Horangi Webinar Series 2020
We introduced live webinars in 2020 to stay connected with everyone while life was completely uprooted from what it used to look like. Thankful to have been given the privilege of carrying on with life at home, we hope it has also been a fruitful time for everyone who have spoken and interacted with us as we discussed through the different topics virtually. If you've missed any of our live sessions, here's your chance to relive them.
Get full access by filling out the form at the bottom of the page.
Explore The Topics Discussed
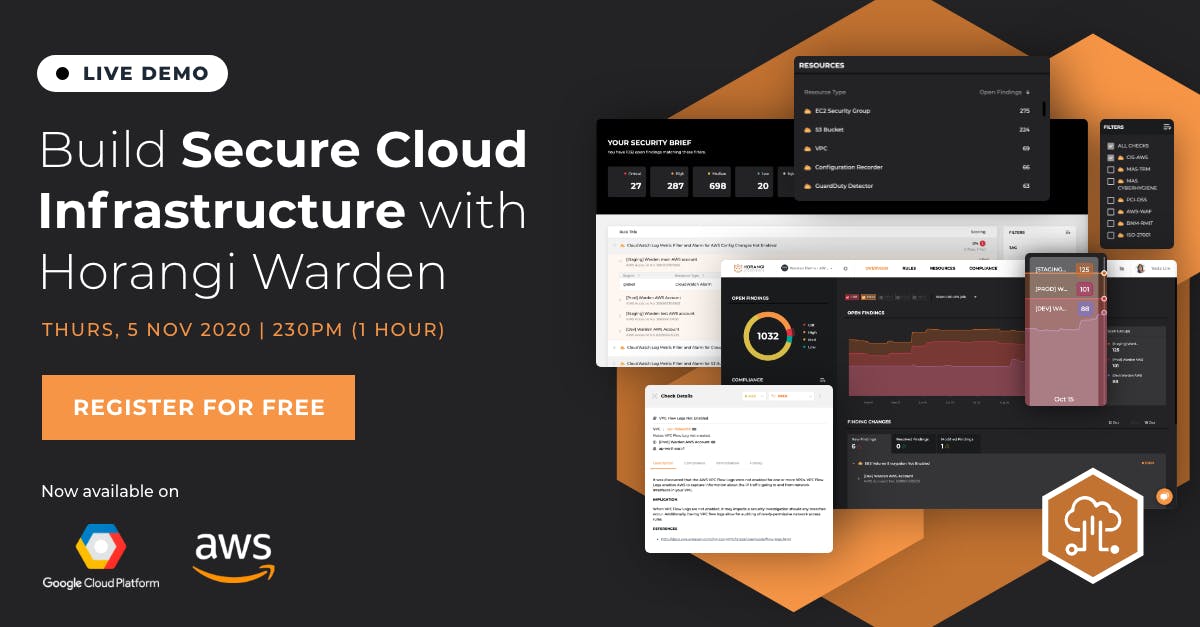
Build Secure Cloud Infrastructure With Horangi Warden
Learn how to optimize security and compliance in the cloud using Warden to help you with:
- Detecting cloud security threats and automatically fixing them
- Automating secure cloud configurations for Amazon Web Services (AWS) and Google Cloud Platform (GCP) as you scale your infrastructure
- Generating one-click, audit-ready compliance reports for 11 compliance standards including ISO 27001 and CIS

Build Secure Cloud Infrastructure With Horangi Warden
Learn how to optimize security and compliance in the cloud using Warden to help you with:
- Detecting cloud security threats and automatically fixing them
- Automating secure cloud configurations for Amazon Web Services (AWS) and Google Cloud Platform (GCP) as you scale your infrastructure
- Generating one-click, audit-ready compliance reports for 11 compliance standards including ISO 27001 and CIS

Tackling the Biggest Blind Spots in Public Cloud Security
When tracing the causes of cloud breaches, businesses were shocked to find that the majority of the breaches could be attributed back to a simple cloud misconfiguration. Why did such incidents continue to happen, even with some of the most digitally-advanced organizations? Could such cloud security incidents be easily prevented? In this webinar, expect to:
- Learn the most critical cloud security blind spots
- Gain insights into tackling cloud misconfigurations
- Cloud security questions answered in a Q&A session

Tackling the Biggest Blind Spots in Public Cloud Security
When tracing the causes of cloud breaches, businesses were shocked to find that the majority of the breaches could be attributed back to a simple cloud misconfiguration. Why did such incidents continue to happen, even with some of the most digitally-advanced organizations? Could such cloud security incidents be easily prevented? In this webinar, expect to:
- Learn the most critical cloud security blind spots
- Gain insights into tackling cloud misconfigurations
- Cloud security questions answered in a Q&A session

Demystifying Your AWS Cloud Security For Faster Innovation
Join Horangi CEO & Co-founder Paul Hadjy and Director of Cloud Security Engineering Steve Teo as they talk about how Horangi’s customers apply our unique security methodology to innovate faster in their AWS environments.

Demystifying Your AWS Cloud Security For Faster Innovation
Join Horangi CEO & Co-founder Paul Hadjy and Director of Cloud Security Engineering Steve Teo as they talk about how Horangi’s customers apply our unique security methodology to innovate faster in their AWS environments.

An Introduction to the MITRE ATT&CK Matrix
Learn how to optimize security and compliance in the cloud using Warden to help you with:
- Detecting cloud security threats and automatically fixing them
- Automating secure cloud configurations for Amazon Web Services (AWS) and Google Cloud Platform (GCP) as you scale your infrastructure
- Generating one-click, audit-ready compliance reports for 11 compliance standards including ISO 27001 and CIS

An Introduction to the MITRE ATT&CK Matrix
Learn how to optimize security and compliance in the cloud using Warden to help you with:
- Detecting cloud security threats and automatically fixing them
- Automating secure cloud configurations for Amazon Web Services (AWS) and Google Cloud Platform (GCP) as you scale your infrastructure
- Generating one-click, audit-ready compliance reports for 11 compliance standards including ISO 27001 and CIS

The Science Behind Peacetime Cybersecurity Operations
Today, is there a distinction between peacetime and wartime? If so, who are we at war with? Like how a car is regularly serviced, cybersecurity requires that same level of proactive attention so your organization does not need to worry about painful cleanup costs. Services that you can leverage include Penetration Testing, Phishing, Red Teaming, and Cybersecurity Assessment. Takeaway from the chat on topics like:
- The benefits of hacking your own organizations
- Steps that businesses can take now to improve their security posture
- This philosophy practiced by our customer tiket.com, a leading Indonesian travel agent

The Science Behind Peacetime Cybersecurity Operations
Today, is there a distinction between peacetime and wartime? If so, who are we at war with? Like how a car is regularly serviced, cybersecurity requires that same level of proactive attention so your organization does not need to worry about painful cleanup costs. Services that you can leverage include Penetration Testing, Phishing, Red Teaming, and Cybersecurity Assessment. Takeaway from the chat on topics like:
- The benefits of hacking your own organizations
- Steps that businesses can take now to improve their security posture
- This philosophy practiced by our customer tiket.com, a leading Indonesian travel agent

Work-From-Home Cybersecurity Explained: Best Practices For Telecommuting
How can hackers exploit work-from-home vulnerabilities? What impact do the new Work-From-Home arrangements have on vulnerability to cyber threats on an organizational and individual level? Learn how to protect yourself and your company's critical assets.
Top 3 WFH Cybersecurity Risks discussed:
- Vulnerable Human Behaviour
- Unsecured Personal Technologies
- Unsecured Personal Practices

Work-From-Home Cybersecurity Explained: Best Practices For Telecommuting
How can hackers exploit work-from-home vulnerabilities? What impact do the new Work-From-Home arrangements have on vulnerability to cyber threats on an organizational and individual level? Learn how to protect yourself and your company's critical assets.
Top 3 WFH Cybersecurity Risks discussed:
- Vulnerable Human Behaviour
- Unsecured Personal Technologies
- Unsecured Personal Practices

The Enemy Within: Navigating A CISO's Biggest Challenges
Consider the world a CISO lives in — unappreciated without a security incident, vilified at the slightest hint of one; the CISO is labeled a cost driver and afforded a measly budget for the job. It is a harsh world and a phenomenon that pervades organizations large and small.
Hear from former Mandiant VP Steve Surdu and Horangi Director Mark Fuentes as they share key strategies to help CISOs navigate their top challenges:
- Understand your organization’s new focus areas to improve your security capabilities in 2021
- Learn how to calculate and prove security ROI, establishing metrics and limitations to make leadership understand the true value of your team
- Get your priorities right with education, people, and process effectiveness

The Enemy Within: Navigating A CISO's Biggest Challenges
Consider the world a CISO lives in — unappreciated without a security incident, vilified at the slightest hint of one; the CISO is labeled a cost driver and afforded a measly budget for the job. It is a harsh world and a phenomenon that pervades organizations large and small.
Hear from former Mandiant VP Steve Surdu and Horangi Director Mark Fuentes as they share key strategies to help CISOs navigate their top challenges:
- Understand your organization’s new focus areas to improve your security capabilities in 2021
- Learn how to calculate and prove security ROI, establishing metrics and limitations to make leadership understand the true value of your team
- Get your priorities right with education, people, and process effectiveness

Playing To Win: The Cybersecurity Strategy Used By Top Businesses
What makes a cybersecurity strategy more than just strategy? Even with security teams hamstrung by a limited budget in 2020, how do the CISOs from leading organizations in Asia consistently drive results for their businesses?
Security leaders from Circles.Life, WeLab Bank, and SPTel in an online fireside chat to share their insights on:
- Keeping up with new cyber threats
- The recipe for creating high-performing security teams
- Priorities for 2020 and beyond

Playing To Win: The Cybersecurity Strategy Used By Top Businesses
What makes a cybersecurity strategy more than just strategy? Even with security teams hamstrung by a limited budget in 2020, how do the CISOs from leading organizations in Asia consistently drive results for their businesses?
Security leaders from Circles.Life, WeLab Bank, and SPTel in an online fireside chat to share their insights on:
- Keeping up with new cyber threats
- The recipe for creating high-performing security teams
- Priorities for 2020 and beyond

Security and Privacy Compliance: Better Together
Horangi Deputy Director of Cyber Operations Mark Fuentes talks about how Horangi’s customers all over Asia use our tailored cybersecurity solutions to achieve their Data Privacy compliance goals.

Security and Privacy Compliance: Better Together
Horangi Deputy Director of Cyber Operations Mark Fuentes talks about how Horangi’s customers all over Asia use our tailored cybersecurity solutions to achieve their Data Privacy compliance goals.

[BAHASA] Know Your Enemy: Phishing From A Hacker's Perspective
Dalam webinar kali ini, Cyber Operations Consultant dari Horangi, Natasha dan Ardiansyah, akan membahas dan mendemonstrasikan cara kerja serangan Phishing Email, serta tips untuk mencegah dan mendeteksi serangan tersebut secara efektif.
Jangan lewatkan penawaran layanan Simulasi Serangan Phishing dengan harga spesial akhir tahun untuk perusahaan Anda!

[BAHASA] Know Your Enemy: Phishing From A Hacker's Perspective
Dalam webinar kali ini, Cyber Operations Consultant dari Horangi, Natasha dan Ardiansyah, akan membahas dan mendemonstrasikan cara kerja serangan Phishing Email, serta tips untuk mencegah dan mendeteksi serangan tersebut secara efektif.
Jangan lewatkan penawaran layanan Simulasi Serangan Phishing dengan harga spesial akhir tahun untuk perusahaan Anda!
[BAHASA] Web App Security: What Your WAF Can & Can’t Do
Apakah WAF saja cukup untuk melindungi aplikasi web anda dari serangan siber?
Dalam webinar ini, Cyber Operations Consultant dari Horangi, Annisa dan Azam, akan membahas mengenai taktik dan teknik eksploitasi salah satu kerentanan keamanan yang seringkali ditemukan pada aplikasi web dengan proteksi WAF (Web Application Firewall) serta keunggulan dari penerapan keamanan siber yang menyeluruh.

[BAHASA] Web App Security: What Your WAF Can & Can’t Do
Apakah WAF saja cukup untuk melindungi aplikasi web anda dari serangan siber?
Dalam webinar ini, Cyber Operations Consultant dari Horangi, Annisa dan Azam, akan membahas mengenai taktik dan teknik eksploitasi salah satu kerentanan keamanan yang seringkali ditemukan pada aplikasi web dengan proteksi WAF (Web Application Firewall) serta keunggulan dari penerapan keamanan siber yang menyeluruh.
Upcoming Webinar
Upcoming Webinar

Taking it in Stride - The Role of Cloud Compliance in Digital Transformation
Taking it in Stride - The Role of Cloud Compliance in Digital Transformation
Your organization's adoption of cloud-native technologies put its infrastructure at risk of non-compliance but cloud compliance doesn’t need to be an obstacle to digital transformation. Find out how in this live webinar on 10 March.

