SOC 2 compliance controls are a series of standards designed to help measure how well a given service organization conducts and regulates its information. SOC 2 is a framework applicable to all technology service or SaaS companies that store customer data in the cloud to ensure that organizational controls and practices effectively safeguard the privacy and security of customer data. It is also an auditing procedure that ensures your service providers securely manage your data to protect the interests of your organization and the privacy of its clients. For security-conscious businesses, SOC 2 compliance is a minimal requirement when considering a SaaS provider.
What is SOC 2 Compliance?
SOC 2 is a voluntary compliance standard for organizations, created by the American Institute of CPAs (AICPA) which specifies how organizations should manage customer data. Before 2014, cloud vendors only had to meet SOC 1 compliance requirements. As companies increasingly leverage the cloud to store customer data, SOC 2 compliance is becoming a necessity for a wide variety of organizations. SOC 2 ensures that a company’s information security measures are in line with the unique parameters of today’s cloud requirements.
Why is SOC 2 Compliance Important?
Compliance with SOC 2 requirements indicates that an organization maintains a high level of information security. Strict compliance requirements ensure that sensitive information is handled responsibly.
Complying with SOC 2 checklist includes controls covering safety standards to provide:
- Access control: Logical and physical restrictions on assets to prevent access by unauthorized personnel.
- Change management: A controlled process for managing changes to IT systems, and methods for preventing unauthorized changes.
- System operations: Controls that can monitor ongoing operations, detect and resolve any deviations from organizational procedures.
- Risk mitigation: Methods and activities that allow an organization to identify risks, as well as respond and mitigate them, while addressing any subsequent business.
However, if your organization operates in the financial or banking industry where privacy and confidentiality are paramount, you may need to meet higher compliance standards.
In addition to the basic security principles, here is how to comply with other SOC 2 principles:
- Availability: Seeking answers to questions like, can the customer access the system according to the agreed terms of use and service levels?
- Processing integrity: If the company offers financial or eCommerce transactions, the audit report should include administrative details designed to protect the transaction. For example, is the transmission encrypted? If the company provides IT services, such as hosting and data storage, how is data integrity maintained within those services?
- Confidentiality: Are there any restrictions on how data is shared? For example, if your company has specific instructions for processing personally identifiable information (PII) or protected health information (PHI), it should be included in the audit document. The document should specify data storage, transfer, and access methods and procedures to comply with privacy policies.
- Privacy: How does the organization collect and use customer information? The privacy policy of the company must be consistent with the actual operating procedures. For example, if a company claims to warn customers every time it collects data, the audit document must accurately describe how warnings are provided on the company website or other channels.
SOC2 Compliance Mapping Clauses
Clause CC6.1.B: Restricts Logical Access
Logical access to information assets, including hardware, data (at-rest, during processing, or in transmission), software, administrative authorities, mobile devices, output, and offline system components is restricted through the use of access control software and rule sets.
Mapped rules include:
- (AWS) S3 Bucket Not Configured with Public Access Block
- (AWS) Lambda Function with Full Administrative Privileges
- (GCP) BigQuery Datasets Publicly Accessible
Clause CC7.2.A: Implements Detection Policies, Procedures, and Tools
Detection policies and procedures are defined and implemented, and detection tools are implemented on Infrastructure and software to identify anomalies in the operation or unusual activity on systems.
Procedures may include:
(1) A defined governance process for security event detection and management that includes the provision of resources
(2) Use of intelligent sources to identify newly discovered threats and vulnerabilities
(3) Logging of unusual system activities.
Mapped rules include:
- (AWS) CloudTrail S3 Bucket Access Logging Not Enabled
- (AWS) CloudWatch Log Metric Filter and Alarm for Security Group Changes Not Enabled
- (GCP) Log Metric Filter and Alerts for VPC Network Route Changes Not Enabled
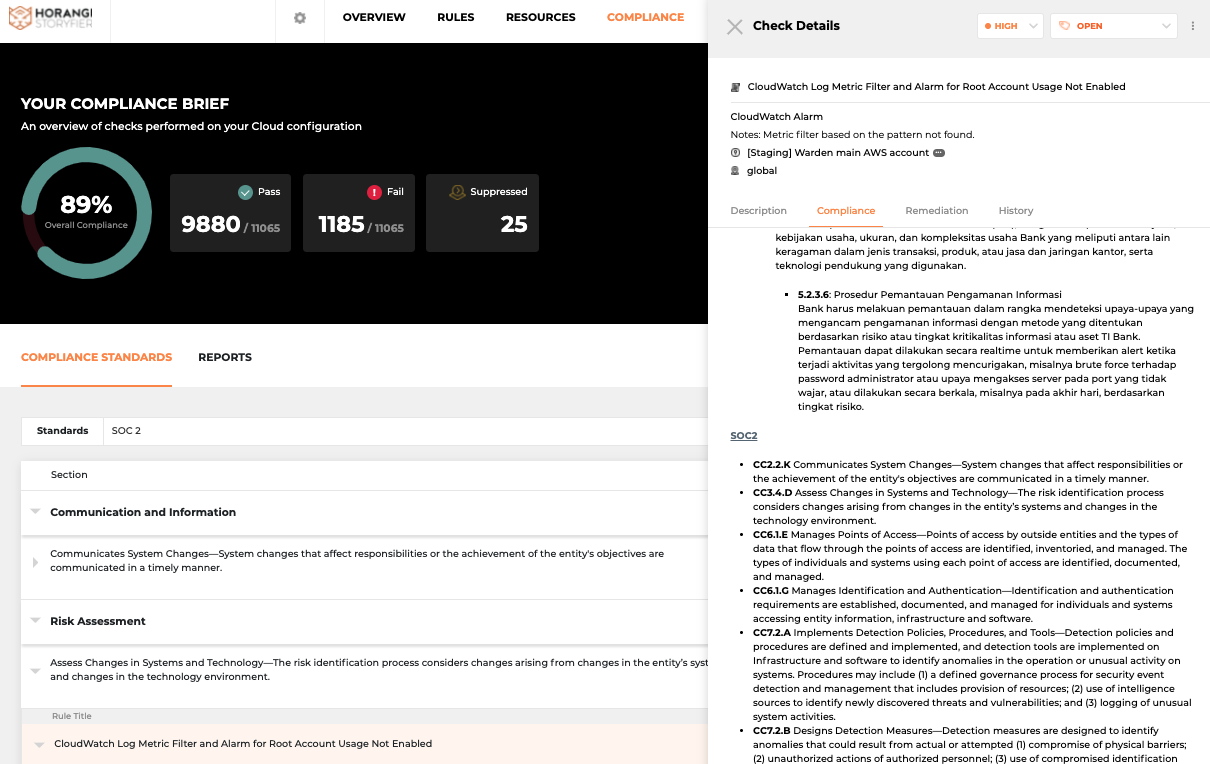
SOC 2 Compliance rules on Warden
What This Means
1. Warden helps to surface gaps in your cloud infrastructure when it comes to SOC 2 compliance. With playbook and one-click remediation, you can quickly resolve these gaps, bringing you closer to a SOC 2 compliant status.
2. These Warden updates will also help to monitor and detect access restrictions, thereby decreasing your attack surface, and complying with the highlighted clause CC7.2.A, as mentioned above.
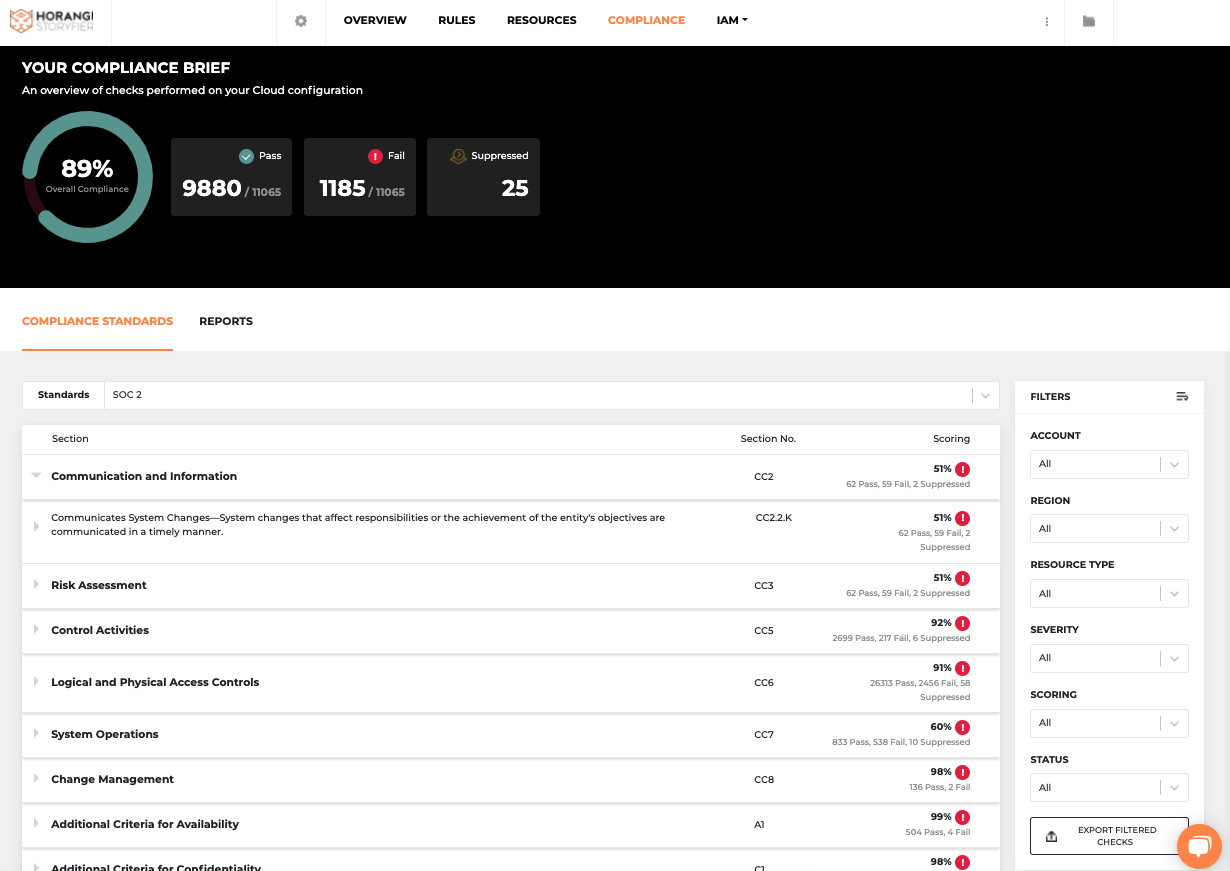
Warden Dashboard with SOC 2 compliance view
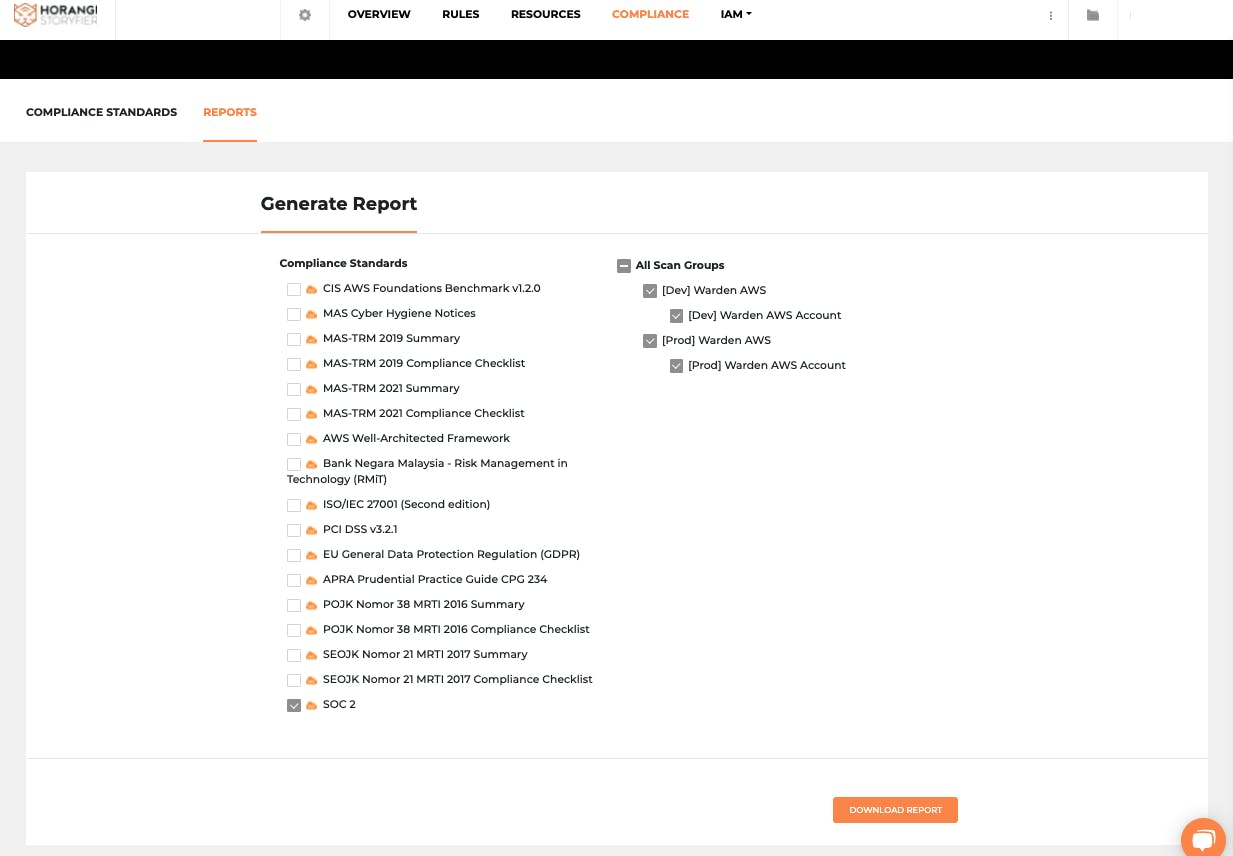
Generating a report on Warden with SOC 2
Conclusion
Being SOC 2 compliant assures your customers and clients that you have the infrastructure, tools, and processes to protect their information from unauthorized access both from within and outside the firms. This builds operational trust and also ensures the safety of their crown jewels. And as the compliance regulatory environment continues to evolve, Horangi Warden is constantly expanding its compliance library to serve customers across the globe. To stay updated with the latest additions to Warden’s compliance automation stack, you can visit our blog. You can also fill up this form to schedule a customized demo to see how Warden can help with all your cloud security needs.




