What are the features being released?
In the new IAM Security Risk section, users can immediately review the list of all excessive permission risks found in the organization. These excessive permissions risks are defined by the unused services and permissions found in the policies for each “identity” in the last 90 days.
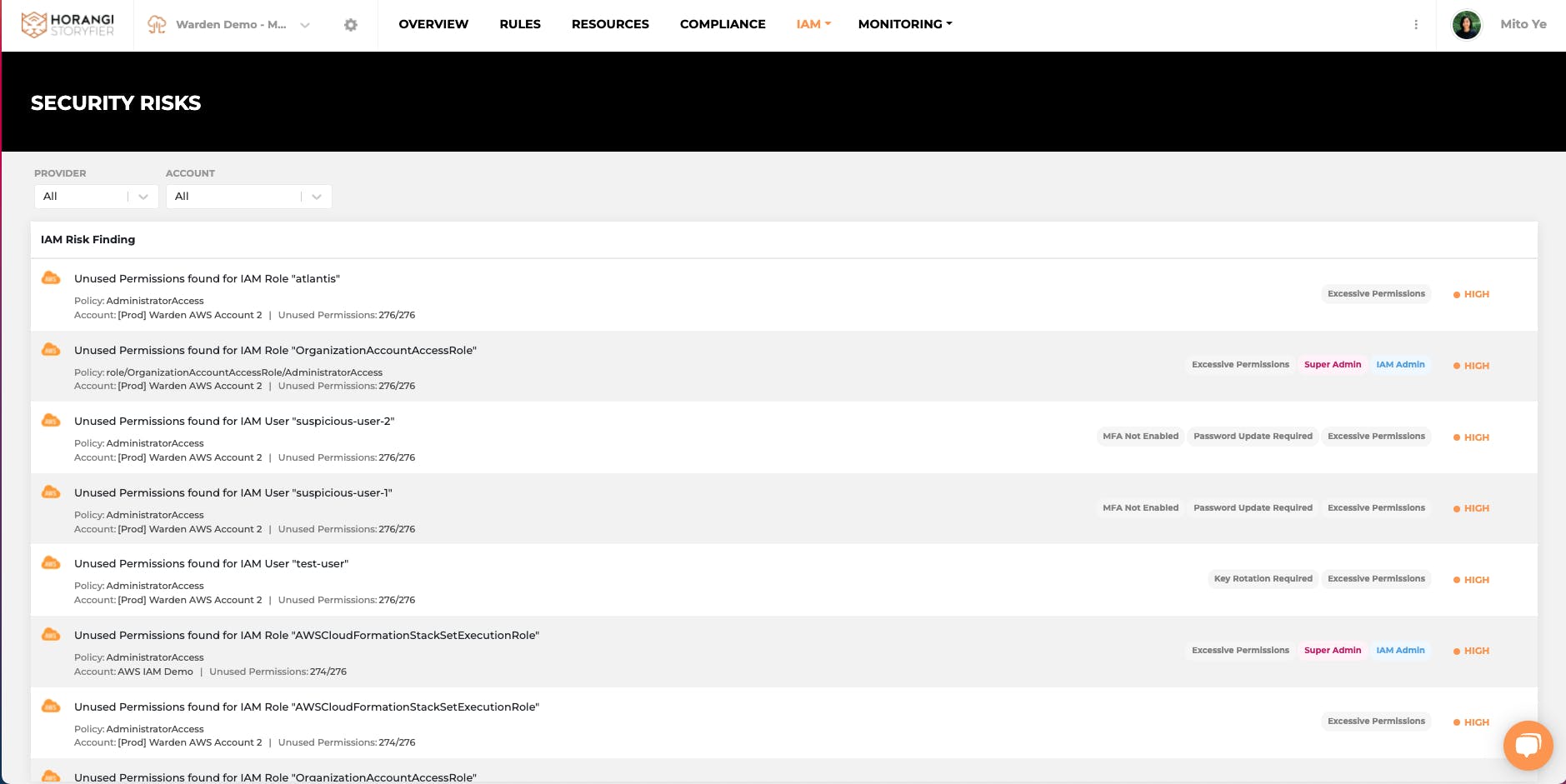
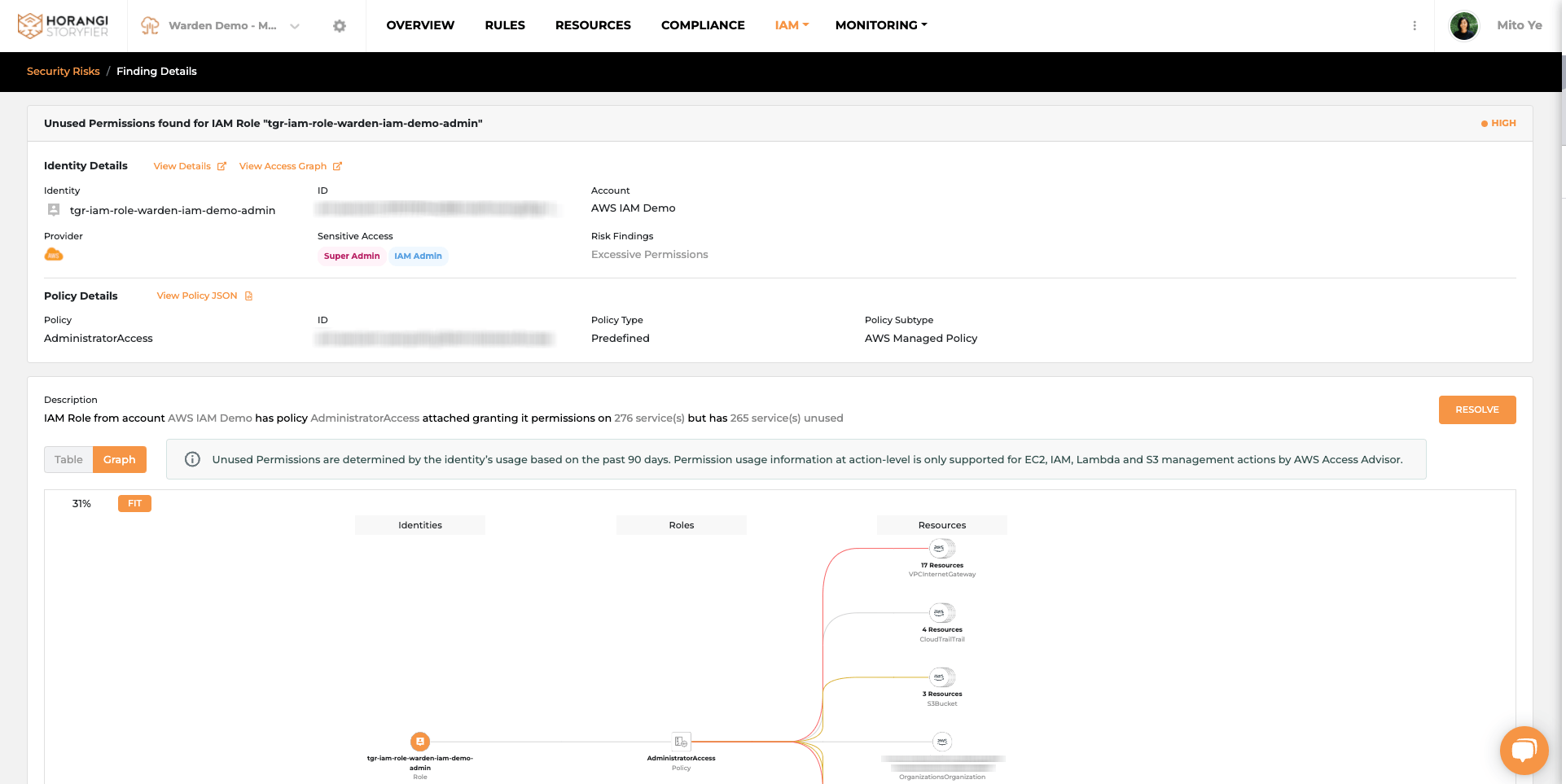
For each of these excessive permissions found, users can review not only “what-they-are” in a clearly labeled tabular format, but also “how-they-were granted” in an initiative graphical format.
After reviewing, users can then proceed to quickly rightsize the permissions with recommended steps. All users need to do is just simply copy and paste new policies or update the existing ones with the recommendation.
With the help of Warden IAM excessive permission and rightsizing feature set, adopting the Principle of Least Privilege (PoLP) can be this simple.
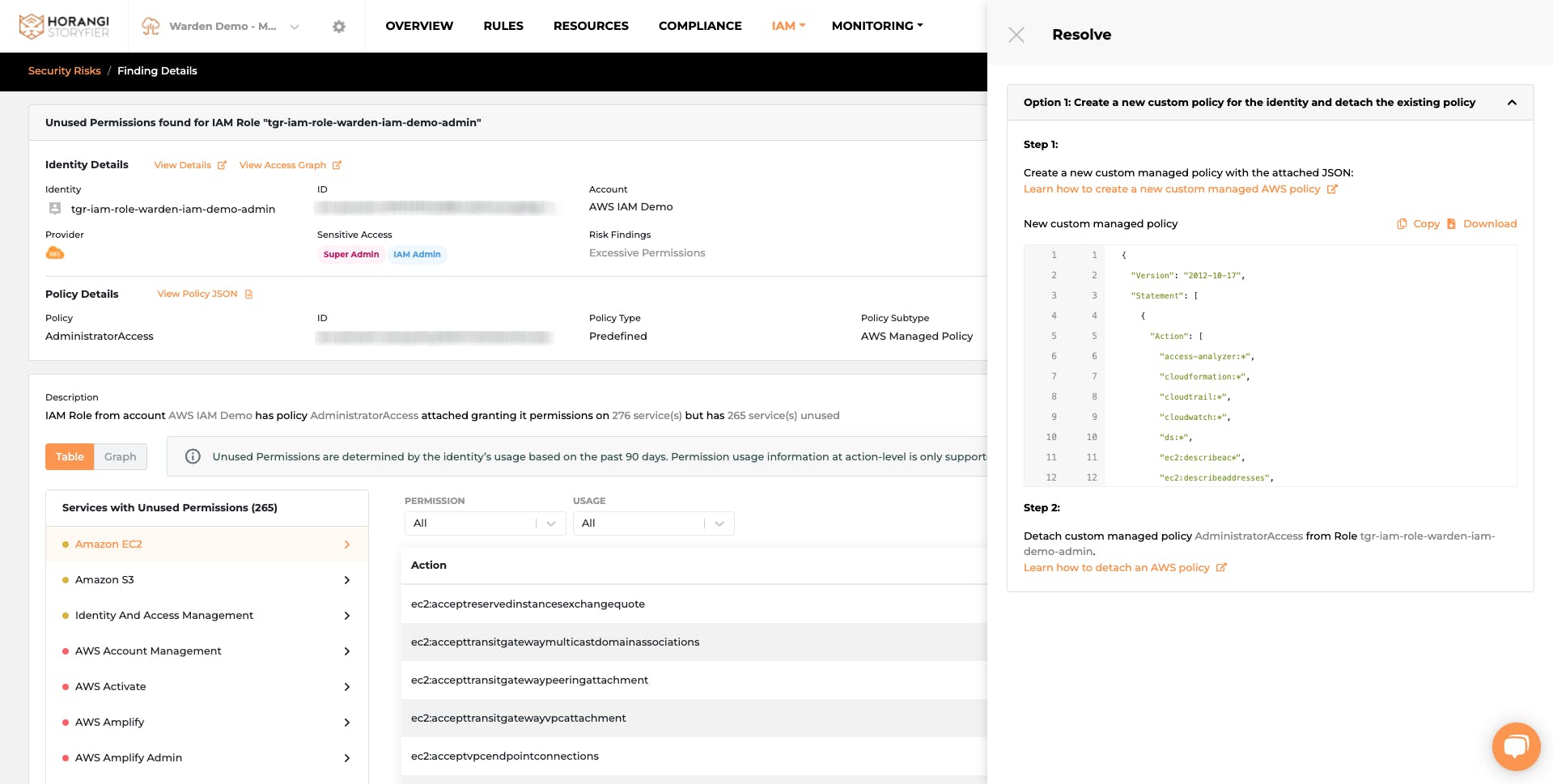
If you are worried about additional impact, we’ve got that covered too. We’ve also added this additional information at the recommendation step, so that you and your team can always make an informed and confident decision on rightsizing.
Why is this feature needed?
Why should people care about excessive permission?
- Excessive permissions could lead to additional attack surface
- It can increase your exposure to the attack
- It makes adopting the principle of least privilege easy
Why would there be excessive permissions?
- With the increasing number of identities and complex ways of granting the permissions, managing the permissions becomes harder and more time-consuming
- Often people granting the permissions do not have a security mindset nor are they cloud security-experts. They just want to get the job done (quickly) and end up granting excessive permissions without knowing it
- Adopting the principle of least privilege is not easy, it requires the study of past usage to make a confident call. Hence, Warden IAM takes care of the examining of historical data parts automatically and provides you with suggestions that are context-rich, while users just need to simply follow through
What value does it add for our customers?
No expertise, no problem
Our graphical view can help you gain Instant clarity on the excessive permissions and their potential impact on all the resources in your organization.
Save time, minimize the headache
Resolving the excessive permissions does not have to be time-consuming. Just simply copy and paste the proposed policies which are recommended intelligently based on the analysis of historical data. The cherry on the cake here is that you can also easily preview the potential impact in a graphical format before the update.
Note: Excessive permissions and rightsizing feature is currently only available for AWS customers.
Conclusion
We hope that this blog post will help you make the most of your Warden IAM. In case you haven’t taken Warden for a spin yet and you are having trouble answering “who has access to my crown jewels and how did they get the access?” then get in touch with a Horangi Specialist for a quick demo of Warden, a comprehensive cloud security tool with IAM, Threat Detection, and Posture Management capabilities.




