Identify Critical Resources
Previously, we introduced Asset Inventory to manage your assets in your cloud infrastructure which can help you with compliance standards including asset management and other security reviews like access reviews. Our goal is to incorporate a centralized asset management functionality that provides a single pane of glass to review all the vulnerabilities and security alerts associated with your cloud assets. And here’s how we plan to do so to make 24/7 monitoring more achievable for your organization.
Why Do You Need Criticality Flagging?
For critical assets, such as resources that run important applications in your production environment or store the most sensitive data need diligent protection. With this feature, Warden Threat Detection can help you prioritize these over other assets. You can highlight them as Critical Assets in the asset inventory. This can further help you quickly identify and prioritize security risks of misconfigurations or excessive permissions on your critical assets. For more information about asset inventory management related to Identity and Access Management, you can read more here.
Value for Our Customers
With this latest release, you can now use the resource criticality flagging feature in Warden Threat Detection. It can automatically identify critical assets that you flagged in the asset inventory. It helps you gain immediate value, as you can fine-tune threat monitoring to prioritize only the threats related to critical assets, significantly improving the efficiency of 24/7 security monitoring.
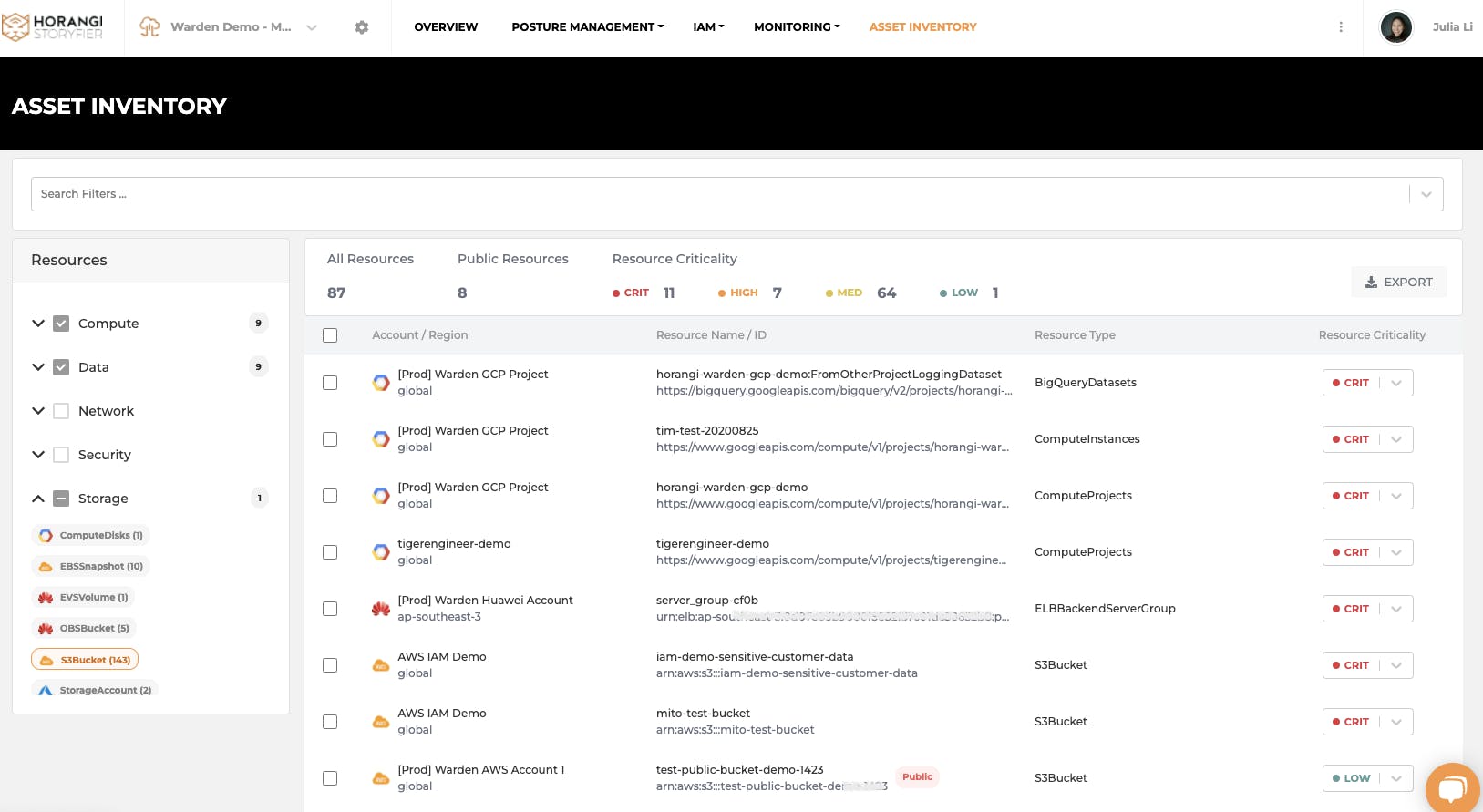
Asset Inventory: Define Resource Criticality
Getting Started: Closely Monitor Your Critical Resources
After you flag critical resources in the asset inventory, you can closely monitor these critical resources with Threat Detection. Warden Threat Detection monitors your cloud infrastructure logs 24/7 and sends out an alert immediately when there’s any suspicious activity happening in your environment.
For critical resources like the bucket where your most sensitive customer data is stored, you may not want to apply the same level of security monitoring as other bucket changes. Instead, you may want to monitor every single activity and get notified whenever changes happen to your critical assets. Having these fine-grained configurations in the monitoring scope enables you to have a differentiated security level on critical resources and apply higher severity warnings on suspicious behaviors on all these resources. For example, you might want to get notified whenever there’s any change on an AWS S3 bucket containing PII data. In Warden Threat Detection, you can create a monitoring group that specifies resource criticality as ‘critical’ which can then automatically apply the same level of high scrutiny for all other flagged ‘critical’ assets in your organization. It enables you to focus more on alerts that truly matter to your organization and snooze false positives. This feature comes highly requested from most of our customers, as it allows them to overcome alert fatigue.
But that’s not all. You can further drill down the noise in Warden Threat Detection, as we have been working hard to make your alerts more customized and efficient to reduce your investigation time and effort. For example, you can also group the monitoring scope by using filters like production vs. development environment, regions, resource types, etc. For more information on how to configure the monitoring group, please check it out here.
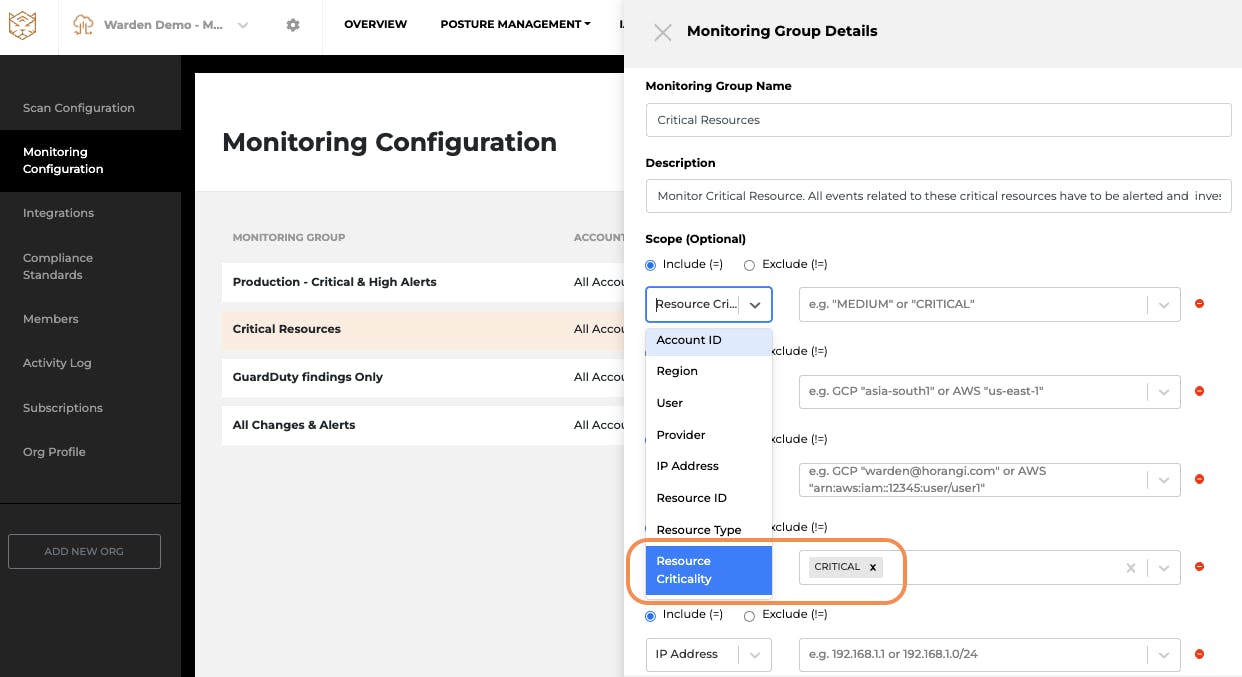
Setting up Monitoring Group for Critical Resources
Investigation Made Easier
In addition to monitoring and detecting suspicious behavior on critical resources, Warden Threat Detection also provides 100% visibility on all activities related to critical resources for investigation. One way to check critical threats on critical resources is by using Asset Inventory, where you can determine all the misconfigurations and IAM Security Risks that are associated with those assets in question. Another way to investigate efficiently is by directly looking through Monitoring Alerts. This can enable you to see potential threats for all resources and quickly identify whether the threats are related to your critical assets at a glance.
By doing ‘asset reviews’ with Warden, you can see the full history of all the changes to critical resources and who has made these changes to them. You can also see the ‘critical flag’ on each resource, that you would have earlier identified as ‘critical assets' in the Asset Inventory across all cloud accounts. Hence giving you 100% visibility for all of your critical assets, making investigation efficient.
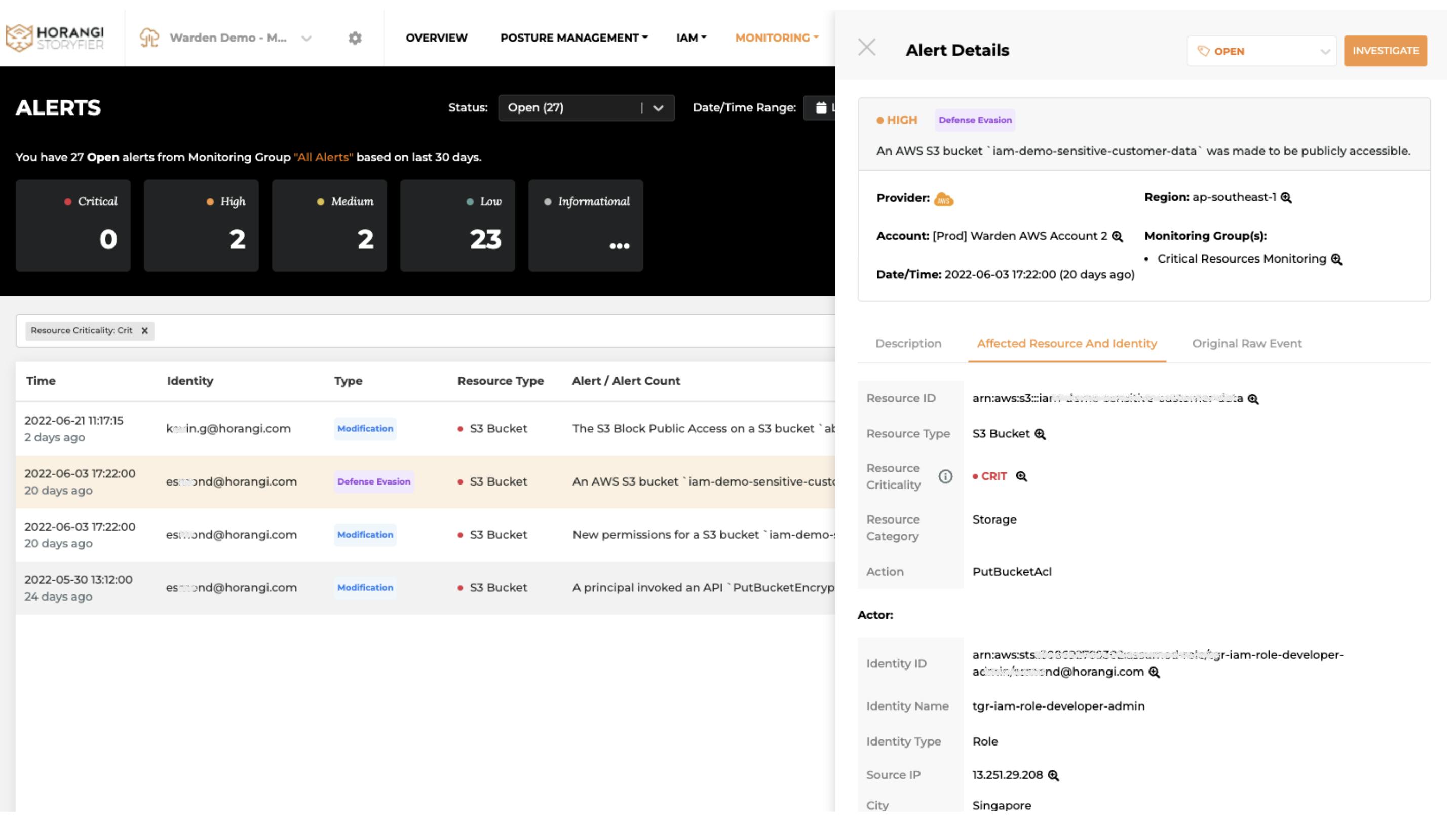
Investigate Alerts related to Critical Resources
Conclusion
Many compliance standards require continuous monitoring of your critical infrastructure. Although monitoring tools can report all possible threats for you, with a small team and growing security burdens on the organization, we need a smarter way to prioritize and monitor the security risks on your critical assets. Hence, an all-in-one security tool like Warden is necessary for protecting your crown jewels from any threat. Drop us a line here to set up a customized 15 mins discovery call.