List of open ports and detected services, e.g. HTTP, DNS, Mail
- The target host Operating System (OS) and version
- Enumeration on the services, such as list of directories, vulnerabilities, and application version
- The credentials found or given
- Any interesting observations found during reconnaissance
- Network map (had you not had it previously)
2. Vulnerability Identification: Verify Your Findings
With all the raw information gathered about your target, it is now time to review the results, remove the false positives, and identify potential exploitable vulnerabilities. Further manual testing, fuzzing, or running of custom scripts may be needed to find these vulnerabilities.
Manual testing
Manual testing typically requires the tester to write their own custom payloads to test if the vulnerabilities are, indeed, vulnerable. While automated tools such as Metasploit-framework, SQLmap, or xssstrike can be used to verify vulnerabilities, you still need to manually verify in order to cover all bases. This way, you can identify the weak mitigation measures used, such as blacklisting of certain keywords.
Fuzzing
Automated fuzzers like Burp Suite (Intruder/Scanner), DNSWalk, or SNMPWalk are often used during reconnaissance. At this stage, it is the responsibility of the pentester to manually review the responses or results returned, identify any unexpected behavior, and do further investigation. If possible, you should get access to a testing server or the binaries to perform fuzzing so you can attach a debugger to identify the vulnerability. It is often very difficult to reliably identify buffer overflow vulnerabilities remotely.
If there are no potential vulnerabilities found, it is recommended to return to your notes and perform more enumeration if required. Once most of the vulnerabilities are identified, it is time to move on.
3. Exploitation: Where The Rubber Meets The Road
Exploitation is where the pentester needs to craft the payload such that the exploit is reliable and causes minimal to no impact on the target. Do not forget the rules of engagement. Strictly adhere to it. Any adverse impact caused by your exploits can have significant consequences on the client's environment. Not following these rules of engagement can put both the client and yourself at jeopardy. Ultimately, you are potentially liable for any damage caused.
Let’s take an example that you find a potential remote code execution on a web application. If you have the testing web applicationtesting web application on your own machine, it would be best to test out your exploit locally before testing it on the target. Otherwise, you might want to do further investigation on what is causing the vulnerability to exist. If there are verbose error messages revealing the code, you could replicate the vulnerability and use it to test the payload locally to ensure the application did execute it without error. Once you get the payload tested, you could attempt to exploit it and try to get a reverse shell connection back to your machine. If you manage to successfully get the connection back, you have unlocked a new level of access. Good news? Now you can do further reconnaissance and enumeration to uncover more vulnerabilities lying beyond the target system or network.
If the exploit fails, you may need to do more research on why and what caused the exploit to fail. If you determine that the vulnerability is a false positive, you need to go back to Vulnerability Identification or the Reconnaissance phase to find more vulnerabilities.
4. Reporting: Proof of the Work
Every Network Penetration Test is a time-limited assessment. Once the assessment is complete, the pentester needs to draft a report complete with findings — the description, how to recreate the exploit, evidence, and the next steps. It is always useful to explain the impact of the vulnerability so that the developer or security analyst has the context to effectively fix the network vulnerability.
Conclusion
Like what Fig 1.1 shows, the approach to doing a comprehensive Network Pentest is cyclical — never-ending, just as a real world threat actor would operate. As a pentester, your job is to ensure you've gotten most of the common vulnerabilities patched, making it as challenging as possible for attackers to find any information on the target.
Ultimately, the key to the success of a Network Pentest is to make sure you have enumerated enough and left no stones unturned. Often, the vulnerability is staring right at you without you noticing it. Deep knowledge of various network services such as DNS, FTP, and SMB will help you to identify vulnerabilities faster.




