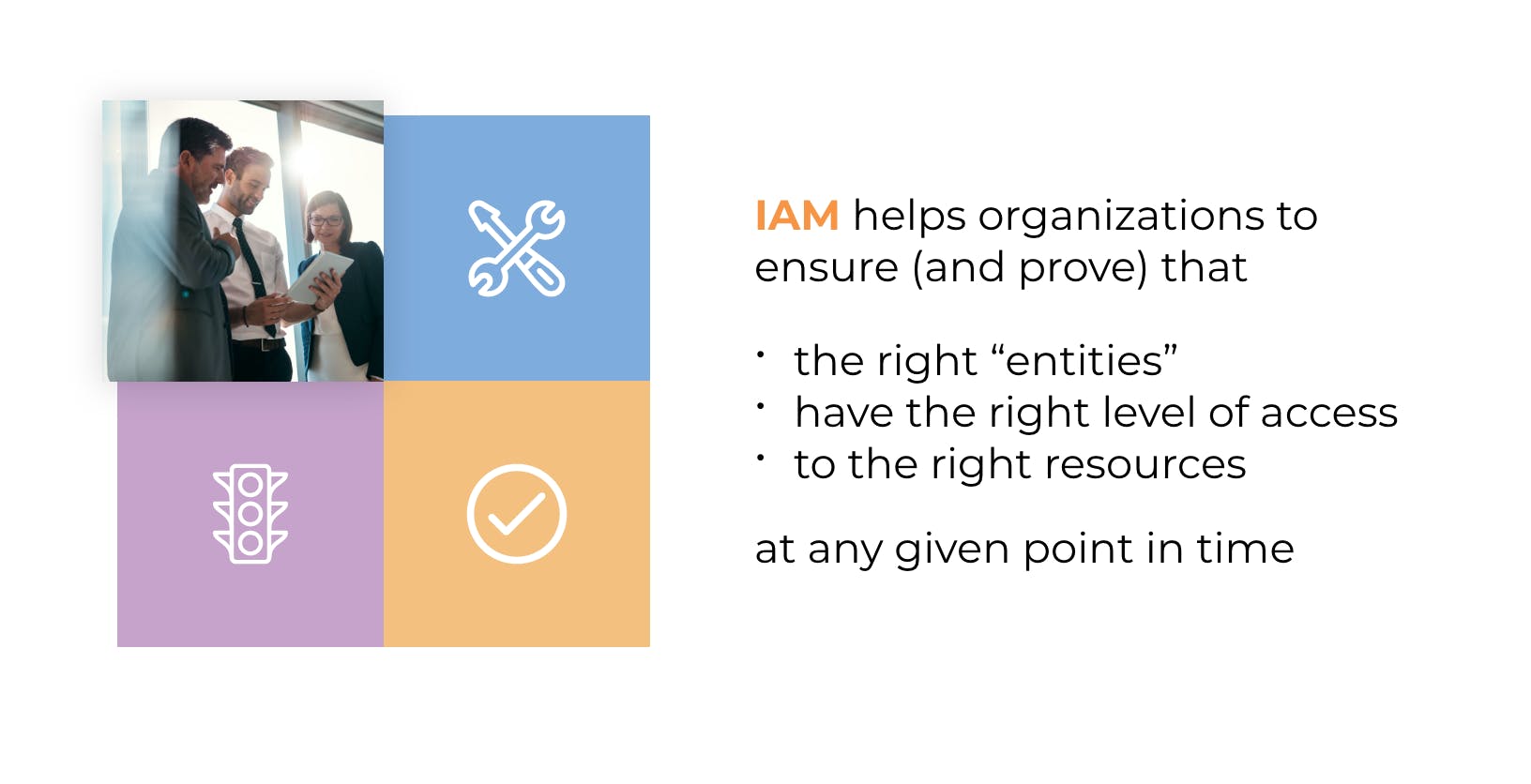
Why do you need IAM?
Warden IAMWarden IAM prevents cloud data breaches by automating the detection of identity and access managementidentity and access management risks in AWS, Google Cloud, Azure, and Alibaba Cloud (coming soon). It automatically discovers all user and service identities and analyzes their entitlements, as granted by roles and policies, using a continuous lifecycle approach. By combining analytics with granular, full-stack insights, Warden IAM makes it possible to enforce least privilege access at scale even in the most complex cloud environments.
Who has access to what in your cloud infrastructure? With Warden IAM, you can quickly find out. So in a nutshell, IAM is for you if you are adopting cloud services at scale in order to innovate and see yourself in any of these situations:
- Organizations that have established some level of cloud security strategy but are still not utilizing a third-party tool for entitlements management for your cloud infrastructure.
- Team of developers and business units directly managing their own cloud and data resources, who might not manage access permissions and secure them properly.
- Security team or DevOps team with limited bandwidth to have complete visibility in your entitlements management system to mitigate security threats.
- Organizations that have not yet implemented the Least Privilege Principle for their cloud infrastructure.
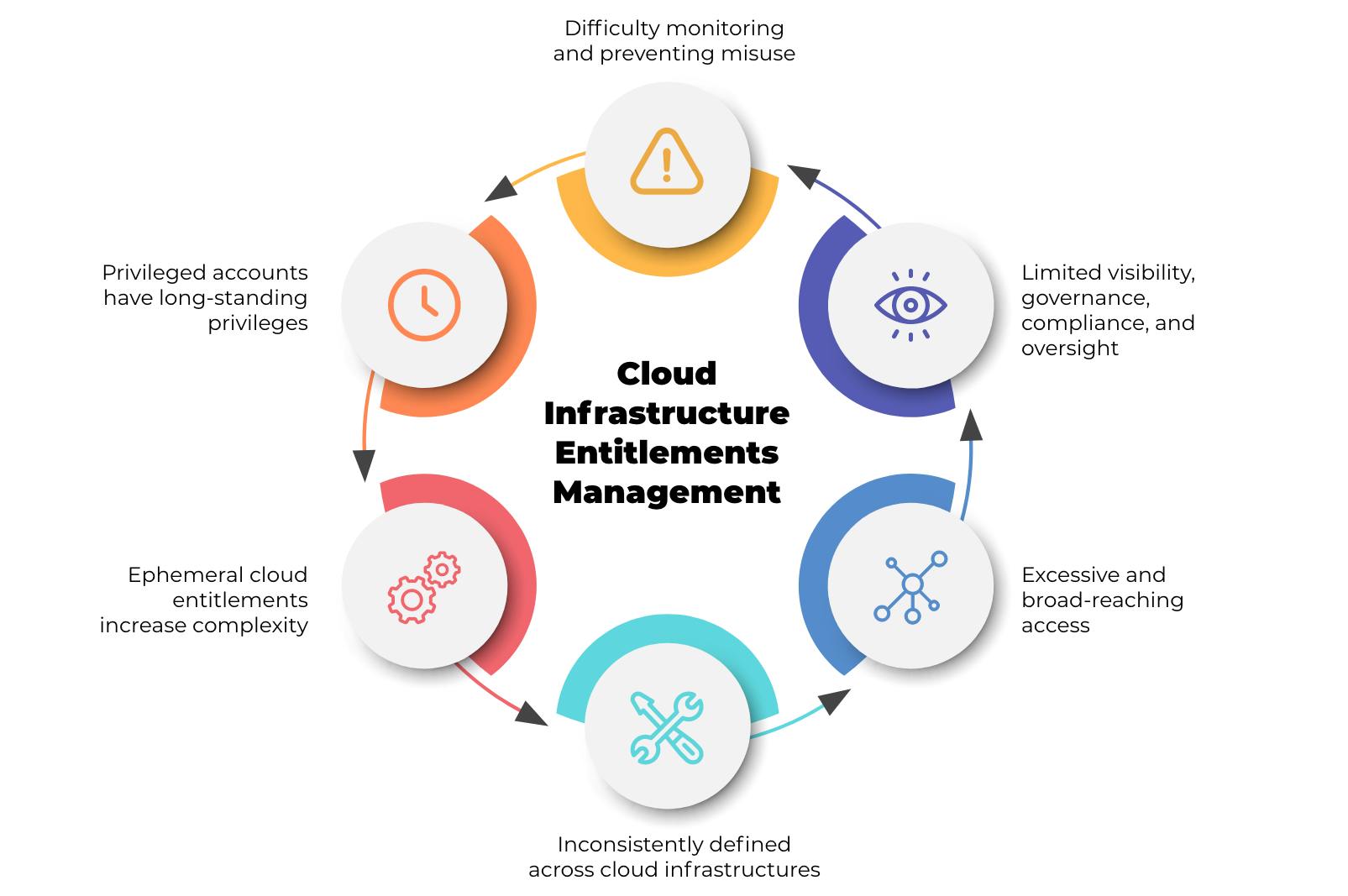
Problems Faced Due to Poor IAM Systems
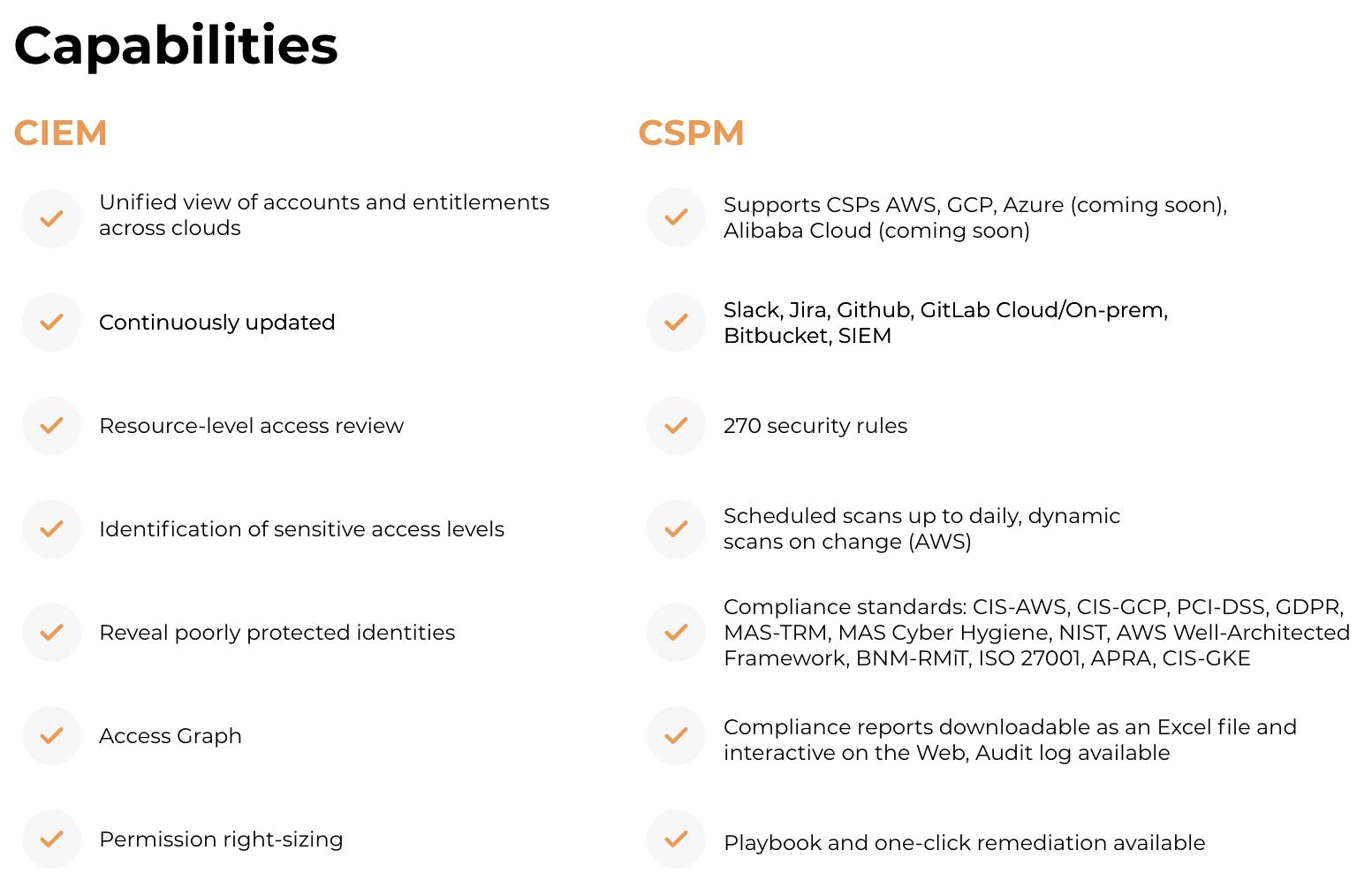
Our Solution: Warden IAM Capabilities
Visibility
Warden IAM makes it easy to have a consistent and comprehensive view of all access privileges across cloud environments.
Some common use cases that face this potential challenge are:
1. Visibility across all identities: Human and non-human identities (such as services or applications), federated (identities defined outside the cloud service provider), and native cloud identities.
2. Visibility across all resources: With Warden IAM analyzed access path, the traversal of your permission structure is displayed in an aggregated format. You can quickly tell who (all identities) has access to your resources in less than 30 seconds.
Continuous Monitoring
In a complex cloud infrastructure, access privileges can expand dynamically. To mitigate risks, Warden’s IAM data is always up to date to ensure that you can constantly monitor the exposure to vulnerabilities, making sure that you’re not exposed.
IAM Dashboard: With Warden IAM you don’t have to open multiple tabs and windows to keep track of access permissions. Our solution quickly summarizes key data insights on a unified dashboardunified dashboard. You can immediately identify the actions you need to take to reduce the risk exposure in your identities and access management.
Two-in-one Platform (CSPM + CIEM)Two-in-one Platform (CSPM + CIEM)
Getting not only your general security exposure insights but also visibility to your identities and access management setup, within minutes of configuration.
Conclusion
If you are having trouble answering “who has access to my crown jewels, and what kind of access do they have in my cloud infrastructure?” then get in touch with Horangi for a quick demo of Warden IAMget in touch with Horangi for a quick demo of Warden IAM to identify important security risks and remediation steps today.




