“Things will get better with time” — this is perhaps one of the most common cliches that we all have heard. And generally most things do get better (read evolve) with time, as we learn the intricacies of the trade. But can you confidently say the same about your security stack? Has it evolved over time to handle the recent spike in breaches?
If you are hesitant or only partially confident about answering this question, then here’s why you should consider investing in a tool which helps with threat identification, like using frequent dynamic scans. It is essential because as we continue our cybersecurity journey, we often get caught up in those everyday tactical tasks, and don’t get enough time to ask ourselves, what’s next? How should we evolve our cloud security best practices and execution to improve our security programs? Are we thinking like a security pioneer? Or just simply adding (or not adding) some new items that make our cloud security efforts actionable and sustainable.
These are some thoughts and questions constantly on our minds. As a Cybersecurity organization, building a safer cyber space is at the core of our vision. And to overcome some of the challenges mentioned above, our CSPM tool Warden now has the ability to help you overcome most of these challenges with Warden Dynamic scans, as you sit back and let it do the heavy lifting for maintaining your cloud security posture.
Wait, why should you be identifying cloud threats in real time?
One of the best things an organization can do is to add some way of threat identification to its framework. This approach is nothing new, but unfortunately it is not used in most security organizations. With cybersecurity-savvy executives forming less than 10% of board members today, there isn’t enough emphasis on building a proactive threat identification and mitigation strategy. Threat identification iIn many cases is a key differentiator between regularly stopping hackers and ongoing, undiscovered data loss. If a threat is detected, mitigation action must be taken quickly to properly neutralize the threat before it can exploit any present vulnerabilities or misconfigurations.
How can you identify cloud threats in real time?
To identify cloud threats in real-time, organizations can adopt a proactive approach to risk mitigation. One way is by having a CSPM tool with dynamic scanning capabilities. Having a consolidated solution (Gartner mentions that 80% of organizations are interested in vendor consolidation strategy) such as Horangi Warden will save you effort and time.
Consider the possibility that no network is attack proof. If you don’t have the tools, people, and the process in place to detect and respond with speed, hackers will find and abuse your crown jewels, your most sensitive resources. Hence, it’s crucial to build up your threat identification and response capabilities before you’re compromised.
Whether it is to prevent data breaches or get help managing your cloud security posture, you can count on Warden CSPM.
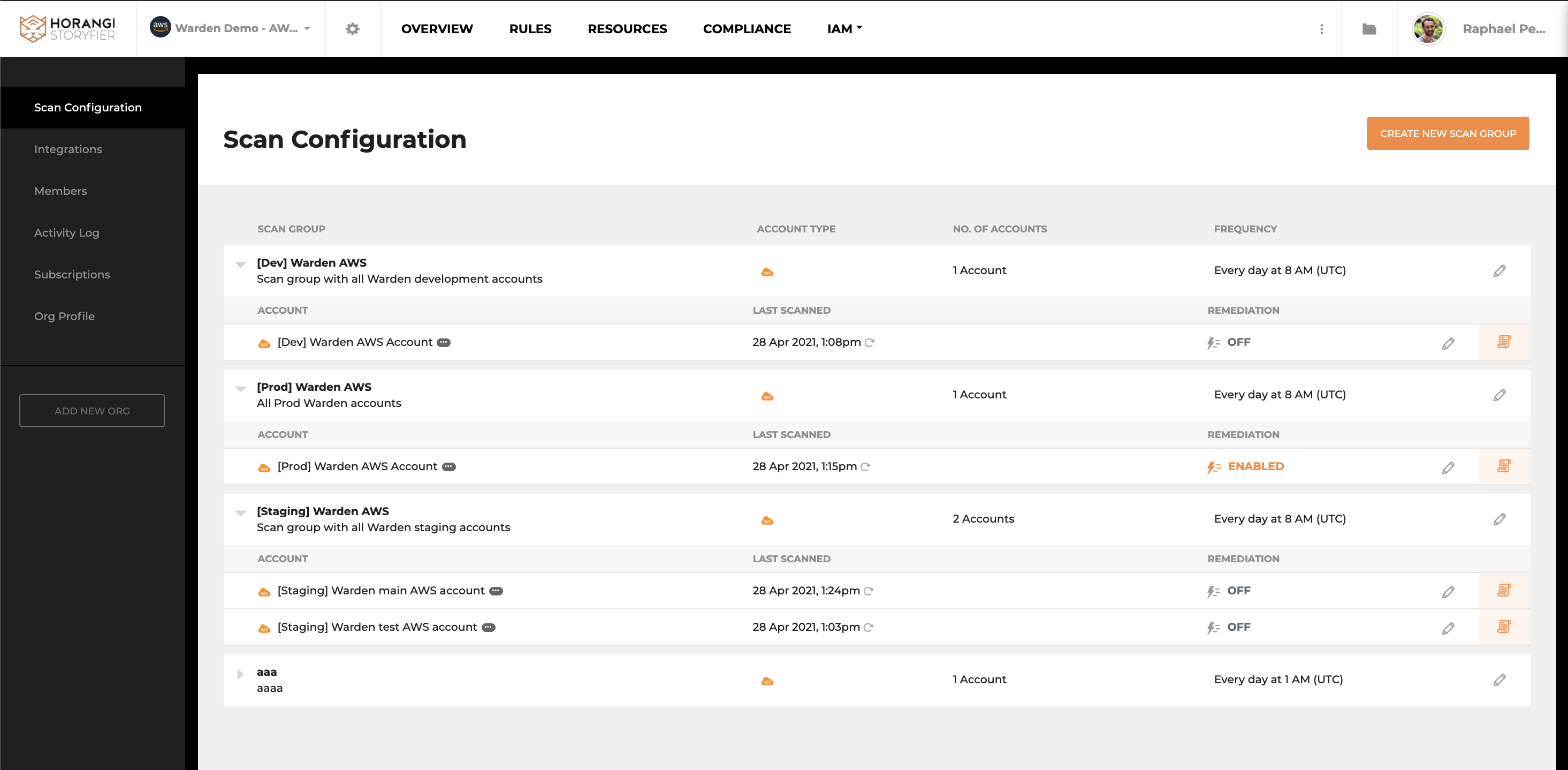
Warden Dynamic scans
To put it in perspective, think of a CSPM as security software for your home. It tells you when you forget to close a door or a window, and with threat detection, it now also tells you whenever an intruder is near your door. This is precisely what a good threat identification feature can help you overcome, minimizing the time to threat detection to improve your overall cloud security posture.
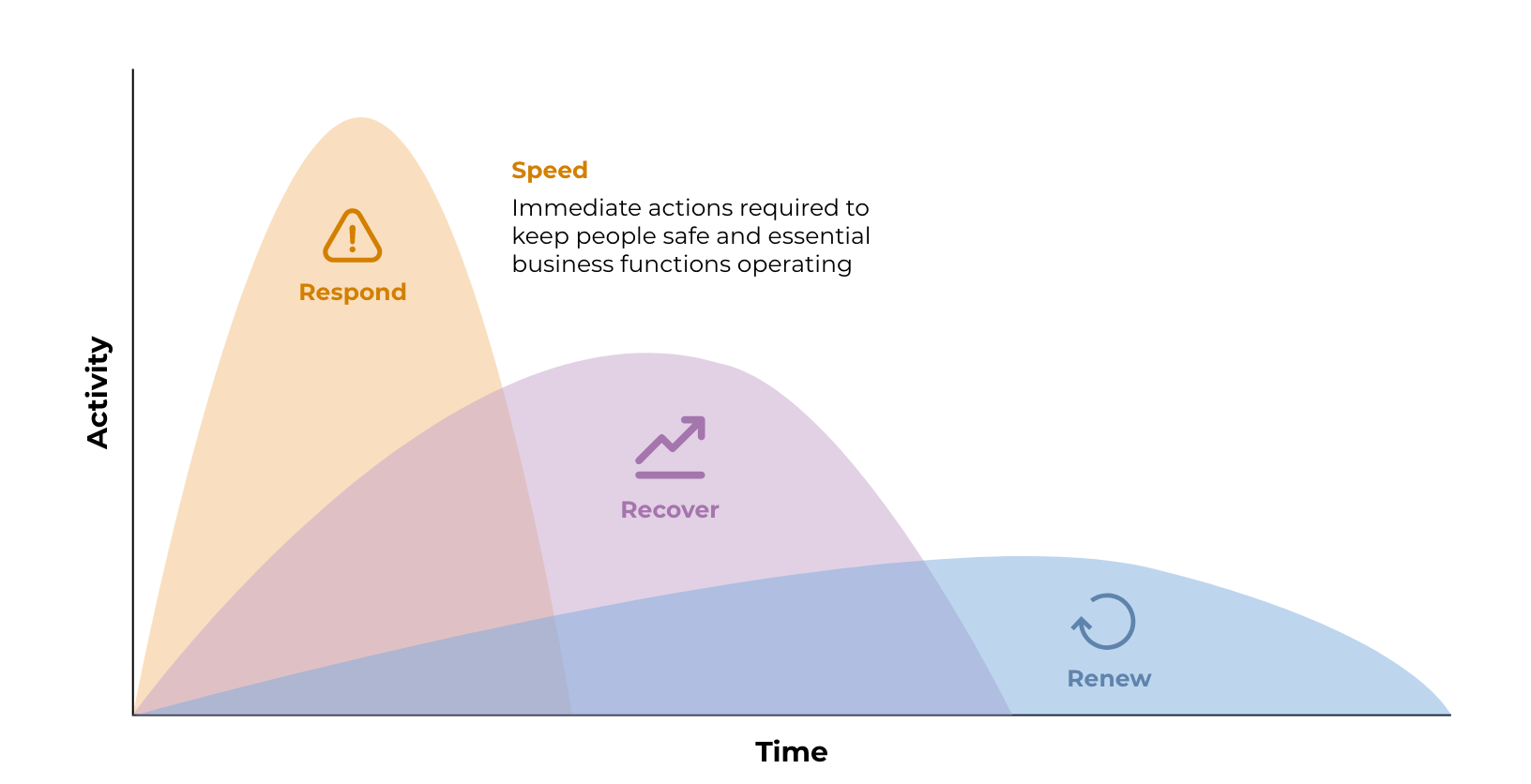
Speed is more important than accuracy while mitigating risks.
What can Warden Dynamic scans help me achieve?

1. Real-time misconfiguration detection: Attackers don’t work on a fixed schedule, so if you want to spot them early then scheduled scans of your infrastructure aren’t enough. You need to detect any misconfigurations made to poke holes in your cloud security in real-time, so that you can respond.
2. Real-time incident notifications: Get notifications sent to your preferred communication channels that your security team uses, by integrating with Slack or any SIEM.
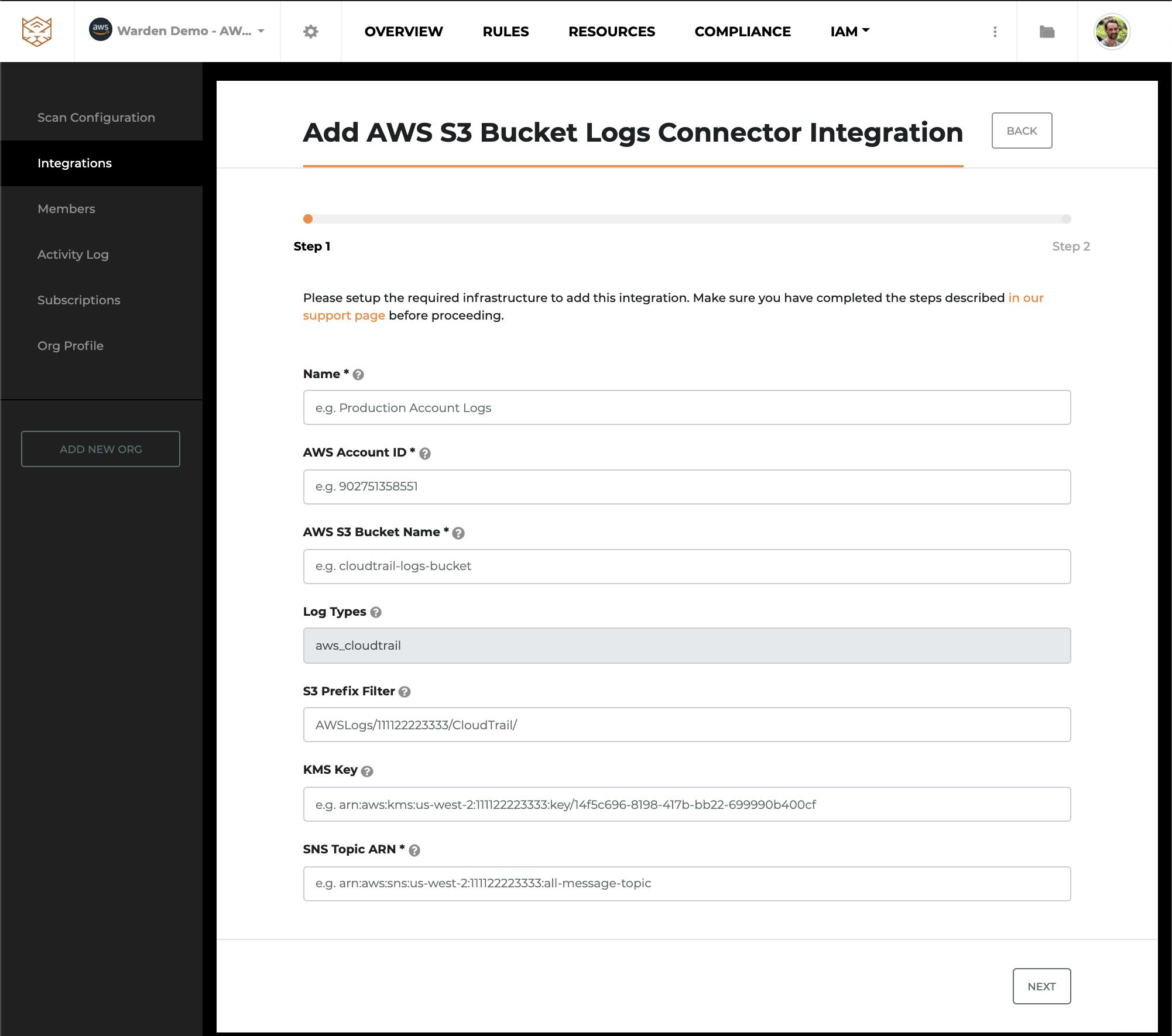
AWS S3 bucket logs container integration to get real time notifications
3. Automation and response: Quickly understand what’s going on with context-rich details of identified risks, and remediate issues in one command or one click.
4. Continuous compliance: Constantly stay in compliance with the fast detection times that Dynamic Scans can give you.
See it in action
To learn more about how your team can build a top-notch security program and make use of the most cutting edge Horangi Warden features, fill-up this form and our specialist will reach out for a live demo of Warden in action.
P.S. Warden dynamic scans are currently available only for Amazon Web Services (AWS) cloud environments. We are working on rolling these out for other cloud solution providers in the coming months.




