What is Warden REST API?
This feature release opens up Warden to numerous possibilities and automated workflows. Using Warden REST API can enhance your existing security orchestration, automation, and response solutions to reduce complexity and human error. This feature also comes in handy to aggregate and share data for reporting, visualization, correlation, or alerting.
How can WARDEN POST API help you?
We have already talked about how using Warden API is very straightforward and can be done within minutes. With the new Warden POST API, you can further shorten the time to push updates to any of your findings.
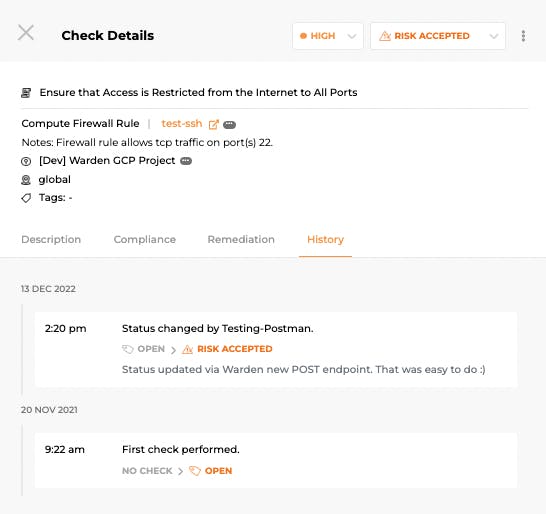
Update to a finding done through POST API
This latest feature can help you with the following use cases:
- Update the severity of a group of findings from “High” to “Medium”
- Update the status of a group of findings from “Open” to “Risk Accepted”
- Specify expiration date for the “Risk Accepted” status for another round of risk assessment
- Include remarks to accompany any changes above for audit purposes
How to Get Started?
Getting started with the Warden API is simple - just head over to our support portal to learn how to generate your first API key.
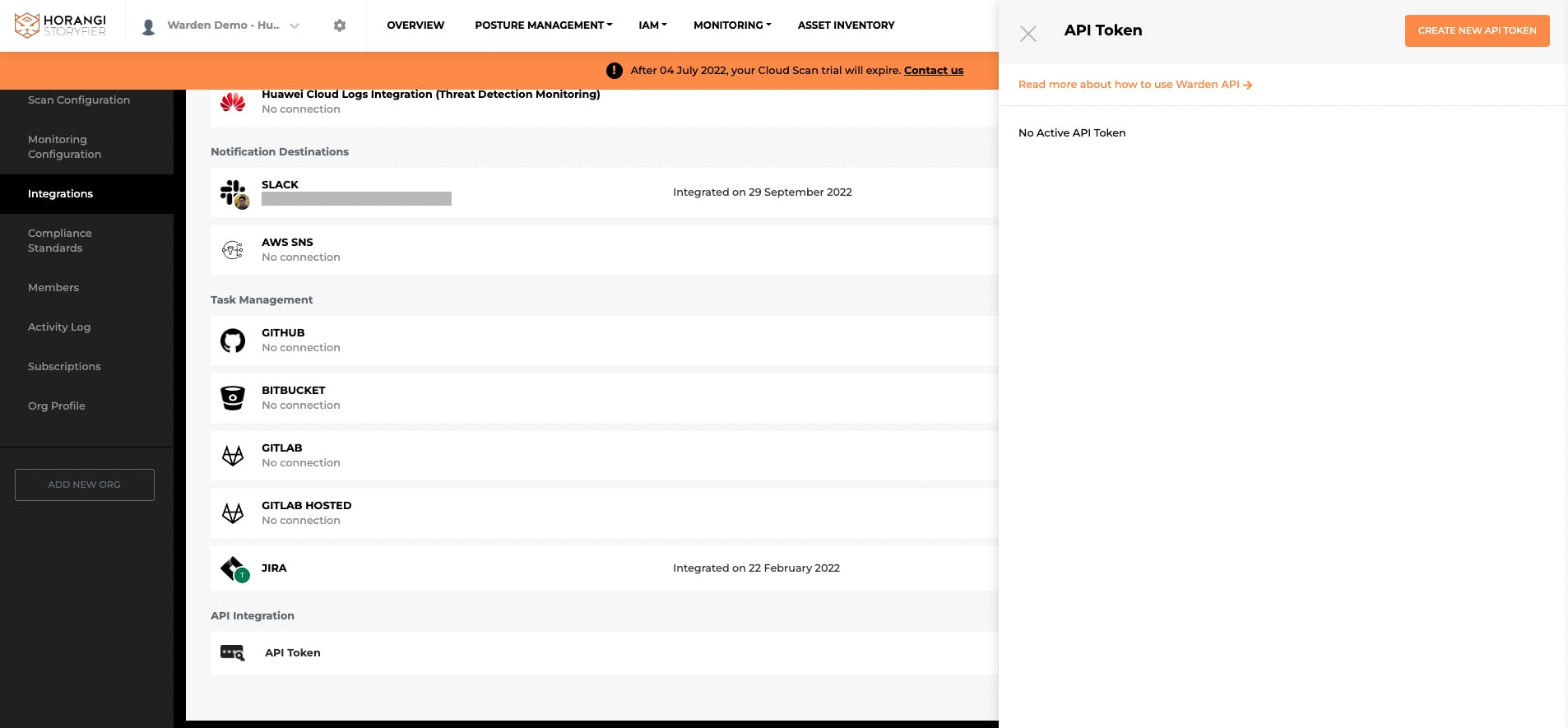
Generating a New API Key in Warden
Once you have done the API integration, reach out to our Warden support staff so that we can run through the do’s and dont’s when using our update API. Remember: with great power, comes great responsibility!
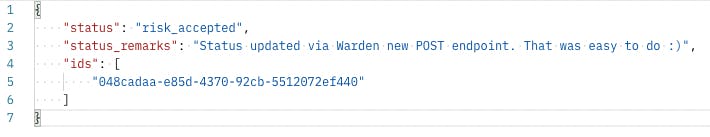
Sample of the POST API body
Conclusion
Unleash the full potential of your multi-cloud platform security with Warden, the only cloud security solution with CIEM, CSPM, Real-Time Threat Detection, Vulnerability Remediation, and Compliance Automation capabilities. If you are excited to know more about how to secure your cloud, drop us a line here.




