What is Warden Threat Detection?
Warden Threat Detection can detect threats in multiple cloud environments including Amazon Web Service (AWS), Google Cloud Platform (GCP) and Huawei Cloud. It monitors your cloud infrastructure logs 24/7 and sends out an alert immediately (near real-time) to inform you when there’s any suspicious activity happening in your environment.
Warden Threat Detection is mapped with MITRE ATT&CK tactics. It can detect most of the seen attack patterns and also comes with predictive ability, making use of User Entity Behavior Analytics (UEBA) for anomaly detection which can analyze user behavior for detecting advanced unknown threats like Insider Threats.
Like for example, as these scenarios listed below:
- Critical changes in the environment that need immediate attention;
undefinedundefinedundefined - Anomalous behavior or suspicious activities from users
undefinedundefinedundefined - Abnormal resource provisioning like Cryptocurrency mining
undefinedundefined - Data exfiltration, Privilege Escalation, Persistence, and more.
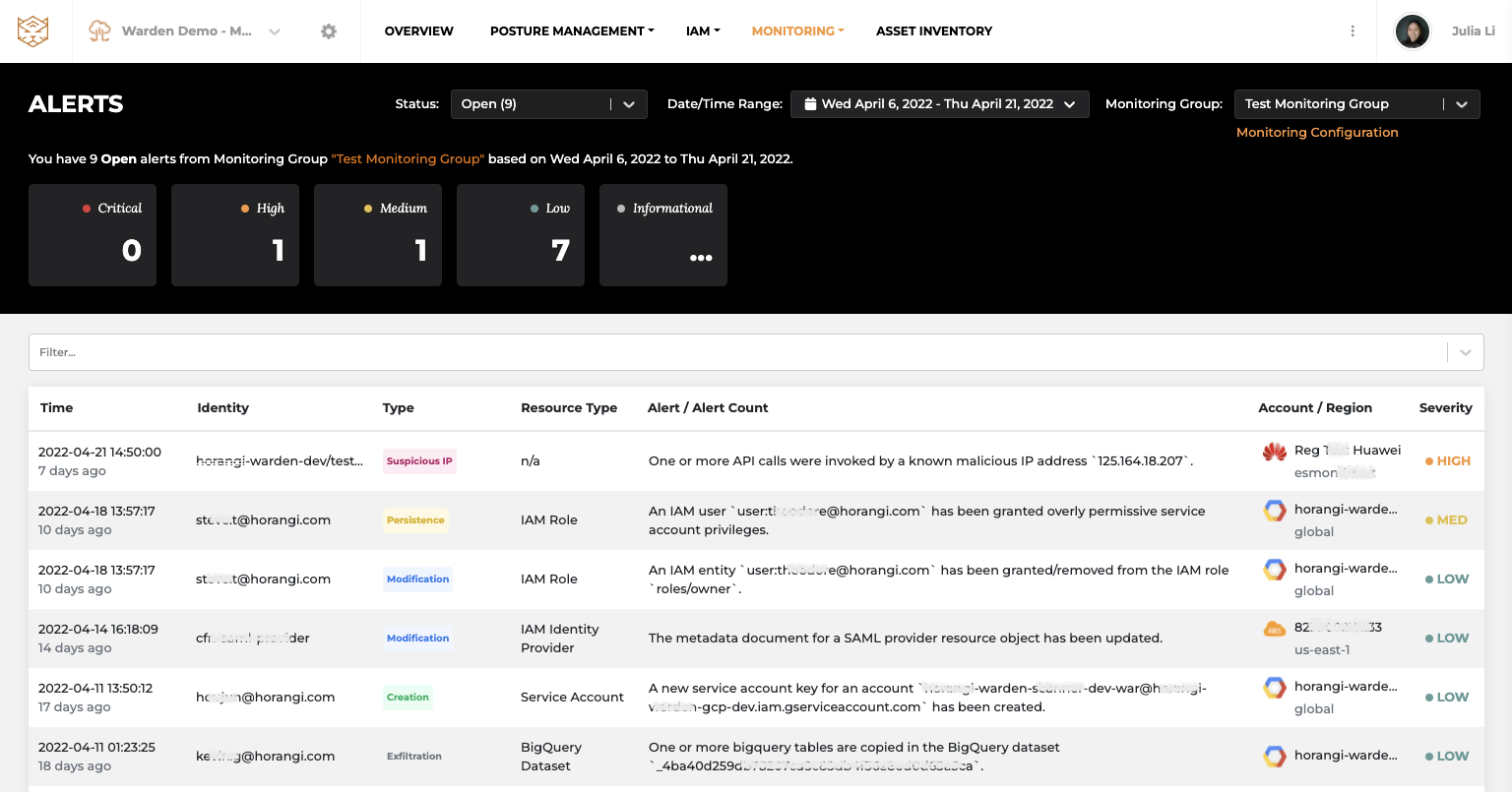
Monitoring Alerts in Threat Detection
Respond Faster with Speedy Investigation
In addition to detection, Warden also provides detailed information for the alerts so that you can quickly understand what is happening in your cloud infrastructure, what would be the impact and how to respond faster.
For example, if an unusual user activity is detected in a new geolocation, you can find anomaly summary information, such as what is the unusual location and how many times access was triggered from there. Moreover, you can investigate activities in a single click to be accessible for all baseline activities, together with flagged anomalies by this user.
If you need further investigation on IP or resources, it is available to pivot on whatever value you want to quickly identify the cause and impact of this incident. Click here to read more about the investigation.
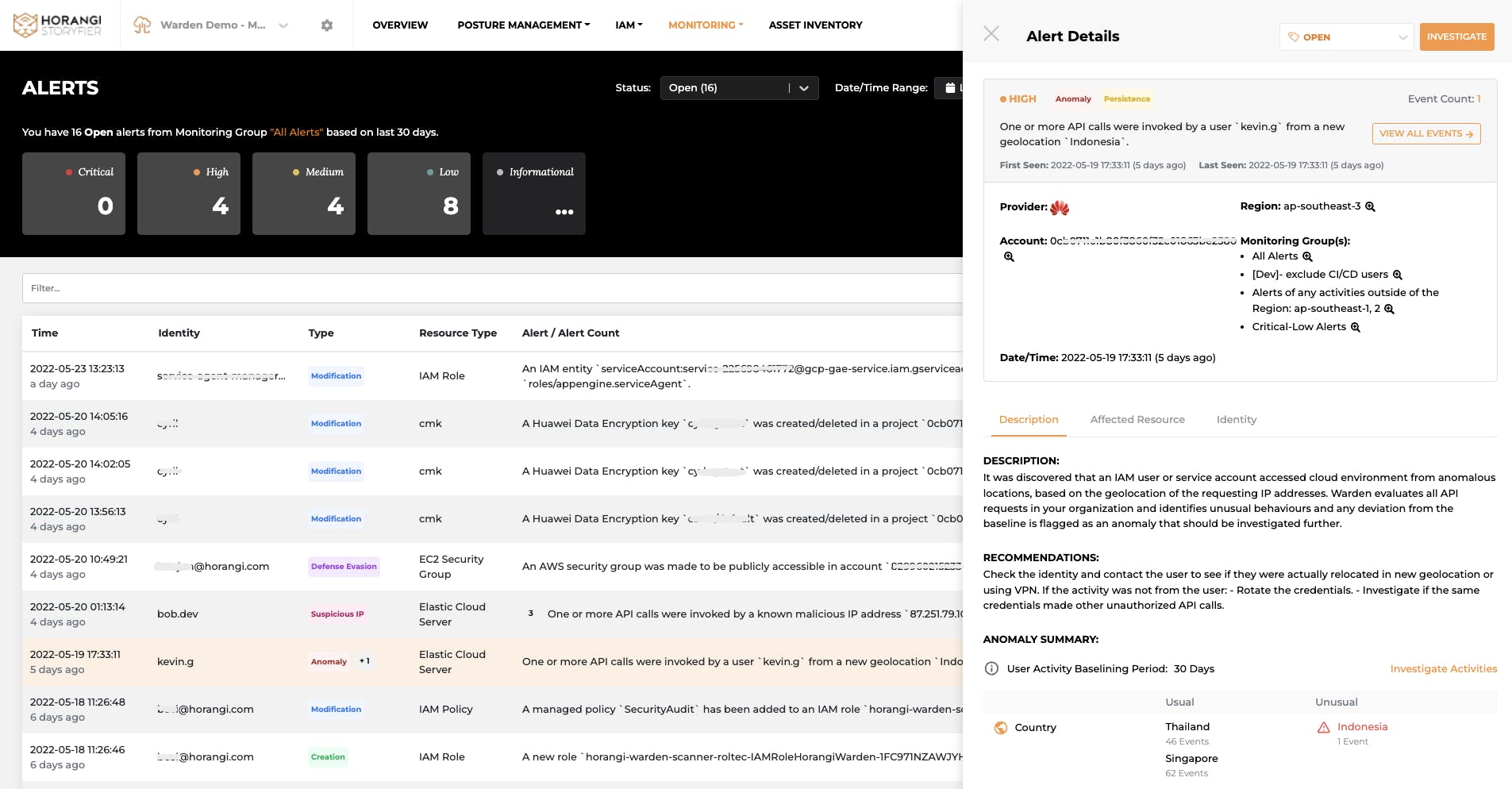
Alert Details with description, affected resources and identities
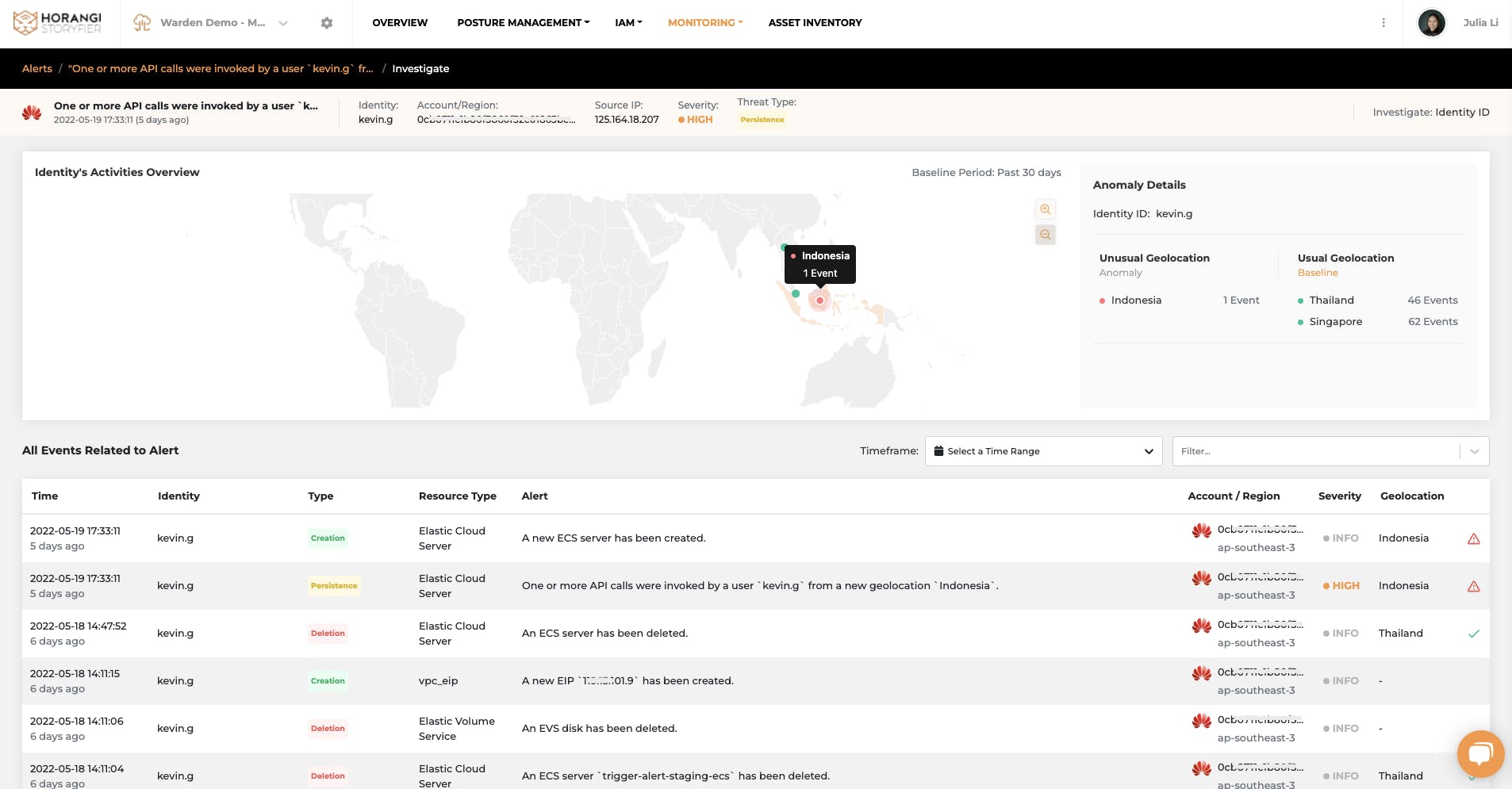
Investigation on alerts with Graphical view and all related events
Fine-tuned detection only for your organization
Unlike traditional detection tools or SIEM tools that require expertise to set up and monitor and flood you with tons of alerts, Warden is an intuitive and easy to setup tool that automatically adjusts its detection focus based on your business use case.
Consider these scenarios, these are just some of the configurations that you can easily set up in Warden and customize your alerts as you need.
- I want to closely look at my production environment rather than the dev environment
- I want to be notified if resources are provisioned outside of the defined regions
- Some of my resources matter more than others, I’d like to keep watch on them
- I don’t need to monitor every single activity from trusted IPs
- No need to flag out when CI/CD users are doing regular changes
Pro tip: Fine-grained scope configuration in the Monitoring Group meets all your special needs. For example, you can even create your own notification setting for critical alerts when suspicious exfiltration activities are detected on the bucket containing PCI data. All you need to do is flag the critical resources in your cloud environment.
(For more information on how to create a monitoring group, please check here.)
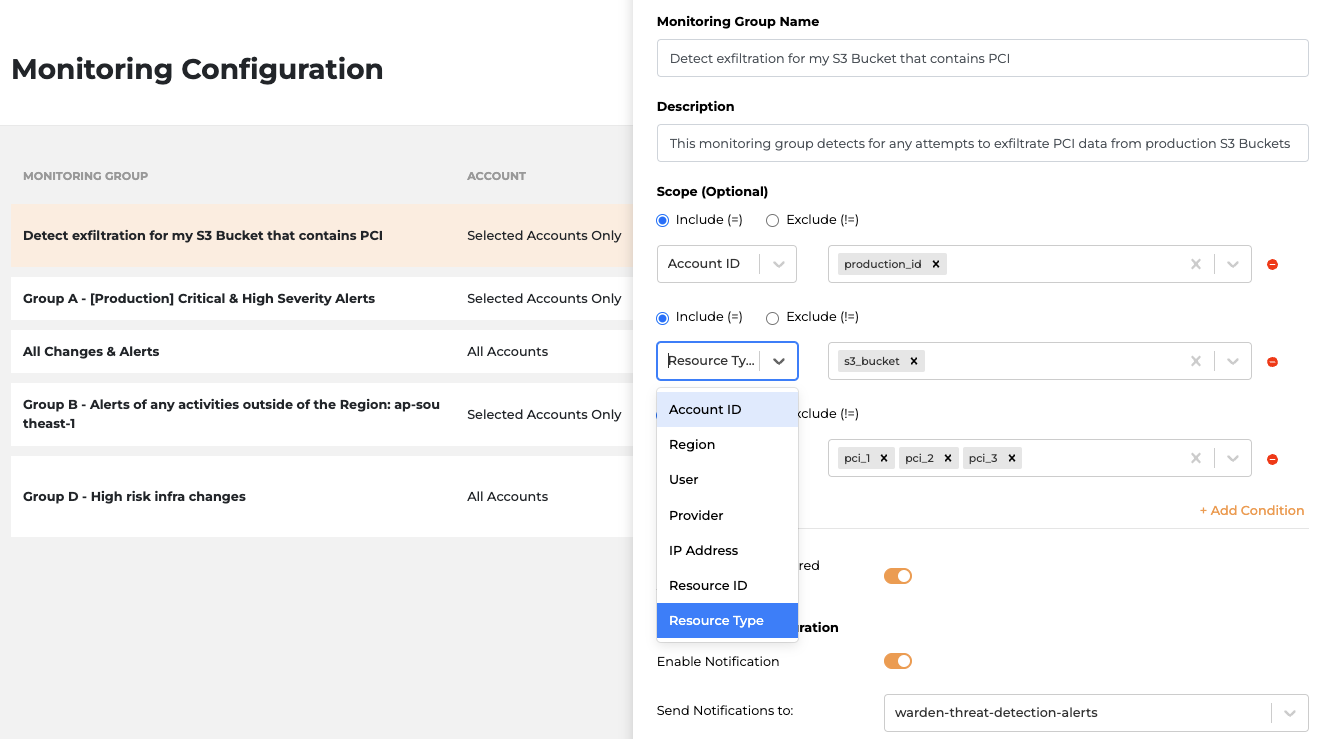
Fine-grained monitoring configuration
How can you set it up?
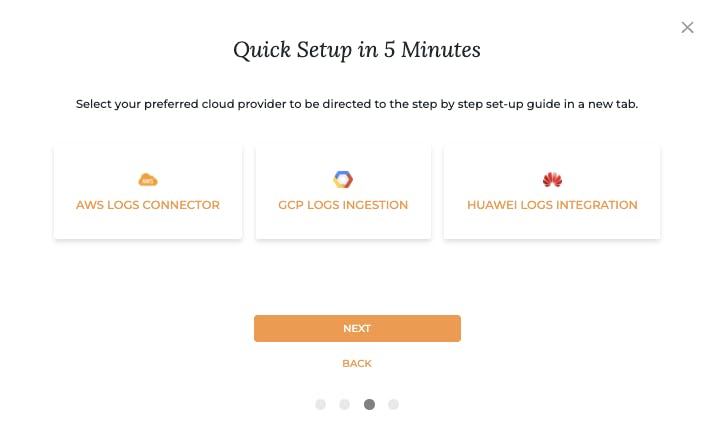
Visit Warden > Integrations and integrate your logs to Warden Threat Detection.
Conclusion
Cyber attacks will never stop and as cloud adoption grows, attackers are using more and more complex techniques to get into your cloud infrastructure and target your critical assets. Hence, real-time detection tools like Warden Threat Detection are necessary for protecting your crown jewels from any threat. Warden empowers your business with all the protection and 24/7 monitoring you need. Drop us a line here to set up a customized 15 mins discovery call.