UPDATE: This blog was originally published on 15 October 2021, and is updated to include the Log4j2 vulnerability as a real life example of A06:2021 Vulnerable and Outdated Components.
What's new in 2021
- Three (3) new categories made it to the Top 10
- Some vulnerabilities have been renamed to better reflect the nature and scope of the vulnerabilities
- There is a new Number One
These are some real-life examples of each of the Top 10 Vulnerabilities and Cyber Threats for 2021 according to The Open Web Application Security Project (OWASP).

- Broken Access Control (up from #5 in 2020 to the top spot in 2021)
- Cryptographic Failures (up from #3 in 2020 to #2 and was previously categorized as “Sensitive Data Exposure”)
- Injection (previously #1 in 2020)
- Insecure Design (New category)
- Security Misconfiguration (up 1 place from 2020 to #5)
- Vulnerable and Outdated Configurations (previously categorized as “Using Components with Known Vulnerabilities” and moved up from #9 in 2017)
- Identification and Authentication Failures (previously categorized as “Broken Authentication”, slipped from #2)
- Software and Data Integrity Failures (New category)
- Security Logging and Monitoring Failures (previously categorized as “Insufficient Monitoring and Logging”, up from #10)
- Server-Side Request Forgery (New category)
A01:2021 Broken Access Control
Broken Access Control happens when access permissions are misconfigured thereby allowing attackers to access, modify or delete data, files and accounts that they should not have access to in the first place.
Snapchat / Facebook Business (Jan 2014 / Aug 2015)
Snapchat
Gibson Security detailed vulnerabilities in the snapchat service, which was dismissed as a purely theoretical attack. A week later, brute force enumeration had revealed 4.6 million usernames and phone numbers.
Why was this significant?
The attack seems to be motivated at least partly by Snapchat’s assertion that the attack was theoretical, and they had not taken any action. This resulted in a data leakage of phone numbers and users details that could be valuable for various uses.
Facebook Business Pages
Laxman Muthiyah found that it was possible for a malicious user to use a request to assign admin permissions to himself for a particular Facebook page. A sample request can be seen below:
Request :-
POST /<page_id>/userpermissions HTTP/1.1
Host : graph.facebook.com
Content-Length: 245
role=MANAGER&user=<target_user_id>&business=<associated_business_id>&access_token=<application_access_token>
Response :-
true
Why was this significant?
Business pages are a widely used function, and by executing this attack, a malicious user could add himself as an administrator and deny access to the actual manager or administrator.
How does this relate to Broken Access Control?
Both issues arose due to the lack of access control measures with a specific function provided.
A02:2021 Cryptographic Failures
Previously known as “Sensitive Data Exposure”, cryptographic failures occur when sensitive data is insufficiently protected and therefore leaked or exposed to unauthorized audiences. Such failures are most common if data is transmitted or stored in clear text or using known-to-be-weak cryptographic algorithms such as MD5 or SHA-1.
Cloudbleed (2017)
Google’s Project Zero found an issue in Cloudflare’s edge servers made it possible to dump memory potentially containing sensitive data, some of which were cached by search engines. This security bug was named Cloudbleed.
Why was this significant?
Cloudflare had acknowledged the leak could have started as early as 22 September 2016, and a private key between Cloudflare machines had leaked. As nearly 6 million websites uses Cloudflare’s services, and many web application defenses are built with the assumption of a secure TLS communication channel, the impact could be large. Estimates from Cloudflare state that between 22 September 2016 and 18 February 2017, the bug was triggered 1,242,071 times.
Cloudflare did a small sample study, with a confidence level of 99% and a margin of error of 2.5%, which showed a limited amount of sensitive data exposed.
- 67.54 Internal Cloudflare Headers
- 0.44 Cookies
- 0.04 Authorization Headers / Tokens
- 0 Passwords
- 0 Credit Cards / Bitcoin Addresses
- 0 Health Records
- 0 Social Security Numbers
- 0 Customer Encryption Keys
How does this relate to Cryptographic Failures?
This should be clear intuitively. The original flaw was due to the way broken html tags were parsed, causing information from a random portion of the server’s memory to be returned.
A03:2021 Injection
An attacker can execute unintended commands or gain access to sensitive data by injecting malicious data as part of a command or query. This usually happens when a website fails to filter, validate or sanitize users’ inputs or implement parameterization.
The Panama Papers incident (Apr 2016)
The Panama Papers are a collection of 11.5 million records from Mossack Fonseca, originally leaked to German journalist Bastian Obermyer in 2015. Due to the sheer size of the data, the International Consortium of Investigative Journalists were approached.
Why was this significant?
Many public figures, present and past, had their financial dealings exposed, linking them to terrorists, drug cartels and tax havens. Some public figures had their careers affected, and in some instances, the information directly led to public unrest.

AFP/Getty images, The Indian Express, The Guardian, Daily Mail, whoar.co.nz
This is also significant from the cybersecuritycybersecurity point of view as it brought to attention the potential vulnerability and relative ease of attacking law firms, compared to the value of the information they carry. Fortune magazine wrote a commentary piece “The Panama Papers Signal A New Kind of Cyber Attack”, citing hacktivism as the motive, with income inequality as the reason. While not (actually) new, the incident did bring this to the public spotlight.
How does this relate to injection/using components with known vulnerabilities?
The documents were leaked in parts, and the site was hosted on outdated software, open to a large number of vulnerabilities. Unfortunately, due to the large number of possible attack vectors, it is hard to pin down the actual method used by the subject(s) who leaked the data.
- WordPress 4.1 (Released December 18, 2014) — various vulnerabilities
- Revolution Slider Plugin — unauthenticated remote file upload via ‘upload_plugin’
- WP SMTP Plugin — mail server login information stored in plaintext
- ALO EasyMail Newsletter plugin — mail server login information stored in plaintext
- Drupal 7.23 (Released August 8, 2013) — 23 vulnerabilities, including code execution and privilege escalation via SQL injection of the Drupalgeddon fame
- Apache 2.2.15, Oracle fork (March 6, 2010) — various vulnerabilities
- Microsoft Exchange / Outlook Web Access (2009) — various vulnerabilities
- A SQL injection SQL injection flaw was discovered by 1×0123(Twitter) in their payment system
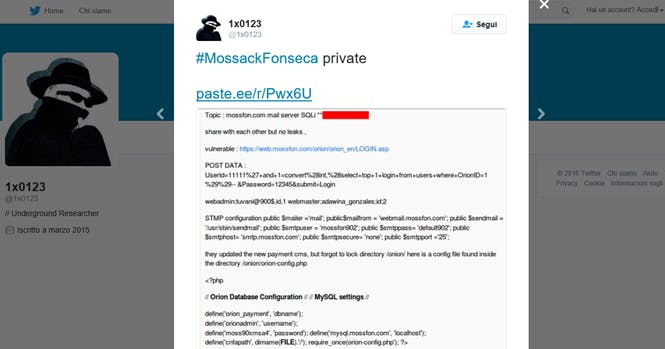
Both the revolution slider’s unauthenticated file upload, which could lead to execution of PHP code, and the code execution via SQL injection on Drupal are trivial to exploit have been pretty thoroughly taken advantage of in the wild.
A04:2021 Insecure Design
Insecure design is a new entry on the OWASP Top 10 in 2021. It is different from insecure implementation in that it has more to do with risks related to design and architectural flaws. A secure implementation might have an insecure design which still renders a web application vulnerable to attacks and exploits.
One good example of insecure design in recent times prevented PC users and gamers from being able to purchase new Nvidia GPUs at recommended retail prices.
Many e-commerce sites did not factor in protection against bots that scalpers used to buy up their entire stocks which were limited to start with.
Scalpers then resold the cards at cut-throat marked up prices on auction websites, meaning those who really needed to obtain a new GPU had to fork out prices that were many times higher than the recommended retail price.
A05:2021 Security Misconfiguration
This category covers a brand range of potential vulnerabilities including insecure default configurations, incomplete configurations, and misconfigured HTTP headers, using insecure default usernames and passwords, etc.
Amazon S3/Mirai (Now / Aug 2016)
Amazon S3
Notably, in recent years, there has been numerous organizations who failed to protect their Amazon S3 storage instance:
- Australian Broadcasting Corporation (Nov 2017) — Leakage of hashed passwords, keys and internal resources.
- United States Army Intelligence and Security Command (Nov 2017) — Various files, including Oracle Virtual Appliance (.ova). volumes with portions marked top secret.
- Accenture (Sept 2017) — Authentication information, including certificates, keys, plaintext passwords, as well as sensitive customer information.
There is an extremely high likelihood that similar issues will continue to be found.
Why was this significant?
A large number of organizations rely on Amazon’s S3 data storage technology, including governments and military organizations. From past examples found, this is a pervasive problem and the information leaked often has a high impact on the organization affected. Having a CSPM solution when you have cloud infrastructurea CSPM solution when you have cloud infrastructure will help monitor common cloud misconfigurations.
Mirai(未来)
Mirai was a botnet utilising IoT devices, managing to execute several high profile attacks after discovery, with the creator going to ground after releasing the code as open source (Anna-senpai).
Why was this significant?
Mirai ran from CCTV cameras, DVRs and routers. Essentially worked by trying common passwords, something that can be easily avoided. The entirety of the password list used is included below:
With such a simple method, the Mirai botnet produced 280 Gbps and 130 Mpps in DDOS capability, attacking DNS provider Dyn, leading to inaccessibility of sites such as GitHub, Twitter, Reddit, Netflix and Airbnb.
How does this relate to Security Misconfiguration?
Security misconfiguration can range from something as simple as allowing excessive permissions to a user account, to failing to restrict resource access to external addresses. In the cases mentioned above, they were caused by misconfiguration of the passwords protecting the systems.
A06:2021 Vulnerable and Outdated Components
This refers to known issues where vulnerabilities exist because developers either do not know the versions of components used including those of nested dependencies, or are not aware that the software used is already unsupported or out of date.
Log4j2 Vulnerability (Dec 2021)
A Remote Code Execution (RCE) vulnerability in the Apache logging package Log4j2 versions 2.14.1 and below was reported on 9 December, 2021.
Why was this significant?
The Log4j2 library is an open-source logging library provided by the Apache Software Foundation that is commonly used in online applications and services to capture logs for development, operational, and security purposes.
Dozens of major online service providers such as Amazon, Microsoft, IBM and Google, use the open-source library in their offerings.
Modern software development methodology drives the adoption of such software libraries, as there is no need to reinvent the wheel, resulting in quicker go-to-market. As a result, the library is sometimes embedded layers deep in applications.
The vulnerability required very little expertise to exploit. Threat actors only need to know how to parse a string into a URL to take over servers to steal data and passwords, install malware and crypto-mining software, and even sell access to third parties such as Ransomware-as-a-Service (RaaS) providers.
Microsoft reported that State-sponsored RaaS and hackers are capitalizing on the Log4j2 vulnerability.
How does this relate to Vulnerable and Outdated Components?
The Apache Software Foundation released an update, Log4j 2.17.1 on 27 December, 2021 to address all known Log4j2 vulnerabilities to date. Below is the release history of updates:
- 2.15.0 6 December, 2021
- 2.16.0 13 December, 2021
- 2.17.0 17 December, 2021
- 2.17.1 27 December, 2021
Log4j 2.16.0 was found to be vulnerable to DoS attacks, prompting the release of version 2.17.0 to address the new vulnerability.
The widespread use of the Log4j2 library means eradicating the threat will be a long-term exercise.
Besides applying patches from vendors and updating your Log4j2 versions, you can also conduct a compromise assessmentcompromise assessment to ensure that you are not already compromised, and carry out penetration testingpenetration testing to test your network and endpoints.
You can even go one step further to make less exploitation less likely while you are updating Log4j2 by deploying a CSPM such as WardenWarden that will help identify vulnerable workloads and act as defense-in-depthhelp identify vulnerable workloads and act as defense-in-depth to break a chain of attack in the event a vulnerable Log4j2 instance exists.
A07:2021 Identification and Authentication Failures
Previously known as “Broken Authentication”, this category covers weaknesses in authentication and session management in web applications. The resulting vulnerabilities allow attackers to gain unauthorized access to accounts and/or data.
Department of Revenue Hack (2012)
A foreign hacker was reported to have stolen 387,000 credit card numbers and 3.6 million Social Security numbers from the South Carolina Department of Revenue.
Why was this significant?
IRS was hacked again in 2015, exposing people’s social security numbers, address, incomes to more than 700,000 peopleexposing people’s social security numbers, address, incomes to more than 700,000 people. This information was then further used to authenticate themselves to get transcripts of their victims, resulting in more exposed data.
Even though in the first instance credit card data was encrypted, social security numbers and other personally identifiable data were not.
Direct consequences of this incident would be the exposure of these people to identity fraud. The 2017 Identity Fraud Study found that $16 billion was stolen from 15.4 million U.S. consumers in 2016, and in the past six years identity thieves have stolen over $107 billionthieves have stolen over $107 billion.
How does this relate to Identification and Authentication Failures?
The first breach in 2012 resulted from the default password set in the authentication layer. In addition, the lack of encryption on some sensitive data fields including the social security numbers increased the impact of this incident.
A08:2021 Software and Data Integrity Failures
This is the second new category in the Top 10 in 2021, and is concerned with the failure to verify the integrity of software updates and patches prior to implementation on live applications and servers.
Perhaps the most high-profile example of this would be the SolarWinds cyber attack in 2020.
SolarWinds, based in Texas, United States of America, provides a platform called “Onion” which helps numerous companies, many of which are Fortune 500 companies and include government agencies such as the Pentagon, to manage their IT resources.
Hackers managed to hack into the “Onion” and added malicious code which was undetected. As a result, SolarWinds unwittingly sent out updates and patches with the malicious code to its customer base. These compromised updates/patches then created backdoors which the attackers then used to install more malware to spy on the affected companies and government agencies.
A09:2021 Security Logging and Monitoring Failures
Previously categorized as “Insufficient Logging and Monitoring”, Security Logging and Monitoring Failures moved one place up from #10 this year. Logging and monitoring are essential components in ensuring that any suspicious activity can be detected close to real-time, or diagnosed after the fact.
Failure to keep sufficient records in these areas could subsequently lead to slower incident responses, thereby accentuating the potential damages of breaches.
Unfortunately, this is an extremely common issue and one that often does not come to attention unless the company experiences an incident and is unable to triage or diagnose it.
A10:2021 Server-Side Request Forgery (SSRF)
This is the third and final new entry into the Top 10 in 2021. Server-Side Request Forgery (SSRF) occurs when a web application proceeds to fetch data without first validating user-supplied URL.
In a bid to provide end-users with convenience, fetching data using a URL has become more common. The vulnerability allows an attacker to compel the web application to send a crafted request to unexpected destinations even when adequately protected by firewalls, VPNs and Network Access Control List (ACL).
There are two types of SSRF -- basic and blind.
A basic SSRF occurs when a victim server sends data back to the attacker after the latter sends a URL request to the server. A blind SSRF occurs when attackers are able to change data or trigger some action on the victim server.
Both types of SSRF can result in data exposure, internal recon, a Denial-of-Service attack and Remote Code Execution (RCE).
What fell out of the Top 10?
Although these categories have lost their places on the Top 10 list, it does not mean that they no longer exist or are any less of a threat. Organizations will do well to continue monitoring and deploying appropriate measures to mitigate these existing threats.
XML External Entities (XXE)
Android Studio, Eclipse, IntelliJ IDEA, APKTool (2017)
Check Point’s research team found vulnerabilities in popular Android development and reverse engineering tools used by developers, engineers and researchers. The issues found could lead to data exposure, as well as malicious users taking over the devices running APKTool.
The proof-of-concept attack allowed showed that a malicious user could inject the malicious code into shared online repositories such as those on GitHub, and allow the malicious user to obtain files available on the device reading the code. Similarly, the popular compiler APKTool has a vulnerability in the configuration yml file, allowing files to extracted anywhere on the system running it.
Why was this significant?
This vulnerabilities could be used to target developer’s machines and servers attempting to load, run, or decompile code.
In the development community, code or libraries are often shared in open source repositories, and a attack like this could result in sensitive documents such as credentials and source code to be exposed. Developers using these popular IDEs could be led to leak sensitive files in this manner.
In the second scenario, the APKTool exploit can lead to Remote Code Execution and allowing a remote malicious user to take control of the machine. For example, extracting a PHP exploit and calling the web server to run it.
How does this relate to XML External Entities (XXE)?
Both attacks are due to the way XML and YML(a similar human-readable data format) is parsed/read. The external reference contained in the XML is processed without further checks, leading to the above issues.
Cross Site Scripting (XSS)
Steam Profile Hack (Feb 2017)
This was a simple XSS hack that was discovered on the Steam platform, on user’s profile pages.
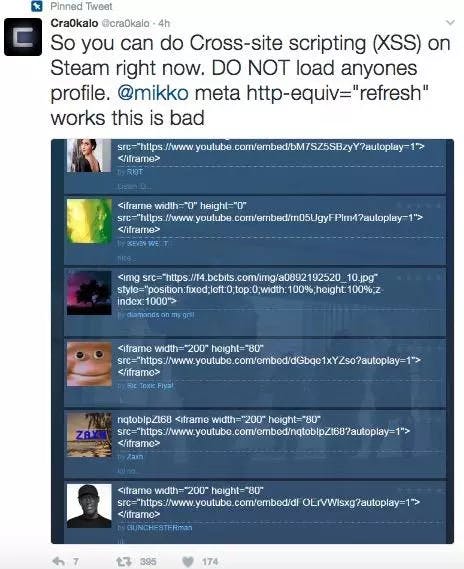
Why was this significant?
While the Steam profile page feature has existed for many years now, this relatively easy to execute hack was only discovered after a long period of time. The potential impact of this hack is well summarised by Reddit commenter “R3TR1X” and Moderator “DirtDiglett”:
- Redirecting a user to a website to phish their login.
- Utilizing CSS trickery to change your profile to trick users.
- Loading larger payloads
- Silently draining your Steam Wallet funds.
- Spreading Malware via an auto-download.
How does this relate to Cross Site Scripting (XSS)?
The vulnerability is a simple XSS flaw, where JavaScript can be input by a user to the profile page, and be executed on the viewer’s browser. This situation is the perfect example of how an innocuous function can hide a potentially damaging flaw for many years due to a minor mistake by a developer or security tester. A simple encoding of user input and display could have prevented this.
Insecure Deserialization
Apache Struts 2 (Sep 2017)
Apache Struts 2, a popular framework used by many enterprise applications, was found to have a Remote Code Execution vulnerability, which could lead to malicious users gaining control over machines running these applications.
Why was this significant?
This issue affects every version of Struts using the REST plugin since 2008, and can be exploited by sending a crafted request remotely. This would allow a remote attacker to run arbitrary code on the machine. Java, and specifically the Struts framework, is popular within the enterprise environment, and this exploit could lead to high risk issues to the companies involved.
How does this relate to Insecure Deserialization?
The vulnerability is due to the XStreamHandler in the REST plugin, and the failure to filter file types from information sent from untrusted source.
Final thoughts
The OWASP Top 10 list is only a literal tip-of-the-iceberg representation of the increasing number of cyber threats facing us today. This list is expected to change as we see more transformations in the ways we work, play, and live our lives in these interesting times.
For instance, increased adoption of the cloud and the advent of new technologies like 5G will likely present more attack surfaces and therefore more cybersecurity challenges to organizations and individuals.
At the end of the day, cybersecurity affects all of us. We should therefore have an awareness of the potential harm to our digital lives.
If your organization is looking for a cybersecurity partner to help secure your business critical assets, contact uscontact us for a discussion.
Originally written by QuanHeng LimQuanHeng Lim




