![]()
End-to-end security leadership and execution.
Horangi's cyber security as a service provides both the C-level security expertise and dedicated professionals needed to drive your organization’s digital initiatives.
What you get:
- Steering Committee Leadership and Participation
- Security Compliance Management
- Cyber Strategy & Risk Assessment
- Project Management
- Policy and Process Development
- Information Security Budget Management
- Security Recruitment and Hiring
- Security Training and Awareness
- Third-Party Vendor Security Assessments
- Business Continuity Planning
End-to-end security leadership and execution.
Horangi's cyber security as a service provides both the C-level security expertise and dedicated professionals needed to drive your organization’s digital initiatives.
What you get:
- Steering Committee Leadership and Participation
- Security Compliance Management
- Cyber Strategy & Risk Assessment
- Project Management
- Policy and Process Development
- Information Security Budget Management
- Security Recruitment and Hiring
- Security Training and Awareness
- Third-Party Vendor Security Assessments
- Business Continuity Planning
![]()
Meet compliance requirements.
Horangi helps organizations comply with frameworks and regulations including ISO 27001, SOC 2, PDPA, GDPR, and MAS TRM.
Other frameworks:
- ISO 27002
- ISO 27005
- ISO 31000
- NIST Cyber Security Framework
- NIST Cyber Risk Framework
- COBIT
- RAF
- PDPO
- HKMA-CRAF
Meet compliance requirements.
Horangi helps organizations comply with frameworks and regulations including ISO 27001, SOC 2, PDPA, GDPR, and MAS TRM.
Other frameworks:
- ISO 27002
- ISO 27005
- ISO 31000
- NIST Cyber Security Framework
- NIST Cyber Risk Framework
- COBIT
- RAF
- PDPO
- HKMA-CRAF

Horangi's in-depth knowledge of Singapore's financial regulatory landscape, combined with the professionalism of its consultant, makes it always a pleasure to work with them. In Horangi's hands, I can trust that my company is always well ahead of regulatory change.

Matt Lambie, Group CTO, Funding Societies
Horangi's in-depth knowledge of Singapore's financial regulatory landscape, combined with the professionalism of its consultant, makes it always a pleasure to work with them. In Horangi's hands, I can trust that my company is always well ahead of regulatory change.

Matt Lambie, Group CTO, Funding Societies

Talents make a clear difference in our work with third parties. Horangi's stong understanding of client needs, ability to elaborate problems into concrete solutions, and sheer ability to execute on these solutions make them a security vendor suitable for organizations of all sizes that need to embark on a similar ISO 27001 compliance journey.

Raden Ardiansyah Natakusumah, Head of Information Security, tiket.com

Talents make a clear difference in our work with third parties. Horangi's stong understanding of client needs, ability to elaborate problems into concrete solutions, and sheer ability to execute on these solutions make them a security vendor suitable for organizations of all sizes that need to embark on a similar ISO 27001 compliance journey.

Raden Ardiansyah Natakusumah, Head of Information Security, tiket.com
Talents make a clear difference in our work with third parties. Horangi's stong understanding of client needs, ability to elaborate problems into concrete solutions, and sheer ability to execute on these solutions make them a security vendor suitable for organizations of all sizes that need to embark on a similar ISO 27001 compliance journey.

Raden Ardiansyah Natakusumah, Head of Information Security, tiket.com
Talents make a clear difference in our work with third parties. Horangi's stong understanding of client needs, ability to elaborate problems into concrete solutions, and sheer ability to execute on these solutions make them a security vendor suitable for organizations of all sizes that need to embark on a similar ISO 27001 compliance journey.

Raden Ardiansyah Natakusumah, Head of Information Security, tiket.com
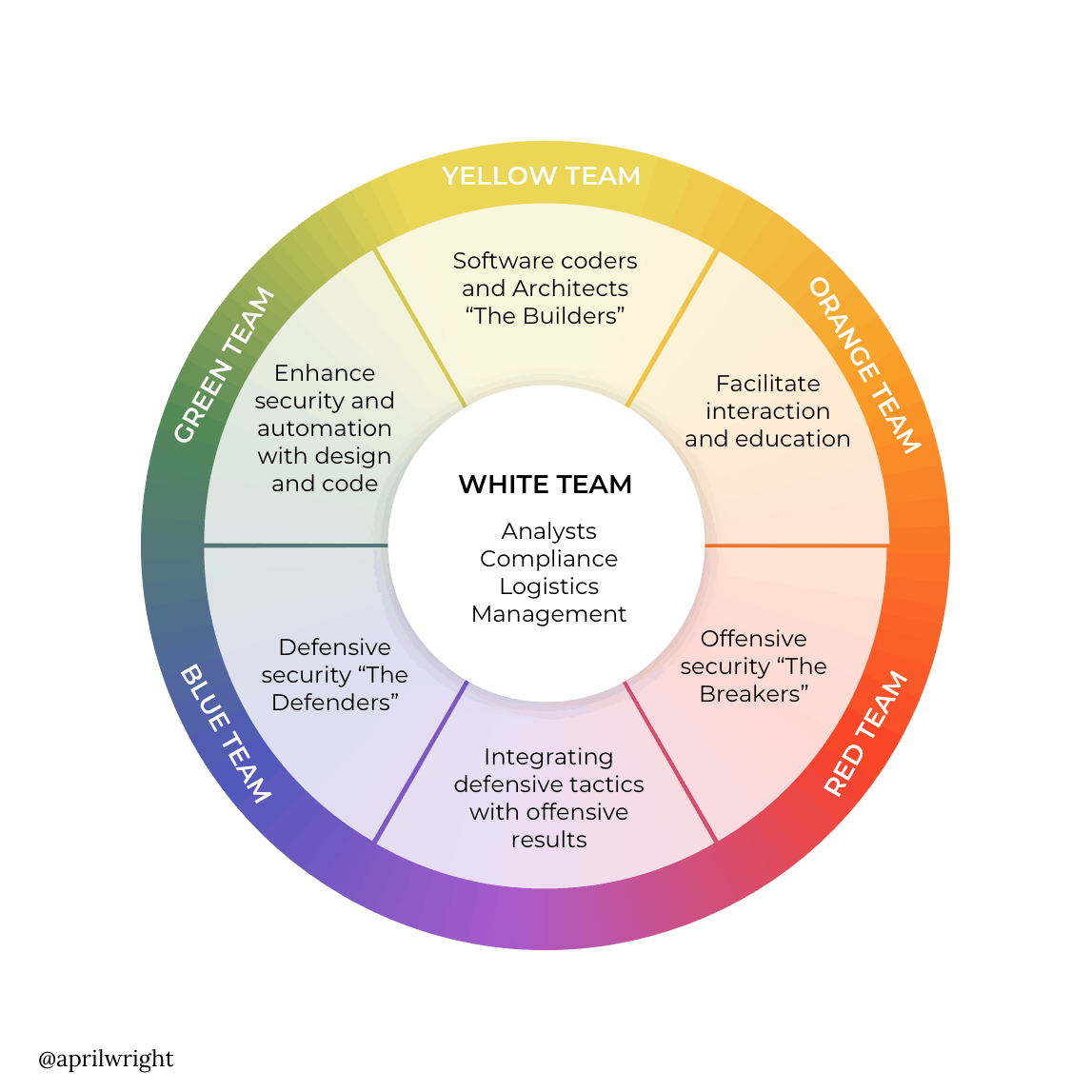
With expertise across the InfoSec Wheel, Horangi consultants analyze how all your teams operate to make your security spend efficient and impactful.
With expertise across the InfoSec Wheel, Horangi consultants analyze how all your teams operate to make your security spend efficient and impactful.
Schedule a Zoom meeting with us to understand your security and compliance priorities today.
Schedule a Zoom meeting with us to understand your security and compliance priorities today.
- Enable specific security capabilities including incident response, endpoint security, and email security
- Detailed project management with roadmap, time, and appointment of internal resources to focus on security implementation
- Develop and refine policies to match business objectives and manage data risks in the systems and environments operated by the organization
Make Security and Compliance Work Smarter

Need to show ROI on cybersecurity spend?
Quantify the reduction in your organization's cyber risk.
Need to show ROI on cybersecurity spend?
Quantify the reduction in your organization's cyber risk.

Compliance requirements deprioritized in favor of other items?
Leverage veteran security leadership to accelerate digital transformation.
Compliance requirements deprioritized in favor of other items?
Leverage veteran security leadership to accelerate digital transformation.

Organization not prepared for a security incident?
Build incident response capabilities and policies.
Organization not prepared for a security incident?
Build incident response capabilities and policies.
Our Certifications












More security spending doesn't lead to better protection
Mckinsey, 2019




