New Feature: Warden Compliance
With more organizations migrating to cloud infrastructure, there are also new risks to company and personal information that come along with it. Making sure that organizations comply with governing laws and regulations is one of the biggest challenges in cloud security.
It’s no secret that the cost of non-compliance is extremely high. Here at Horangi, we believe in being proactive about managing compliance instead of scrambling when it’s too late.
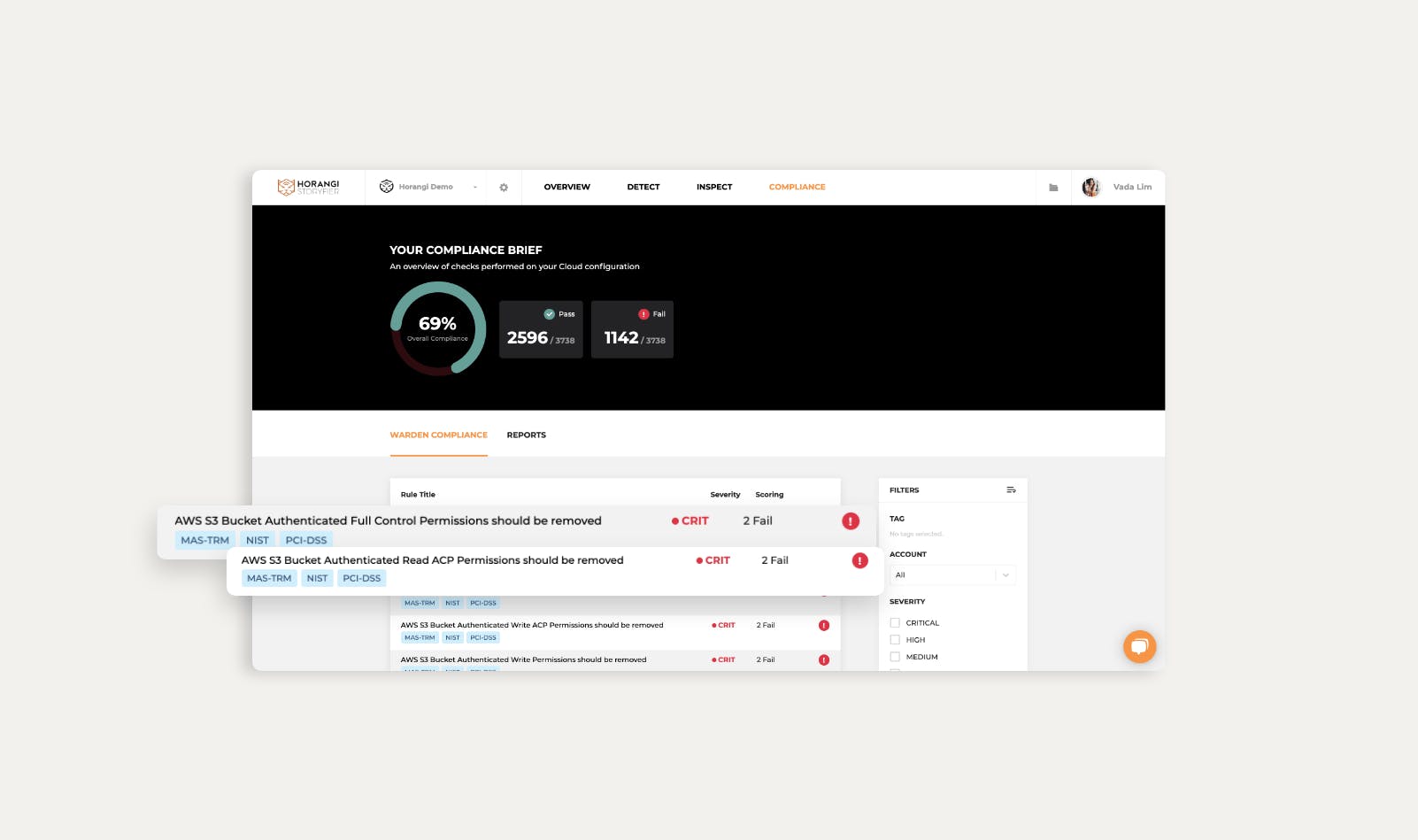
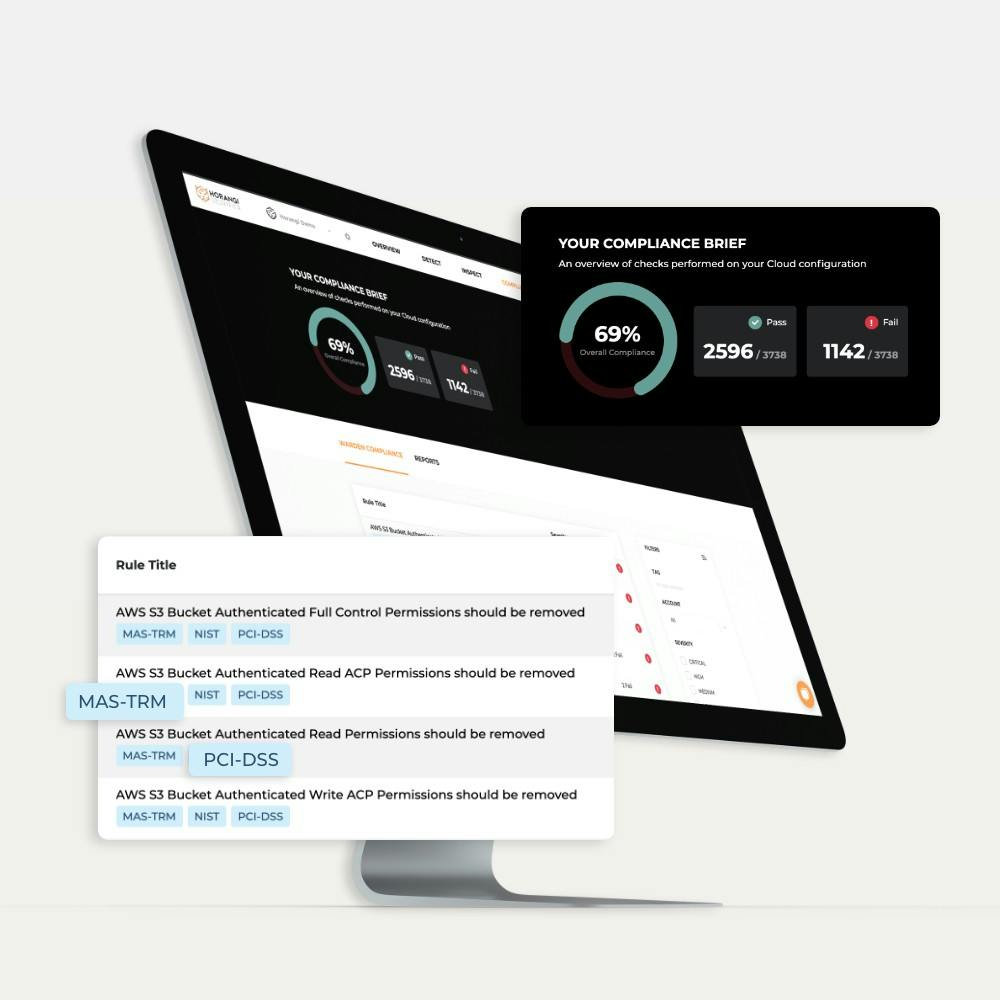
In line with this, we released a new Storyfier Compliance feature that gives you a quick view of your compliance risk posture with the ability to zoom in on what issues need to be resolved to stay compliant.
We also tagged specific compliance standards that our findings would have an impact on. Specifically, we added tags for the following standards:
- CIS-AWS
- MAS-TRM
- MAS Cyber Hygiene Notices
- PCI DSS
- NIST
- GDPR
Apart from CIS-AWS control mappings for we added during the previous release, we also added detailed mappings of our checks to specific control items of MAS-TRM and MAS Cyber Hygiene.
The Monetary Authority of Singapore - Technology Risk Management (MAS-TRM) guidelines are regulations covering all Singapore-based financial institutions that focus on security best practices to protect financial and personal data.
The MAS Cyber Hygiene Notices, on the other hand, are legally-binding subsets of MAS-TRM focused on specific industries.
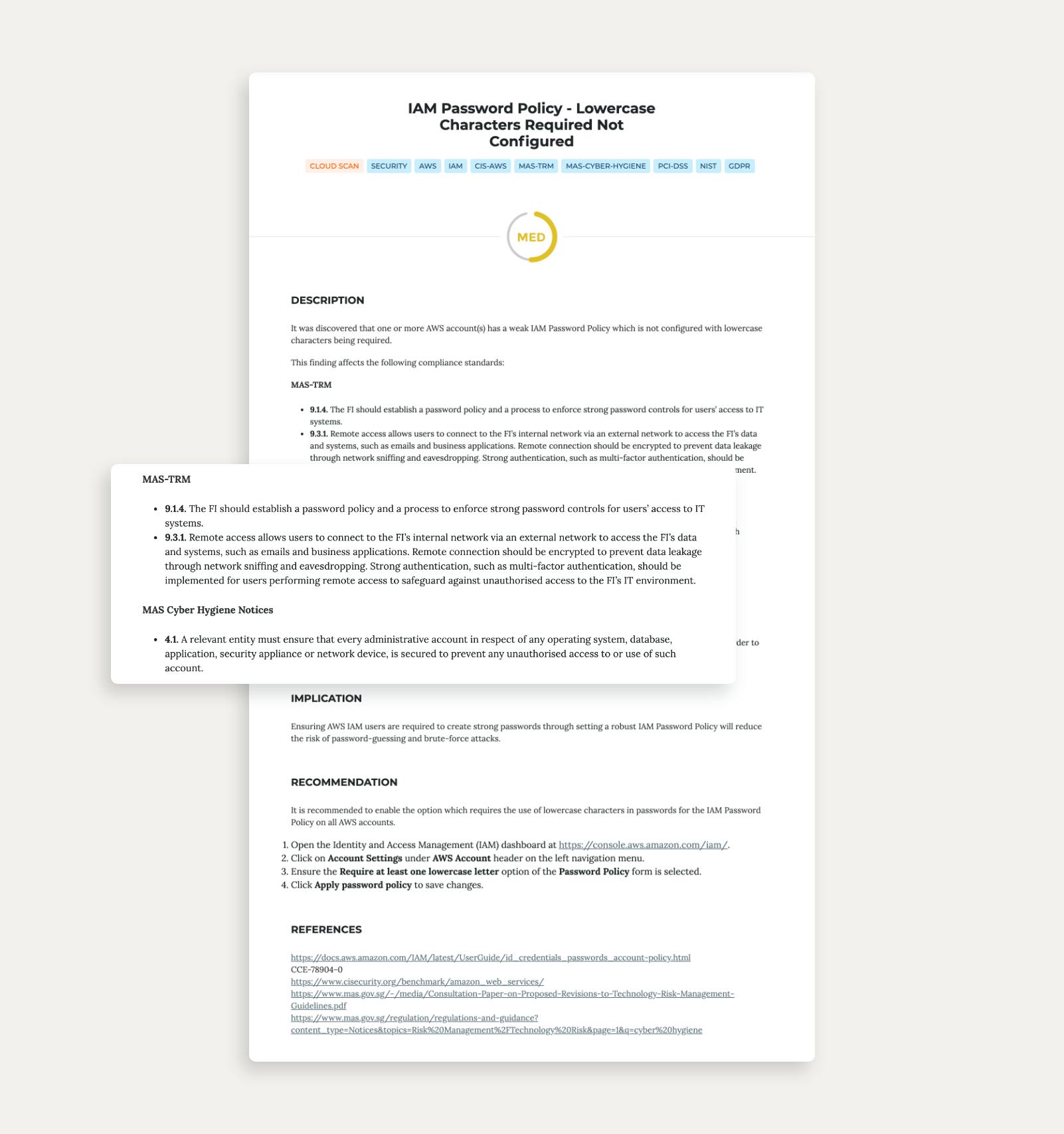
All Warden findings now contain information about which specific MAS-TRM and MAS Cyber Hygiene regulations target that particular finding. You can even find links to the full standards for your reference.
Control mapping for other compliance standards will follow over the coming months.
Compliance Report Generation
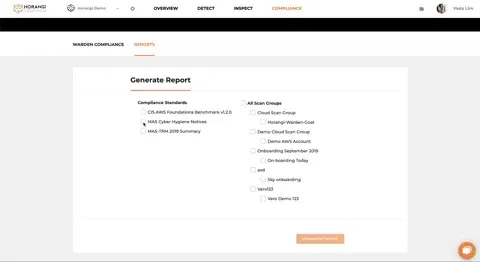
Reduce the time you spend making reports and export compliance information you need through our report generation feature.
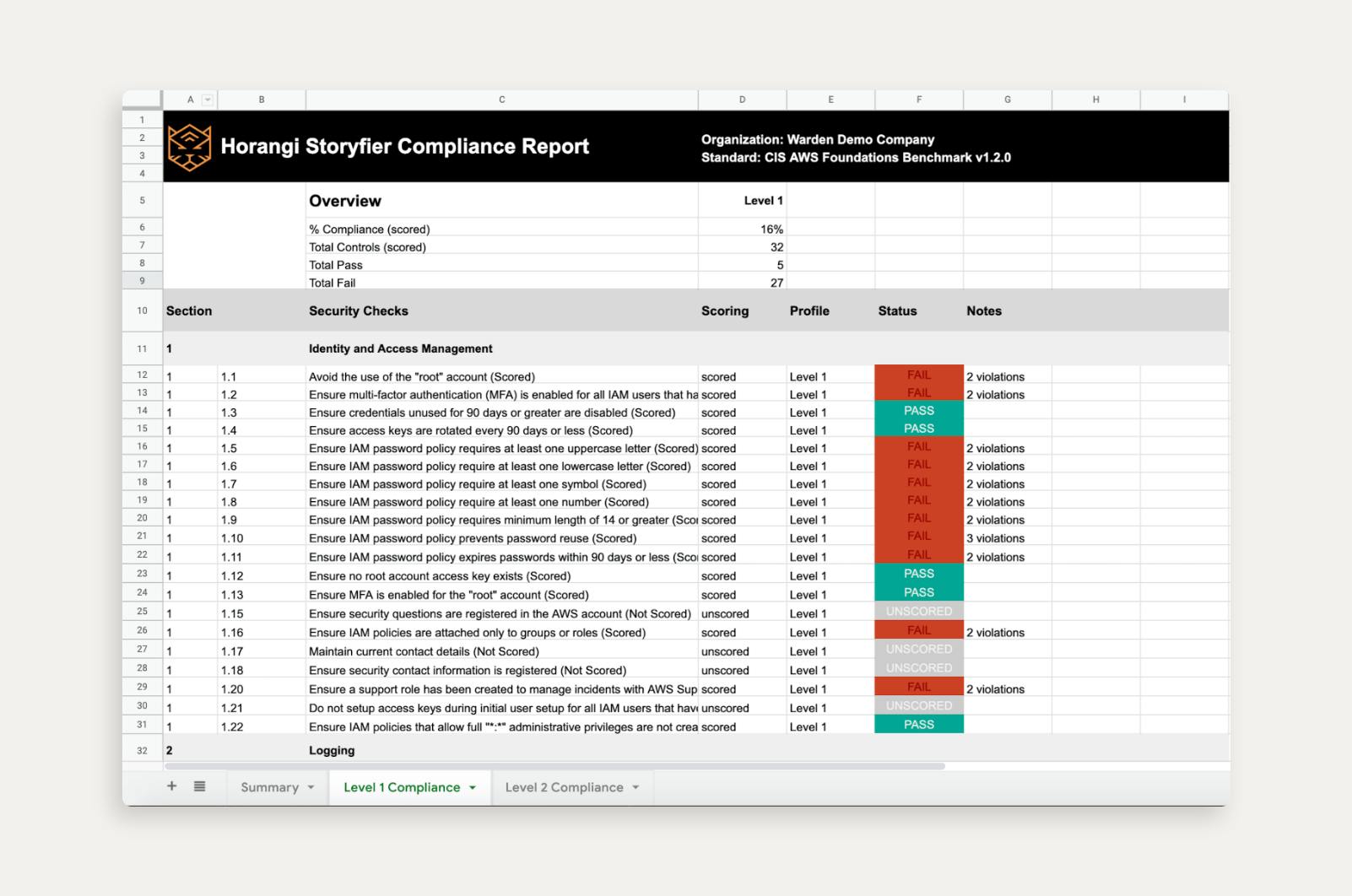
The compliance reports you generate will show you what checks have been performed for each control item covered by Warden, with how many of each have passed or failed. You can use this report to communicate your compliance posture internally, or as part of the evidence, you send to an external auditor or certifying body.
You can generate a report for all the checks Warden performed for the following compliance standards and choose which AWS accounts to include in your report.
- CIS-AWS
- MAS-TRM
- MAS Cyber Hygiene Notices
Report generation for other compliance standards will soon follow.
In a few clicks, you get a detailed report of your cloud’s compliance posture and the specific control items we check for, giving you more time to cover other parts of your compliance requirements and address these findings.
Vulnerability Management: Bulk Editing
Many of you asked for a way to manage vulnerabilities in bulk. We definitely heard you.
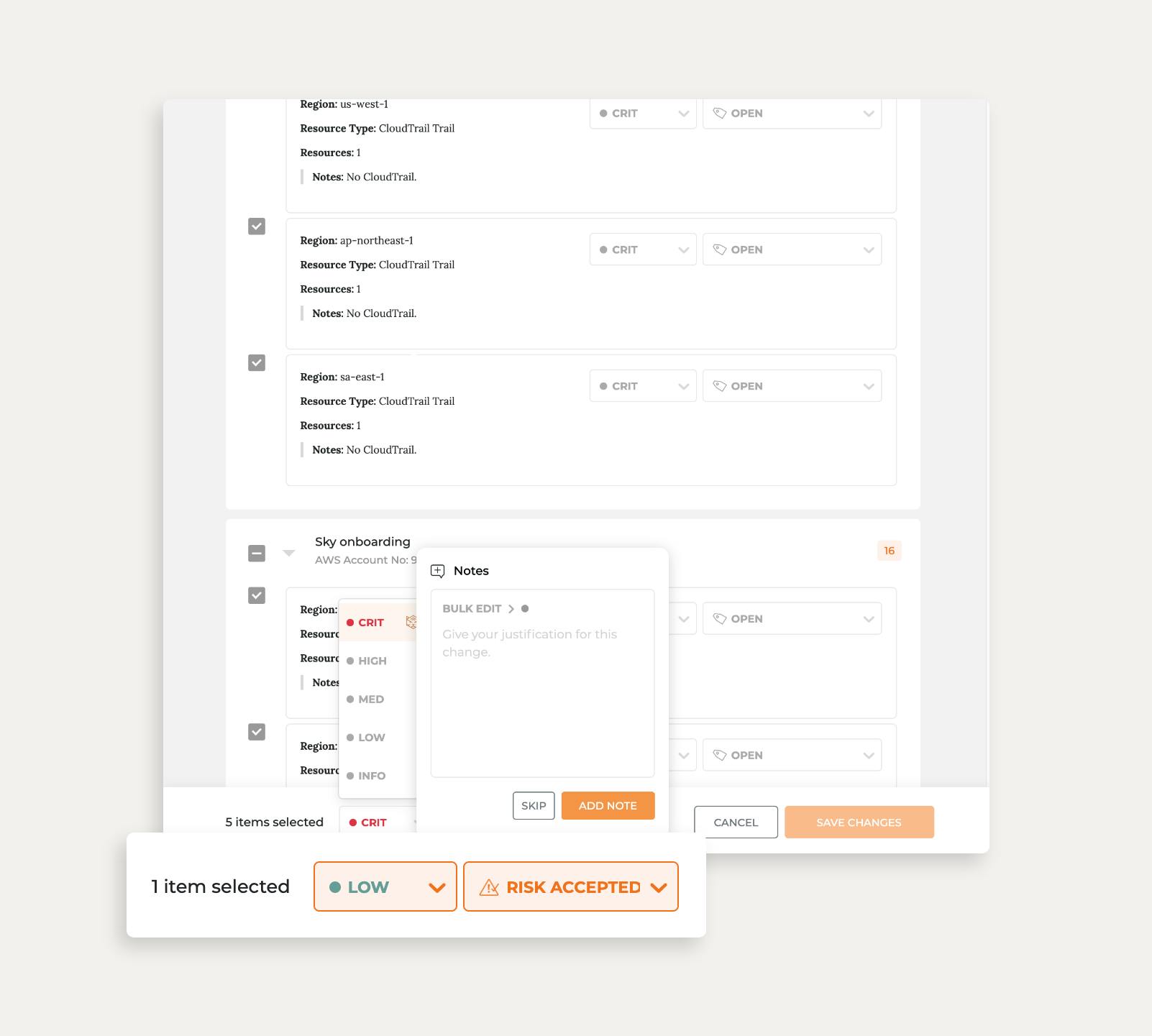
You can now edit your findings in bulk. Just tick the checkmarks next to the findings you want to manage, make your changes, and you’re done.
Export Findings to CSV
Another new feature we released is a way to export your findings to a nifty CSV file, giving you the flexibility of using those findings in whichever tool or workflow you need. Just filter out the findings you want to export and click on Export Findings.
Those are the things we worked on for the past two months. Stay tuned if you want to know more about future releases.
Want to know how compliant your organization’s cloud infrastructure is? Register for a trial here.