It was the weekend, so I thought it was finally time to catch Squid Game, the Korean series on Netflix that everyone has been raving about. Just 5 minutes into the series made me realize the striking similarity between the game and cybersecurity. As the narrator explained the rules of the game, I associated how real-world cybersecurity also has these two important concepts that we hear almost every day - Offense and Defense.
These days, organizations can get attacked on more fronts than ever before. Each application of cloud-based technology or mobile technology presents a new opening through which attackers seek to gain access to your organization’s valuable information (crown jewels). Let me walk you through how Horangi can help you counter some potential cyber threats and enforce network defenses with our in-depth services (Offensive, Strategic, Threat Hunting) and a tailored approach to minimize your attack surfaces.
A Quick Recap: Offense and Defense (No Spoilers, I Promise)
The rules of Squid Game are explained right at the start using a group of children playing the game as an illustration. Etched on the ground is a perimeter defined by lines that together look like the outline of a squid, along which the children playing as defenders will travel on. They will have to traverse the perimeter to defend against the other group of children who will be the attackers in the game. The attackers are free to move around the perimeter to probe for weaknesses in the defenses, with one caveat -- they can only do so by hopping on one leg. Their objective is to get past the defenders by any means necessary; they are free to run around on both legs once they get past the defenders.
The end-game is for an attacker to defeat a defender named the ‘Inspector Royal’ by touching the ‘squid head’ with his feet. The attackers win the game if one of them manages to do that, but they will ‘die’ if the defenders push them out past the perimeter.
How is it Related to Cybersecurity?
It occurred to me that there are quite a few similarities that one can gather between Squid Game and Cybersecurity.
- Perimeter resembling a squid: That’s your network perimeter
- Defense: Tools and people that have been deployed to guard the perimeter, like your security team and native or third-party security tools
- Offense: Attackers that try to get past your network defenses and get access to your important data

Squid Game: Defense and Offense
Time to Up Your Game
Did you know that an average cost for a potentially compromised record is $225 and it is significantly higher for industries like healthcare ($380 per compromised record data) and financial services ($336 per file)?
Now imagine a scenario where an attacker gets their hand on millions of your customer’s data? If you don’t get better at playing the Squid Game, then you can sustain an average loss of US$4.24 million in a single breach and that’s just the monetary effect. It also leads to severe reputational damage and loss of trust from customers.
How Can You Up Your Game?
- Get started by building your defenses
Once you have identified your critical assets and sensitive data, you need to start building up your defenses around them. Whilst nothing is ‘100% unhackable’, the more appropriate and effective defensive measures you put in place, the better equipped you are to address cyber threats. Time and budget constraints are always going to be a factor in your cybersecurity efforts and most companies usually have limited resources to work with. When this is the case, your focus needs to turn to protecting your crown jewels (the most sensitive information assets). - Segregate your networks and lock your crown jewels away
A flat network can be an attacker’s dream and any breach could allow attackers easy access to sensitive data, without the need to jump between networks or systems. By segregating your network, you make the job of the attacker more difficult and increase the chances of their activity being discovered. Once your network is segregated, you’ll then need to control access. There are several ways you can do this, and Horangi can help you navigate user roles/permission privileges and how to set them up correctly with our flagship cloud security product Warden. - Build defense-in-depth
Putting up defenses around your crown jewels is obviously key, but are you putting up defenses throughout your business? Defending your network perimeter should be like defending a castle, if an attacker gets through one set of defenses there should be another set waiting for them. This is called defense-in-depth and the more effective defenses you have in place throughout your network, the more difficult you make it for attackers to gain access.
How Can Horangi Help?
How do you know if your cybersecurity defenses are truly effective?
You need to test them!
Having your work tested can seem like a daunting prospect, but that’s not the case here. Testing is to support your efforts, ensuring that your business is as protected as it can be and allowing you to make informed decisions about your next steps. And this is the part that Horangi can help you with.
With our extensive experience in offensive security and our use of best-in-class threat detection software, we can help you get better at playing your cybersecurity Squid Game by thoroughly training, testing, evaluating, and helping you implement key cybersecurity practices. We play both ‘Offense’ (to probe for weaknesses from outside) and ‘Defence’ (to assess the comprehensiveness of existing security measures) on your Squid/Network perimeter and determine how strong your network firewalls and access controls are, if you have any vulnerabilities or exposed attack surfaces that can be exploited, and much more.
We also help you systematically set up a strong cybersecurity foundation and foresee loopholes in your security stack. With us, you will get comprehensive reporting and our expertise to understand the current state of your overall cyber resilience and perceptive insights to improve your security posture. Here’s what you can expect with Horangi’s expertise in your arsenal.
Offensive Services: Our cyber experts will use real-world adversarial techniques like Penetration Testing, Red Teaming, Spear Phishing, Source Code Review to identify vulnerabilities in your defense, in order to improve your security posture. All engagements usually start with a reconnaissance phase which includes performing Open Source Intelligence (OSINT) on the organization such as the network layout, employees, technology stack, harvesting email addresses, social media, passwords leaks, and even minute details such as email signature, lanyards, etc.
Horangi Offensive Cybersecurity Services
Strategic Services: Horangi's holistic cybersecurity methodology that tackles the cybersecurity problem at its core can help you accelerate your security maturity. With tailored strategies put forth by Horangi consultants based on Cybersecurity Assessment, Ransomware Defense Assessment, and CISO-as-a-Service, you can cut through security complexities and follow a roadmap that generates organizational efficiencies.

Horangi Strategic Cybersecurity Services
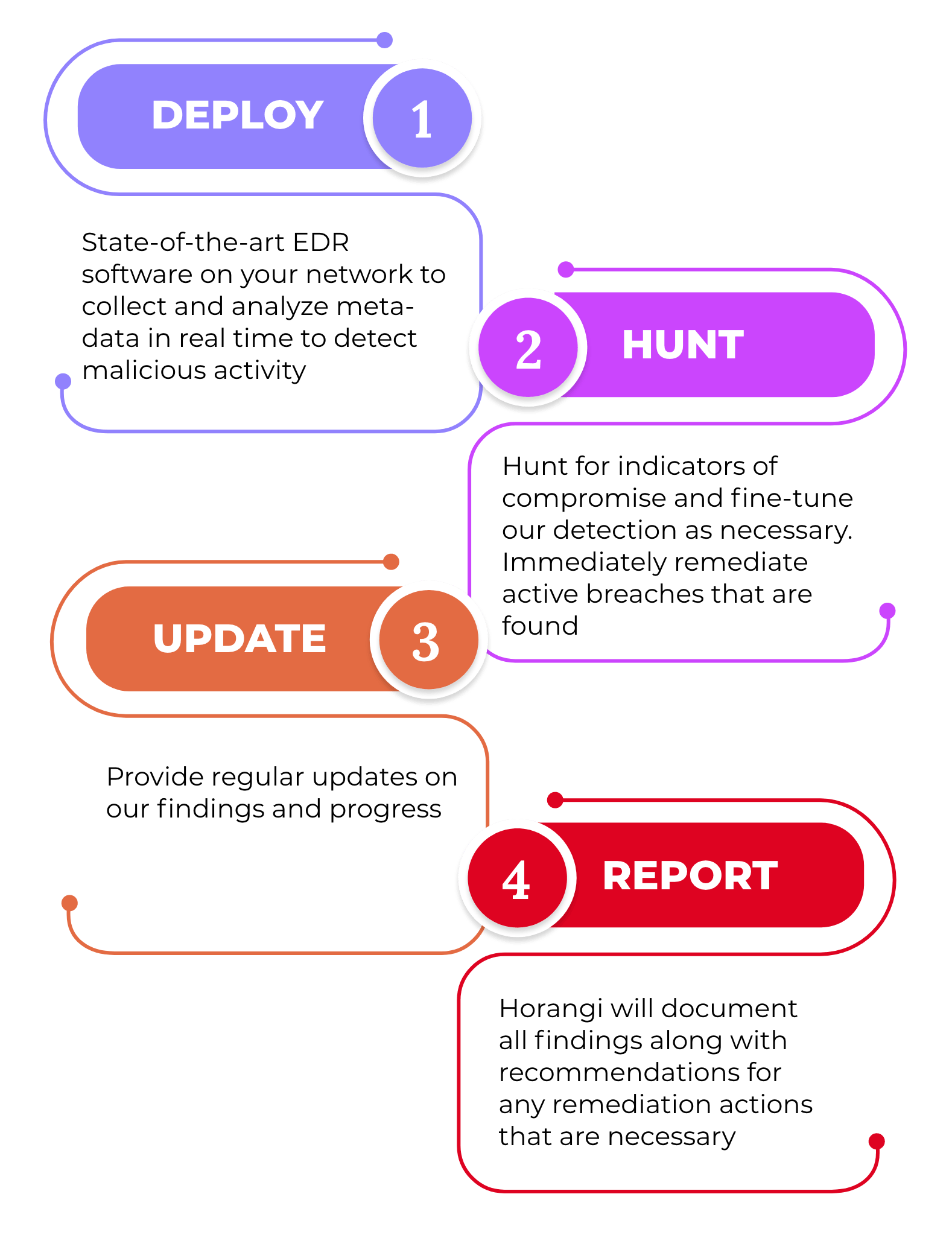
Threat Hunting: Threat Actors could be in your network today. Horangi’s Compromise Assessment examines your entire network infrastructure and endpoints for undiscovered vulnerabilities, signs of unauthorized access, and traces of suspicious activities. Paired with our best-in-class Next-Generation Antivirus (NGAV), Asset Management, Cloud Workload Protection Platform (CWPP), and Endpoint Detection and Response (EDR) software to actively hunt for hidden threats within your network. You will receive regular and timely updates from our team during the entire exercise.
Our 4 Step Methodology for Threat Hunting
Don’t Let Security Be A One-Off Exercise
Cybersecurity can sometimes be seen as a tick box exercise and there is often a belief that a one-off, annual security assessment is enough to keep a company protected until it’s time to test again next year. This isn’t the case and just because you’ve been tested today doesn’t guarantee you won’t get breached tomorrow. Attackers are always looking for new attack routes and no company, or technology is ‘unhackable’.
Given enough time, information, resources, and dedication, attackers can always find a route. Cybersecurity improvement efforts, therefore, need to be ongoing, helping keep your company one step ahead of these malicious threats. And have an edge in this real-world Squid Game. Let us help you play the cybersecurity game with informative tactics and comprehensive insights to minimize your chances of having a breach in your network. At the completion of our engagement, Horangi will provide actionable insights and recommendations that will help you increase your organization’s resilience against cyber attacks.