As we discussed in part one, Sniper Forensics is an investigative methodology originally created by Chris Pogue and focused on delivering the most relevant answer as quickly as possible (Pogue, 2009). Follow logical pathways, build an investigation plan and execute.

To make this happen, Sniper Forensics is built around three logical principles that should drive almost all investigative decisions.
- Occam’s Razor
- Locard’s Exchange Principle
- The Alexu Principle
Occam’s Razor was originally coined by a 14th century English Franciscan friar called William of Ockham. William’s said, “among competing theories, the theory with the fewest assumptions is most likely correct.” (Kayne) In the modern world, we basically call this “Keep it Simple, Stupid” or the KISS principle.

In cyber-security, examples of this process are found when determining an attacker’s method for gaining unauthorized access to a victim’s server. Investigators should enumerate all of the possible infiltration vectors (leads) for the victim environment or specific system and use that list as a place start looking for evidence. Once we have enumerated the infiltration vectors, investigators should use their experience, knowledge, and Occam’s Razor to prioritize our leads.
For us the enumerated list of infiltration vectors normally looks something like this:
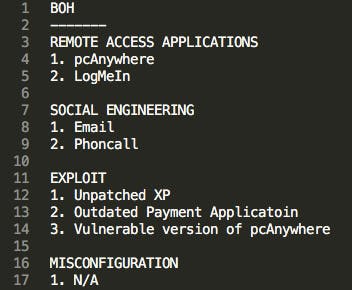
In this example, we determine that the four most likely infiltration vectors are two running remote access applications, some form of social engineering (maybe they downloaded the malware directly), possibly an exploit, or some misconfiguration that has not yet been discovered. Some findings will fall into multiple categories, such as a phishing attack that leads to the collection of valid credentials for a remote access application (Social Engineering and Remote Access Application).
In this case, after we listed the out the infiltration vectors, two things were immediately noticeable, based on experience. First, there are multiple remote access applications running in memory, our hypothesis is that they are in an “always on” configuration and will accept connections from anywhere. Second, one of those remote access applications is a vulnerable version of pcAnywhere that we have seen exploited on numerous cases.
At this point in our investigation planning process, it seemed most likely that I had found another instance where pcAnywhere had been used to gain access to this system. It was also likely that an attacker could have gained access via stolen or weak credentials for LogMeIn. It seemed least likely that an attacker had placed a phone call to convince the victim to go to a link or provide their password.
The important part here is that we used our experience and the available data as a tool to gauge where we might start our investigation. We applied Occam’s razor to our situation. As a result, we started our investigation around the remote access applications and let the data start showing us what happened. As it turned out in this case that we were not able to conclusively prove or disprove that pcAnywhere was compromised. However, LogMeIn was used to login to one of the systems from Romania at about 3am EST (GMT -5).
This is a good time for a quick segue, the number one rule of Sniper Forensics is follow the data to your conclusions, don’t ever draw a conclusion and force the data to fit in. As Chris would say, “That’s bad!”. As an example, we hypothesized that pcAnywhere was used to maliciously access the network. After completing the analysis, we’re just not sure; but it is possible. We didn’t selectively interpret the evidence to fit our theory.
I personally happen to agree with Chris on this one, the most unpleasant thing anyone of us ever have to do is follow up after an investigator has forced data into their conclusion and then prove them wrong. So don’t your fellow forensicators do that!
Edmund Locard was an interesting fellow and is now widely regarded as the father of modern forensics. Locard was able to form the first police laboratory in France during the early 1900s where he coined the most basic tenant of forensic science: “Every contact leaves a trace” (Petherick, Turvey, & Ferguson).

In physical crime scene, this means that a person leaves trace evidence in every room that they visit; it could be hair follicles, shoe prints, dead skin, etc. It also means that every room someone visits leaves trace evidence on their person, such as dust particles, paint transfer, or some object that is taken from a room, such a piece of hotel letterhead or a hotel pen. This concept is essentially the same in a digital crime scene; if someone were to login to a server from their laptop, evidence of the transaction exist on the server and different evidence also exists on the subject’s laptop.
It is up to us as forensic investigators to determine where that trace evidence may exist, how to extract it and what the evidence tells us. Sometimes we know the evidence exists but we have no way of actually collecting it or analyzing it, these are incredibly frustrating scenarios. When it’s a limitation in analytical ability, it is great to have a broad network of other forensic specialists for friends!
Moving along and continuing with the practical example of pcAnywhere; when the exploit is used to gain access to the vulnerable version of this software, it creates or overwrites an error file. No source IP address can be derived, no session data, only the modification date of the error file itself may provide a clue. This is trace evidence. It takes a lot of work to correlate with other data to yield a conclusive finding. In a malware investigation, it’s would be good to correlate the modified time of the pcAnywhere error file with the creation date of the malware or malware dump file. That might be enough to yield a strong circumstantial finding, if we’re lucky.
It’s also important to remember that the “Absence of evidence is not the evidence of absence”. (Turvey, B.E. 2008)
The Alexiou Principle is something Chris documented after working with Mike Alexiou (previously of Terremark). I always argue that this is the most important principle because it’s the one the helps keep our investigators focused and is the light at the end of the analysis-paralysis-tunnel.
The Alexiou Principle itself is a set of four questions, something I collectively call a question set:
- What question am I trying to answer?
- What data do I need to answer that question?
- How do you extract that data?
- What does the data tell you?
I’ve taught Sniper Forensics for a long time and I am always leading training efforts for Cyber Operations staff here at Horangi. The most common question I get when discussing this principle is, “what type of question do I ask?”. I might take it for granted, but I believe this is simple once you get the hang of it. For me I ask questions in the same way I set goals.
For me, it is best to have a narrow long term vision and have clearly defined and achievable short term goals that help you get to the end. In this spirit, I break question sets into levels starting at the top level question and ending at the bottom level questions. There are any number of middle questions between the top and bottom. .
Top level questions define your overall investigative goal. Bottom level questions help you derive actionable answers. Middle level questions help you get from the top to the bottom. The idea is to start with a top level question set and work your way down, enumerating as many possibilities as is feasible, until you have a list of bottom level question sets that outline exactly which data you need to examine.
It’s really easy for this to get out of control and become unwieldy, but with a little bit of time and patience, you can master this technique and start cranking out investigations much faster than any other team member. I’ve got a long list of professional references that will attest to it!
Also, try not to ever go from the bottom to the top! We call that shotgun forensics and it leads to analysis paralysis which stymies investigative progress.
In most scenarios, I have 6 top level questions:
- Did an attacker gain unauthorized access to our client’s Environment?
- How did the attacker reconnoiter the environment?
- How did the attacker infiltrate the environment?
- How did the attacker move throughout the environment?
- How did the attacker aggregate data?
- How did the attacker exfiltrate data?
For each question, I build out the question set according to the Alexiou Principle. Then I continue to write questions until I figure out exactly which file(s) from which system I need to look at.
Building out a top level question set looks like this:
- Did an attacker gain unauthorized access to our client’s environment? ← this is a top level question
- What data do I need to answer that question? ← the rest of these are part of the top level question set.
- Did the attacker gain unauthorized access to our client’s environment via a remote access application?
- Did the attacker execute a social engineering attacker?
- Did the attacker exploit a vulnerability in an environment?
- Did the attacker exploit a misconfiguration in the environment?
- How do I extract this data?
- What does this data tell me?
A middle level question might looks like this:
- Did an attacker gain unauthorized access to a remote access application?
- To answer this question I gather a list of remote access applications that exist on all systems.
- I collect this from a list of running processes, installed components in the registry, and from known directory locations on disk.
- After examining this data, I normally find something like:
pcAnywhere and LogMeIn were installed on disk and running in memory
A bottom level question set would be:
- Did an attacker gain unauthorized access to the environment via pcAnywhere?
- To answer this question, I need the log files and error files from pcAnywhere which are located in the C:\Program Data\Symantec\pcAnywhere folder.
- These files are plain text and can be viewed in a normal text editor.
- After examining this data, I found that:
- pcAnywhere did not have logging enabled and no error file was created meaning it is not possible to determine if the pcAnywhere application was ever used ether legitimately or maliciously.
Since I didn’t have a conclusive finding here, I will continue on with LogMeIn and every other infiltration vector I can find. Sometime you’ll know an attacker was on the system but there’s just no evidence on how they gained access.
Don’t get frustrated, drill down for every top level question until you get to some evidence and then document your findings! It takes a bit of practice and some getting used to, but once you get good at building out an investigative plan you can crank through cases very quickly and accurately. You can present your findings with confidence too!
References
Pogue, C. (2009). Sniper Forensics “One Shot, One Kill” — SANS Institute. Retrieved March 30, 2017, from https://digital-forensics.sans.org/summit-archives/2010/2-newell-spiderlabs-sniper-forensics.pdf
Turvey, B.E. (2008). Criminal Profiling: An Introduction to Behavioral Evidence Analysis. Elsevier. p. 267. ISBN 9780123741004. LCCN 2008274380
Petherick, C. E., Turvey, W. A., & Ferguson, B. E. (n.d.). Edmond Locard. Retrieved March 30, 2017, from http://aboutforensics.co.uk/edmond-locard/
Kayne, S. (n.d.). Retrieved March 30, 2017, from http://www.iep.utm.edu/ockham/



