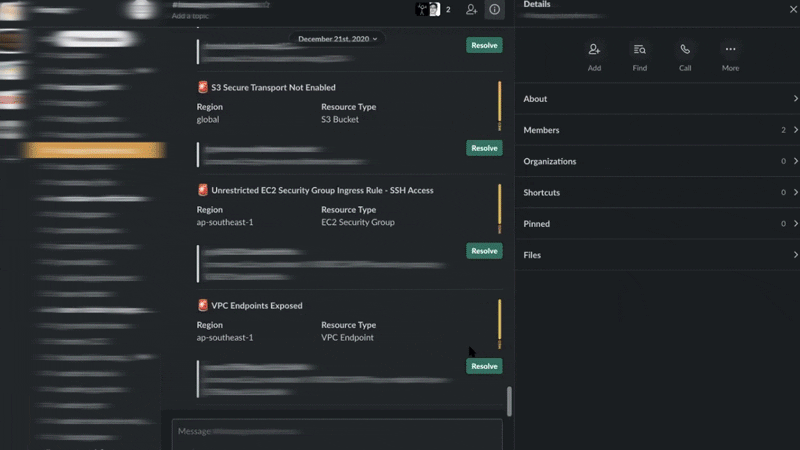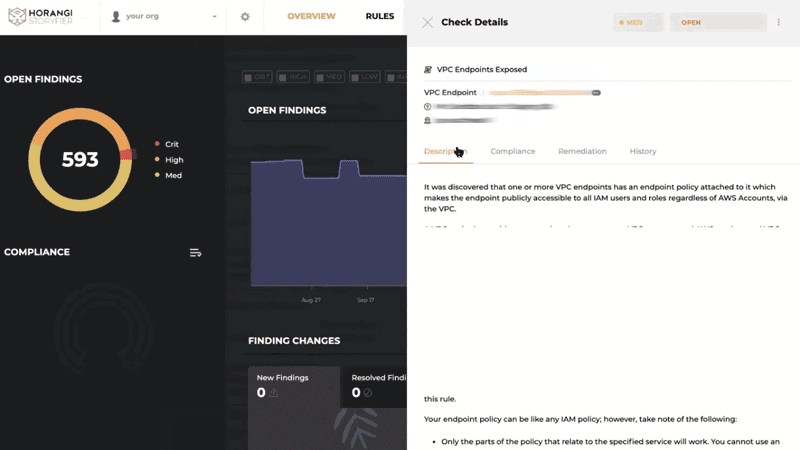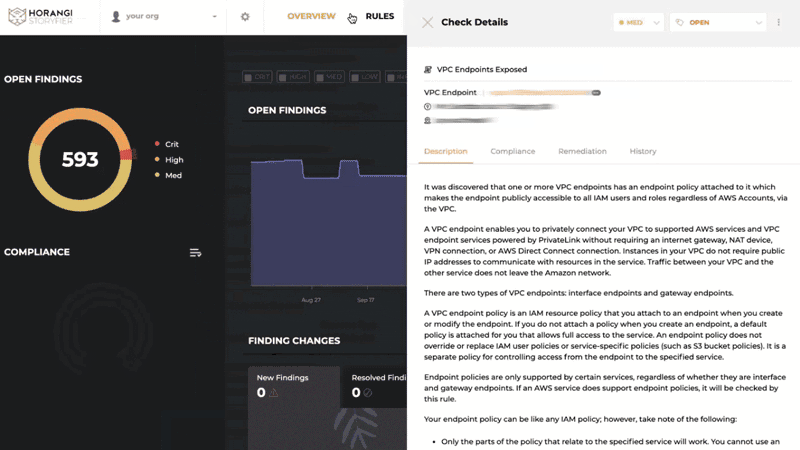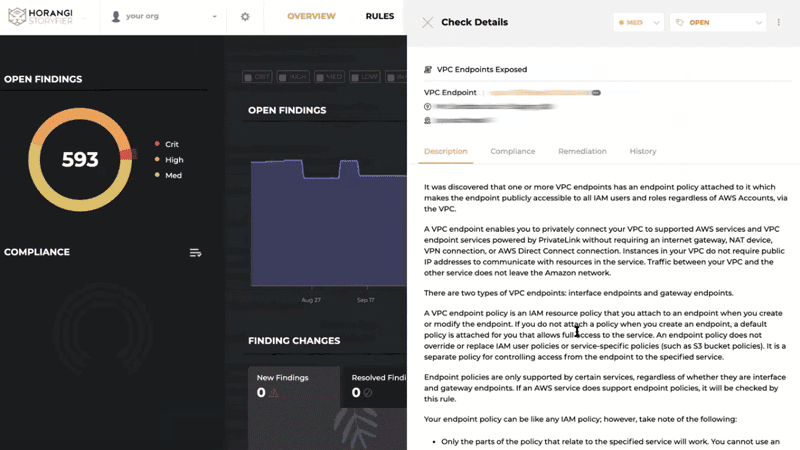
Only the security alerts you need, delivered the way you want
How do you keep track of the thousands of cloud resources used and whether you face security threats worth worrying about? Warden's rule set identifies whenever you contravene security best practices, alerting you when they happen so that you can prioritize these fixes accordingly.
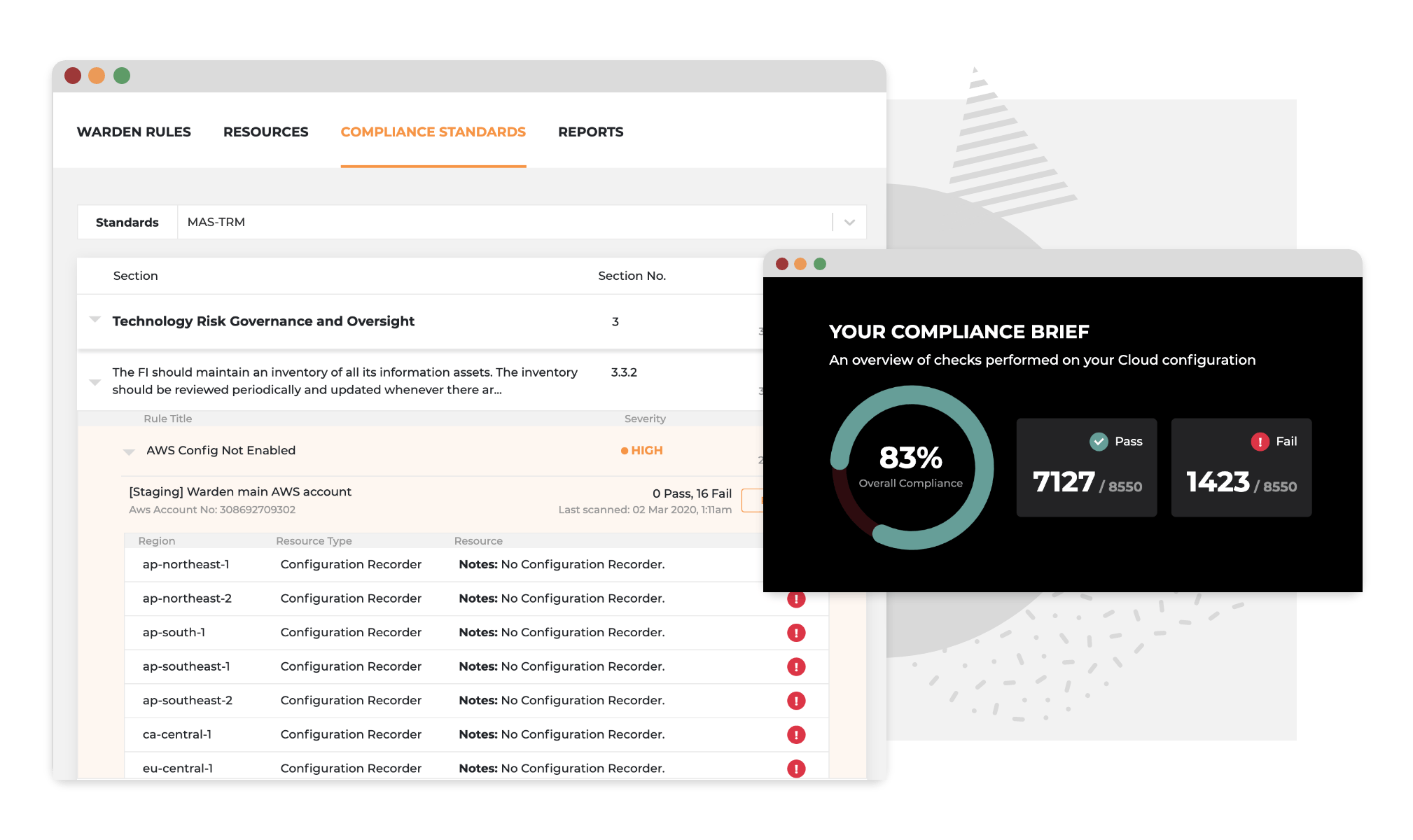
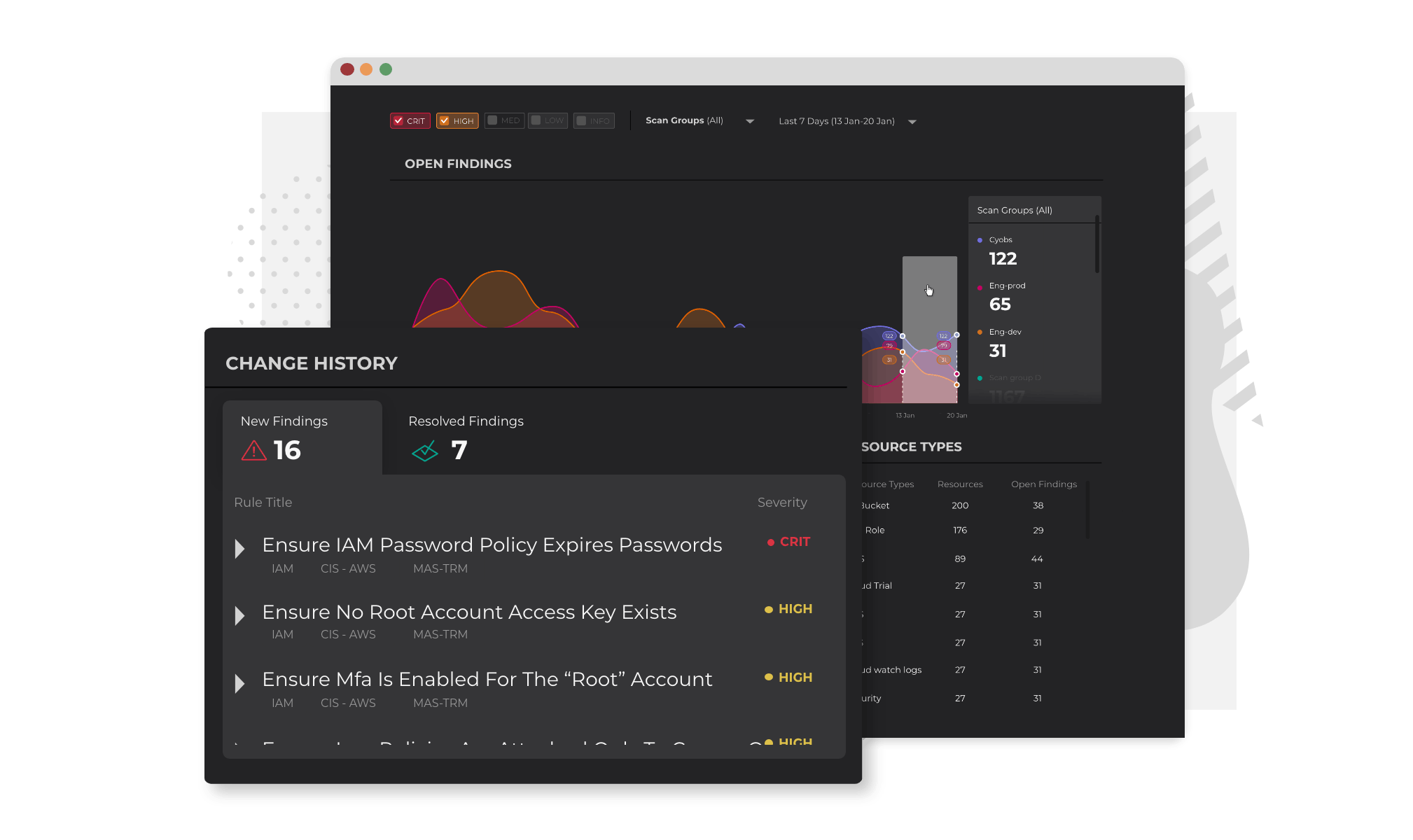
Automate compliance to always be audit-ready
Control level mapping against popular frameworks such as GDPR, MAS TRM, and ISO 27001 empowers your organization to reduce the time spent on reading compliance documents and creating reports. With Warden's Compliance dashboard, all of the necessary information and function are readily available for you and your auditors.
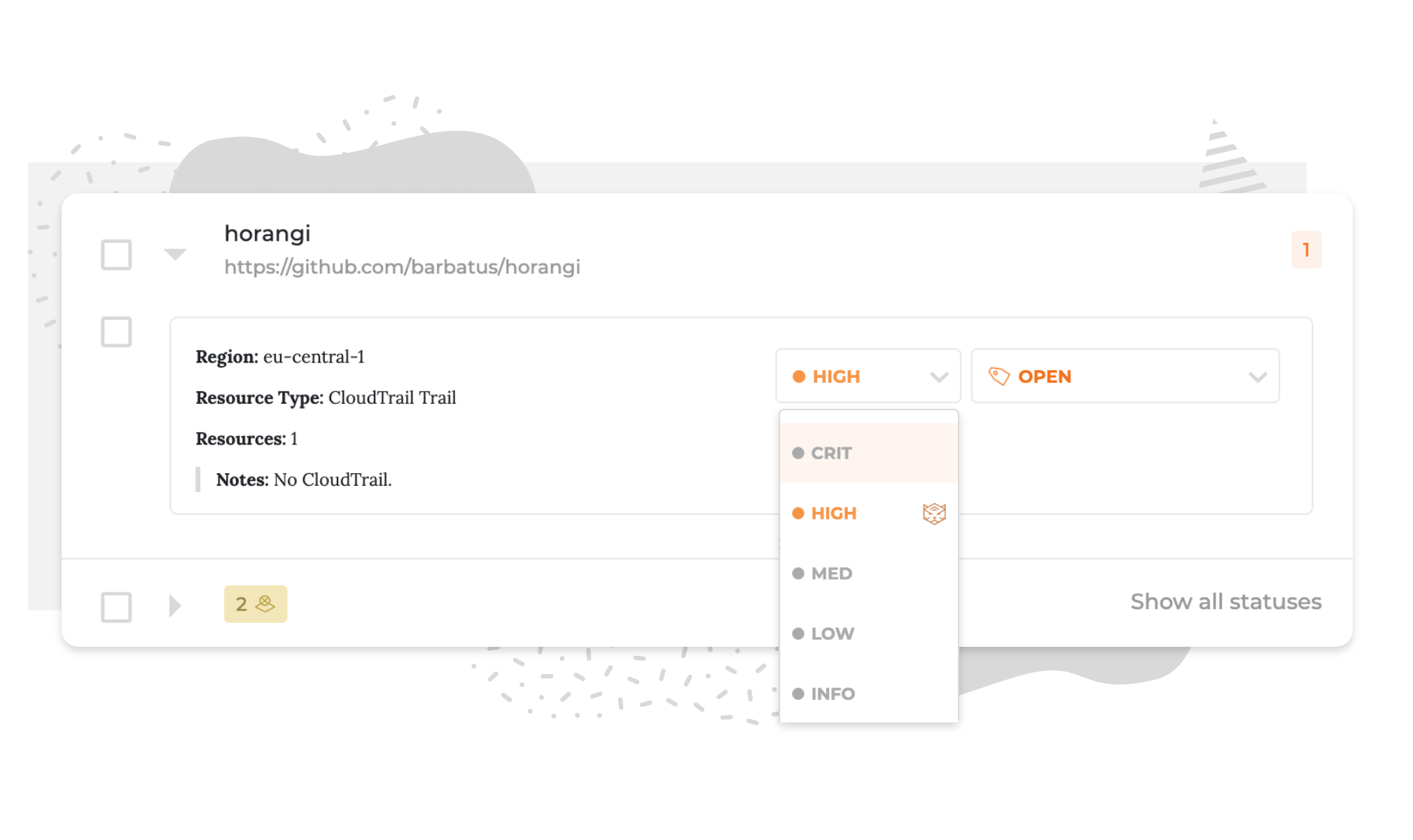
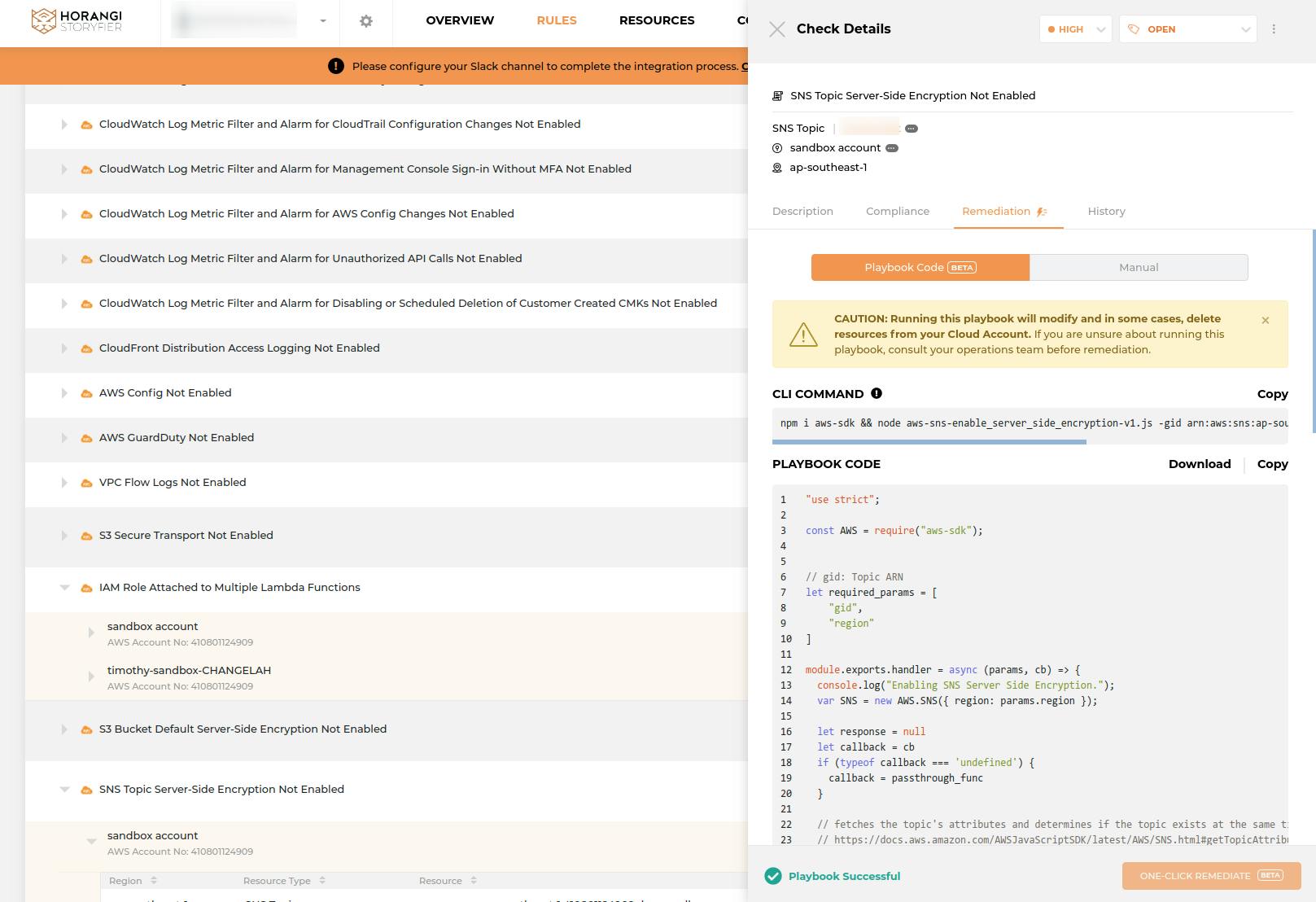
Warden's comprehensive rule set
You are equally responsible for cloud security as the service provider. Horangi Warden's cloud security scanner has over 250 rules and counting across AWS IAM, S3, ElasticSearch, GCP IAM, KMS, BigQuery etc. Each rule is complete with an appropriate risk value, description, and the option to execute a one-click or playbook remediation.
Stop security breaches that result from weak authentication of your cloud infrastructure
Secondary layers of authentication form a critical defense layer against unauthorized access from an attacker who has managed to hijack the root credentials through side-channel attacks or social engineering techniques. Without the added layer of authentication, an attacker may even gain access to Amazon EC2 control panels and have the ability to radically delete and modify data in your cloud environment including Amazon Simple Storage Service (Amazon S3) Buckets, AMI's, and Amazon Elastic Block Store (Amazon EBS) instances.
Related Warden rule below (click Implication and Recommendation):
Description
Implication
Recommendation
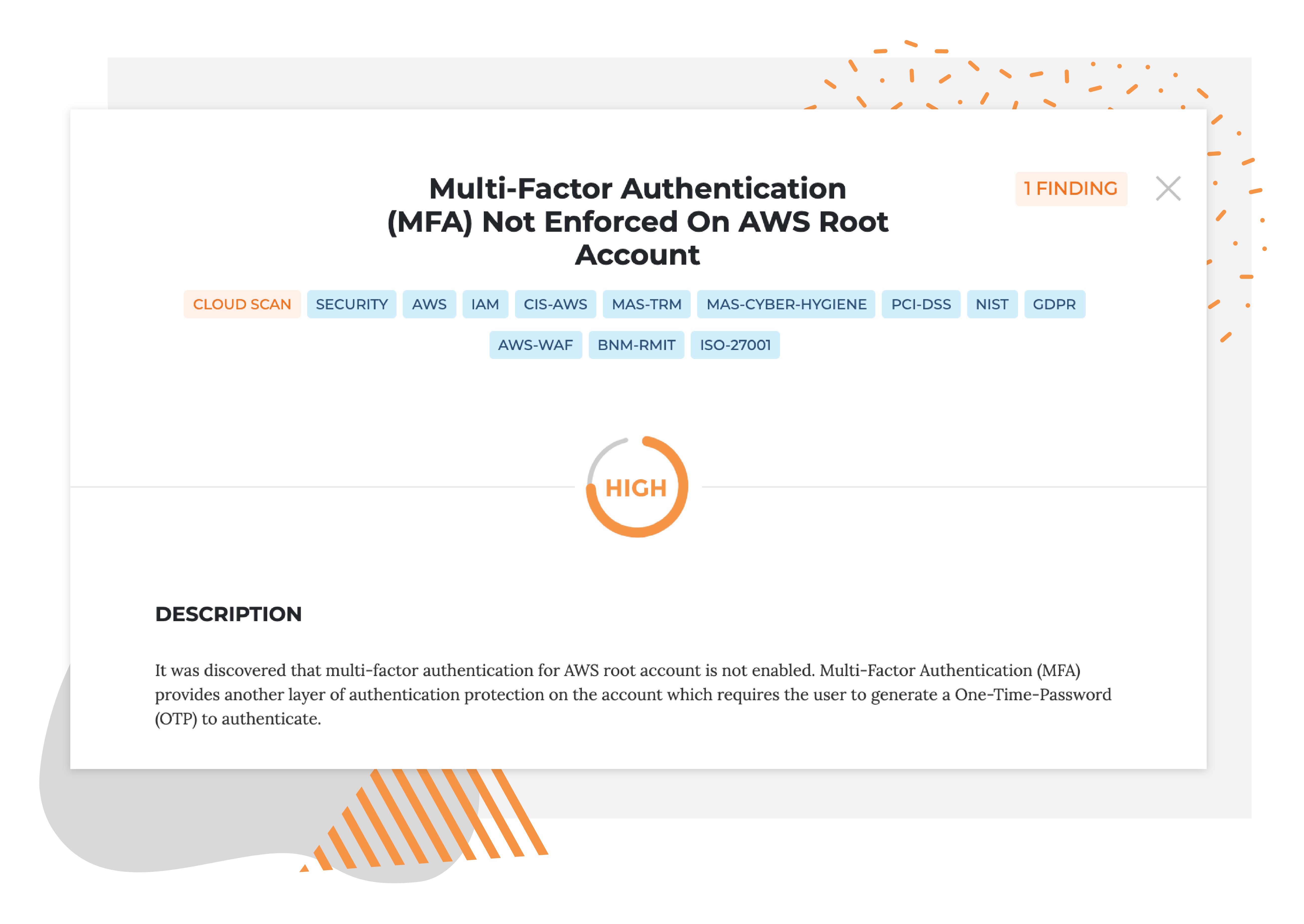
Description
What is the vulnerability?
It was discovered that multi-factor authentication for AWS root account is not enabled.
Multi-Factor Authentication (MFA) provides another layer of authentication protection on the account which requires the user to generate a One-Time-Password (OTP) to authenticate.
Get notified whenever excessive account permissions and admin privileges are granted.
Overly lax account permission policies can be a hotbed for account misuse as attackers are constantly on the lookout for access keys that have full admin privileges. Before a user accidentally uploads your organization's access keys to GitHub, Warden will alert you to the relevant security risks.
Related Warden rule below (click Implication and Recommendation):
Description
Implication
Recommendation
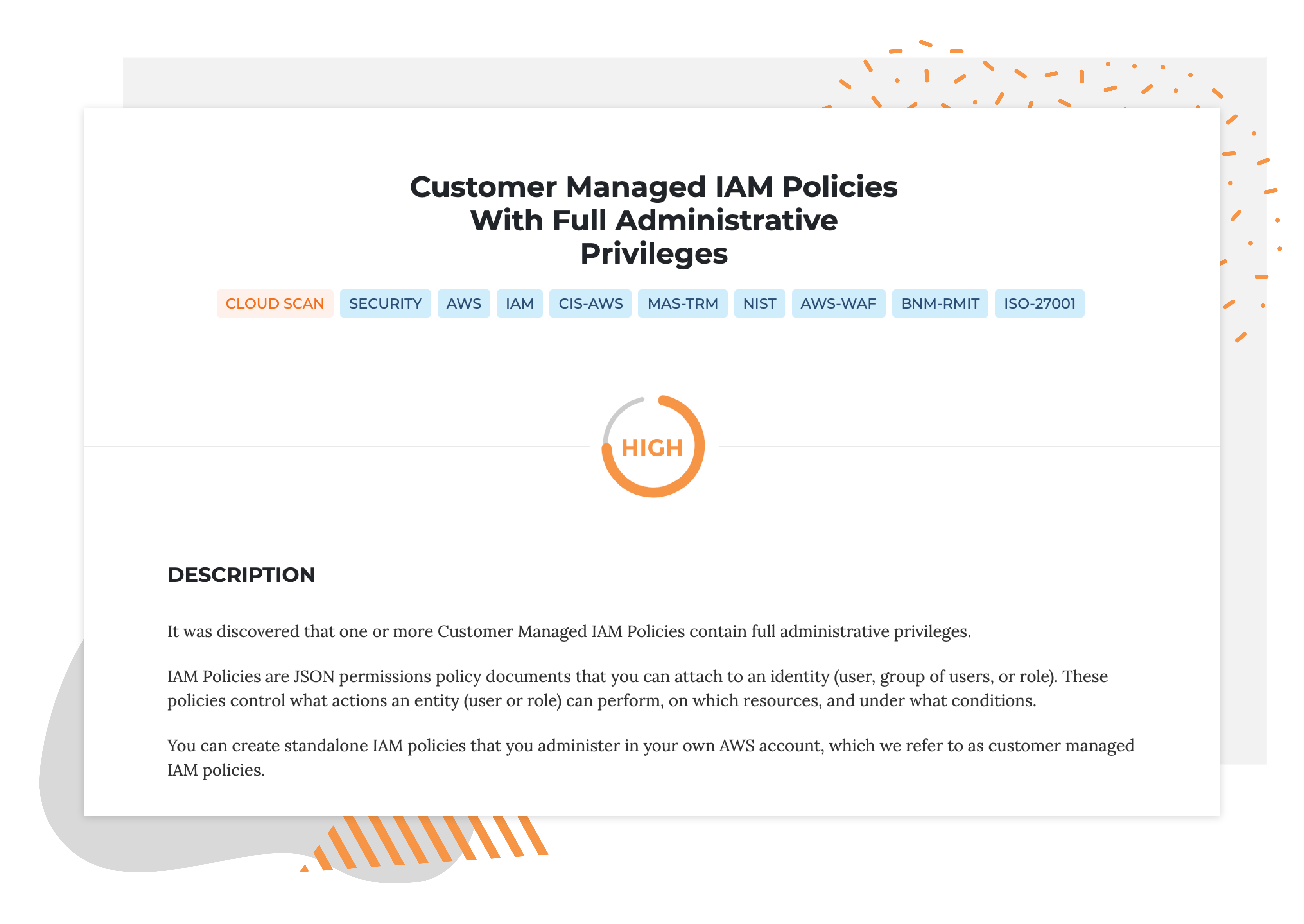
Description
What is the vulnerability?
It was discovered that one or more Customer Managed IAM Policies contain full administrative privileges. IAM Policies are JSON permissions policy documents that you can attach to an identity (user, group of users, or role).
These policies control what actions an entity (user or role) can perform, on which resources, and under what conditions. You can create standalone IAM policies that you administer in your own AWS account, which we refer to as customer managed IAM policies.
Prevent attacks that exploit excessive or misconfigured network connectivity in your AWS infrastructure.
Incorrectly configuring your EC2 security groups or ElasticSearch — a common problem during the software development lifecycle — can expose your sensitive data to the public. Warden helps you to detect this critical vulnerability before any bad actors do.
Related Warden rule below (click Implication and Recommendation):
Description
Implication
Recommendation
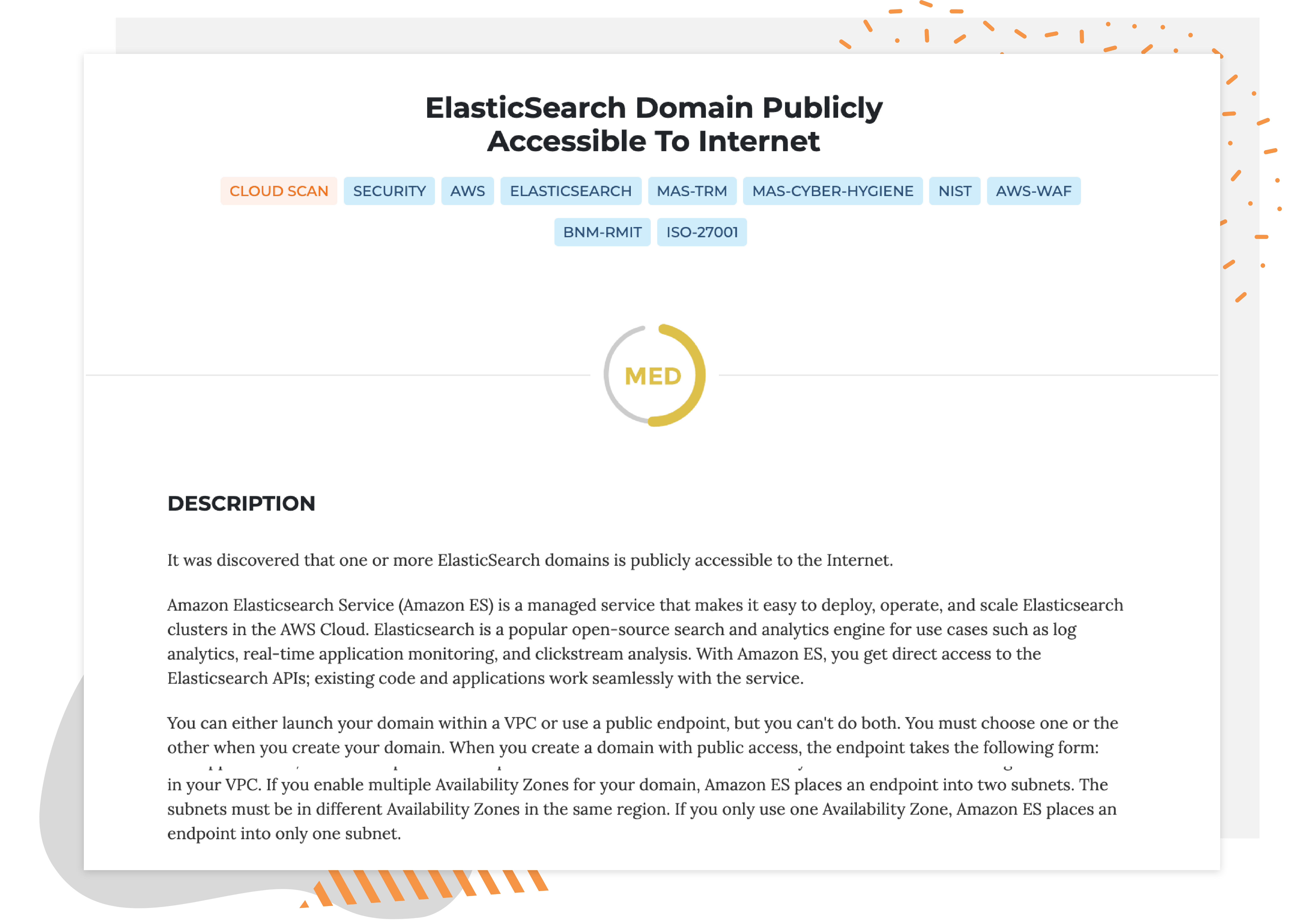
Description
What is the vulnerability?
It was discovered that one or more ElasticSearch domains is publicly accessible to the Internet. Amazon Elasticsearch Service (Amazon ES) is a managed service that makes it easy to deploy, operate, and scale ElasticSearch clusters in the AWS Cloud. ElasticSearch is a popular open-source search and analytics engine for use cases such as log analytics, real-time application monitoring, and clickstream analysis. With Amazon ES, you get direct access to the ElasticSearch APIs; existing code and applications work seamlessly with the service.

Workflow integration
Once turned on, Warden integrates seamlessly into your existing workflows for your organization to get working fast. With third party channel integrations that include Slack, Github, Bitbucket, and Jira, you can customize how you want to receive alerts for new Warden findings according to your organization's preferred workflow.