What is Warden Threat Detection?
Warden Threat Detection can detect threats in multiple cloud environments including Amazon Web Service (AWS), Google Cloud Platform (GCP), Huawei Cloud, and Alibaba Cloud. It monitors your cloud infrastructure logs 24/7 and sends out an alert immediately to inform you when there’s any suspicious activity happening in your environment.
Warden Threat Detection is mapped with MITRE ATT&CK tactics. It can detect most of the seen attack patterns and also comes with predictive ability, making use of User Entity Behavior Analytics (UEBA) for anomaly detection which can analyze user behavior for detecting advanced unknown threats like Insider Threats. Currently, Warden is the only threat detection tool that is available for Alibaba Cloud.
Strengthen your Security Governance with Real-time Monitoring
On top of your prevention measures in your cloud environment, real-time threat detection is key to keeping away from advanced threat actors. Threats evolve over time, making old responses redundant, along with the dynamic cloud environment.
Warden monitors logs that record all the activities happening in your cloud environment, especially all the API calls, and identifies suspicious behaviors based on the MITRE ATT&CK framework. We can detect numerous types of threats in the cloud, throughout various phases of an adversary's attack lifecycle. For example, persistence or Privilege Escalation behavior, where attackers try to stay within your environment after gaining initial access, or defense evasion, where the attacker turned off logging or changes the security configuration, read more here.
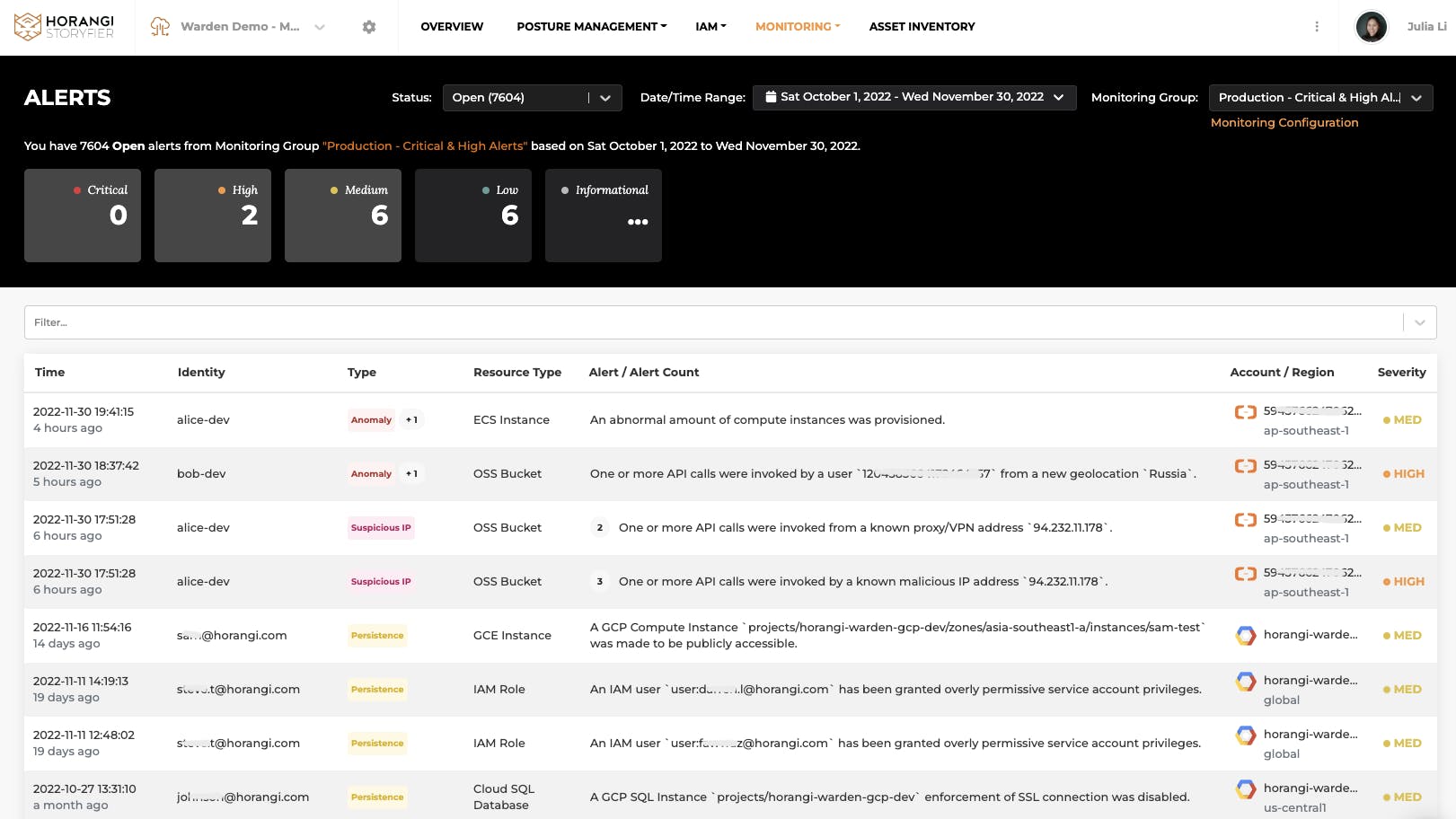
Monitoring Alerts in Threat Detection
Besides, all the activities are enriched with Threat Intelligence sources that can flag out connections from malicious IPs or Tor IPs. It shows suspicious IP alerts with geolocation data, affected resources and identities, and further information is available with the resource access graph.
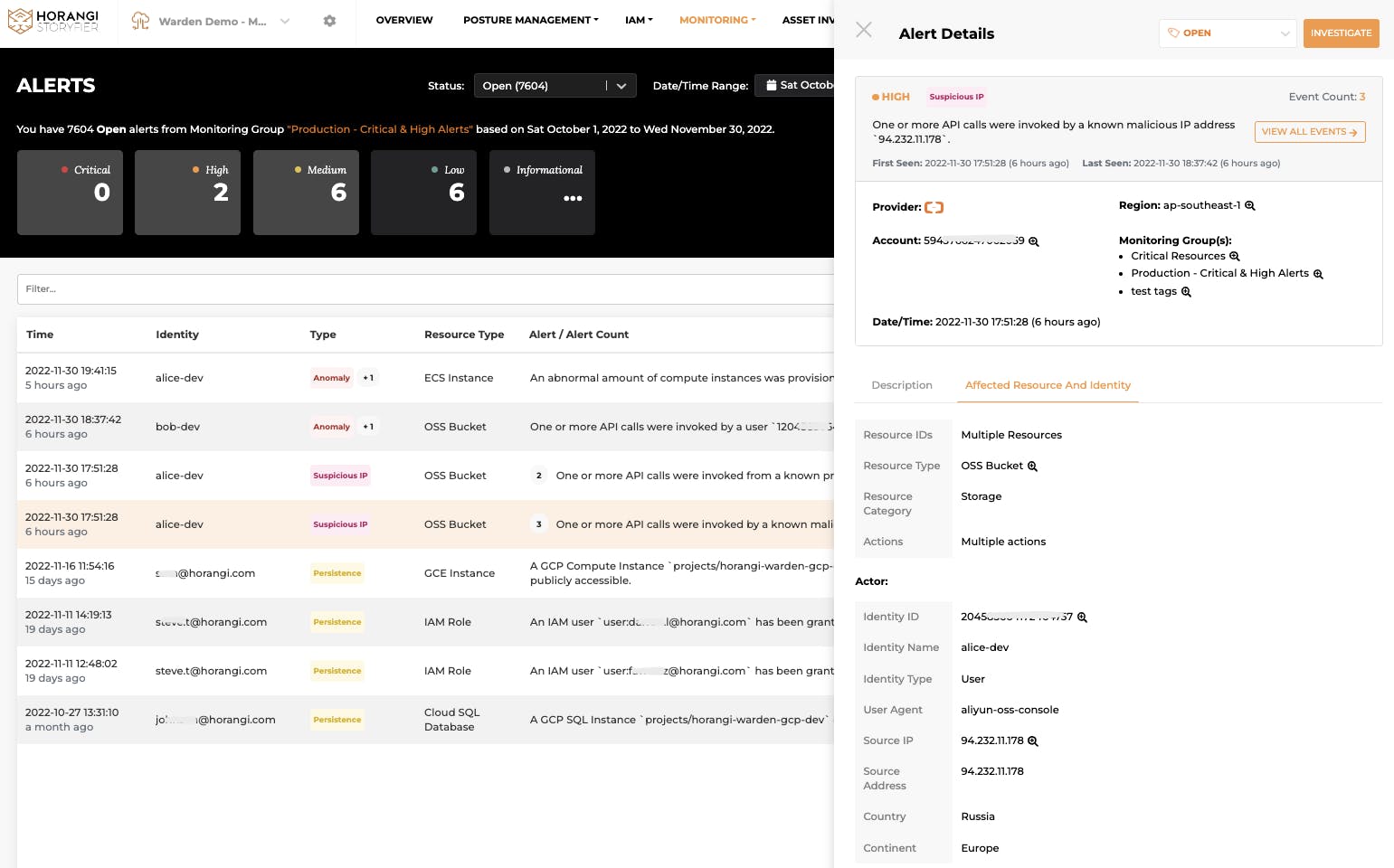
Affected Resource and Identity details in Suspicious IP Alerts
Anomaly Detection with User Entity Behavior Analytics (UEBA)
The important thing to note is that Warden is able to detect anomalies with User Entity Behavior Analytics. The key thing in UEBA is that it identifies anomalous activities by looking at contextual information and flags out whenever there’s an anomaly deviating from the baseline. It could be an early indication of credential compromise, cryptocurrency mining, or even insider threats.
For example, a user suddenly accessed your cloud resources from a new geolocation - something that is very likely to happen in case of a real cyberattack. The attackers can access your data from the unusual geolocation using the compromised credential.
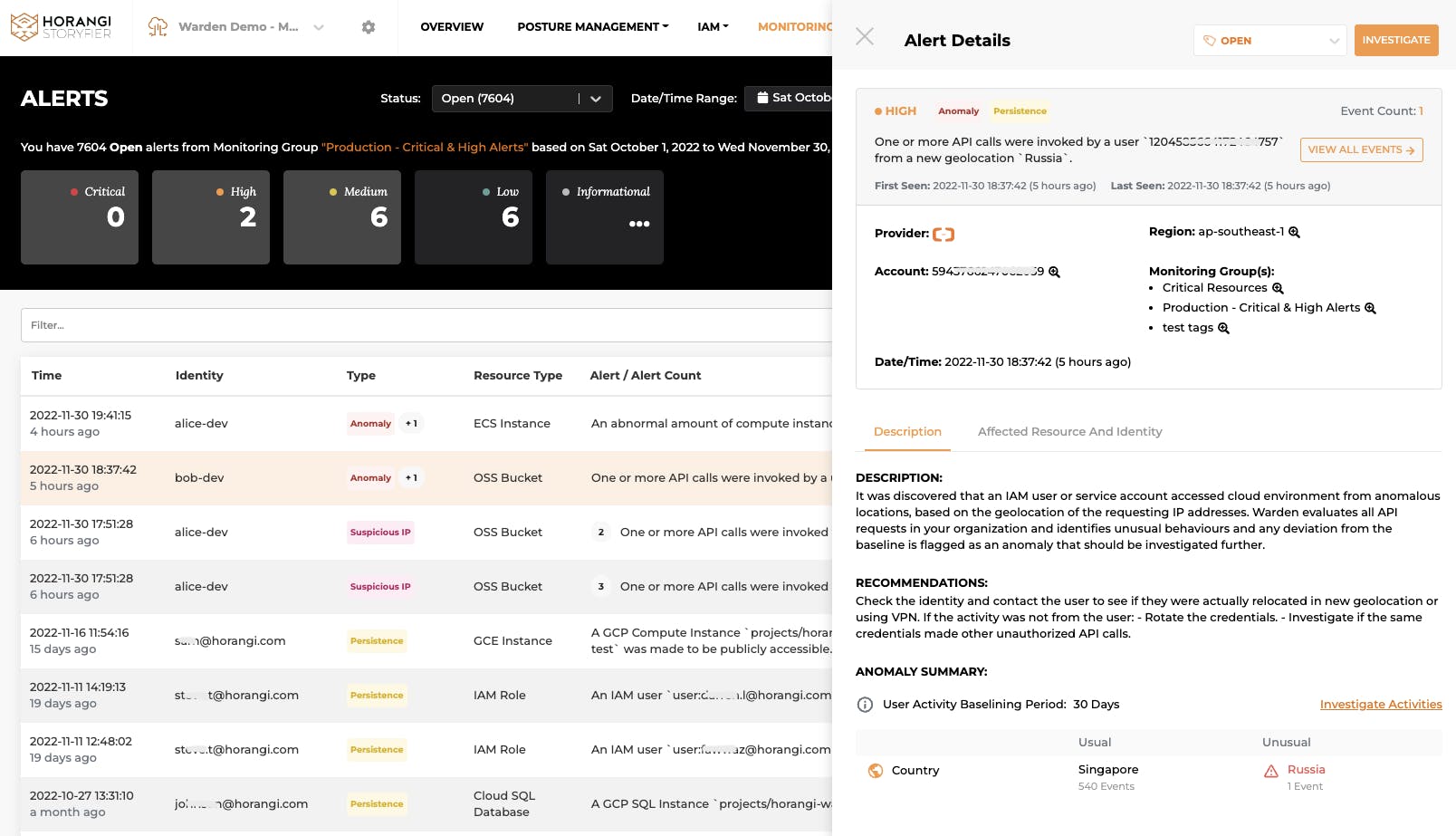
Anomaly Alerts with Descriptions
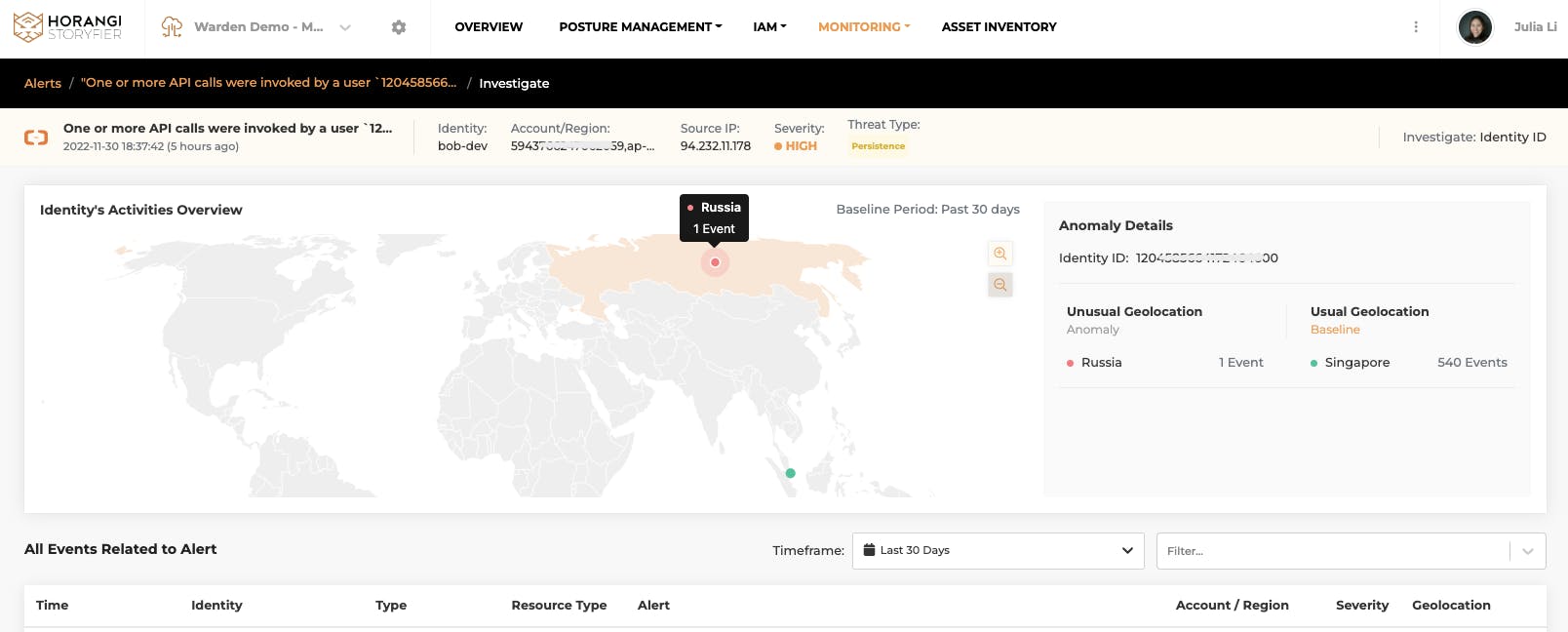
Anomaly Investigation Graph
Another example is a resource-based anomaly, like cryptocurrency mining. The moment an attacker tries to spin up an unusually high number of instances or launch them in rarely used regions, you will immediately get alerted.
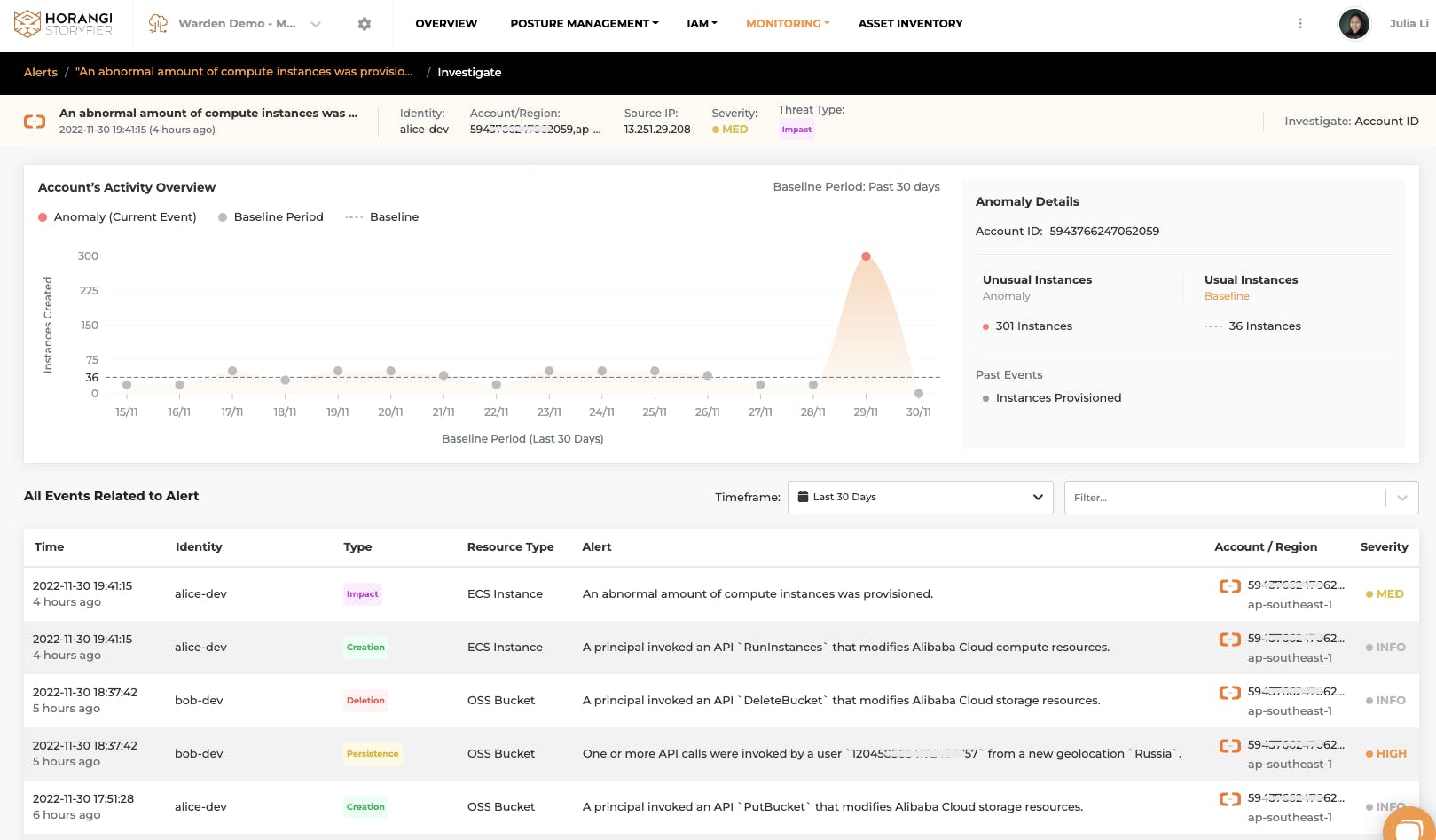
Abnormal Resource Provision
How can you set it up?
With Warden’s Threat Intelligence, you can instantly identify and zoom in on a suspected asset and understand the full context from both a configuration and activity perspective with associated event severity, thereby reducing your meantime (and money) to detecting, investigating, and remediating threats. Visit Warden > Integrations and integrate your logs to Warden Threat Detection. Read more here.
Conclusion
Threat actors in the cloud typically leverage the cloud management plane and not just the network layer. If you only have traditional security tools that are not equipped to detect threats in the management plane, you are already one step behind these advanced threat actors. Get Threat Detection on your fingertips with Horangi Warden and predict and remediate potential vulnerability issues before they occur. Drop us a line here to set up a customized 15 mins discovery call.




