We are thrilled to announce the open beta of Warden's integration with AWS Inspector, taking a major step towards empowering organizations to effortlessly strengthen their cloud infrastructure. During this open beta phase, we invite you to join us in testing and providing valuable feedback as we fine-tune this new feature.
What is AWS Inspector?
AWS Inspector, a service provided by AWS, plays a crucial role in cloud security. It enables the discovery of cloud workloads such as EC2 instances, containers, and lambda functions, scanning them for software vulnerabilities. AWS Inspector utilizes the Common Vulnerabilities and Exposures (CVE) database to identify vulnerabilities and helps uncover unintended network exposures.
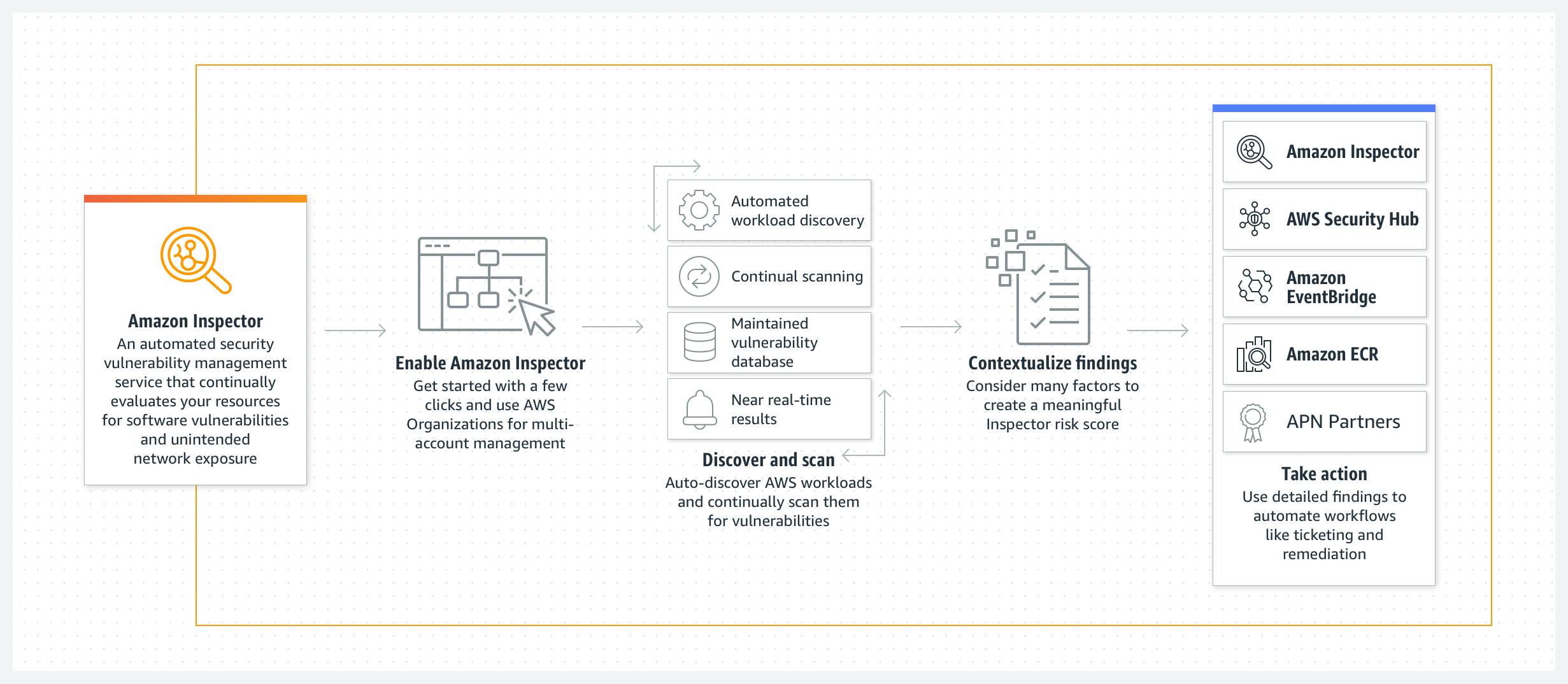
Why is this Integration Important?
Cloud security remains a top priority for organizations, including yours. As the adoption of cloud services expands attack surfaces, there is an increasing need for proactive protection. The integration of Warden with AWS Inspector addresses this critical need and offers users the following key benefits:
- Single pane of glass:
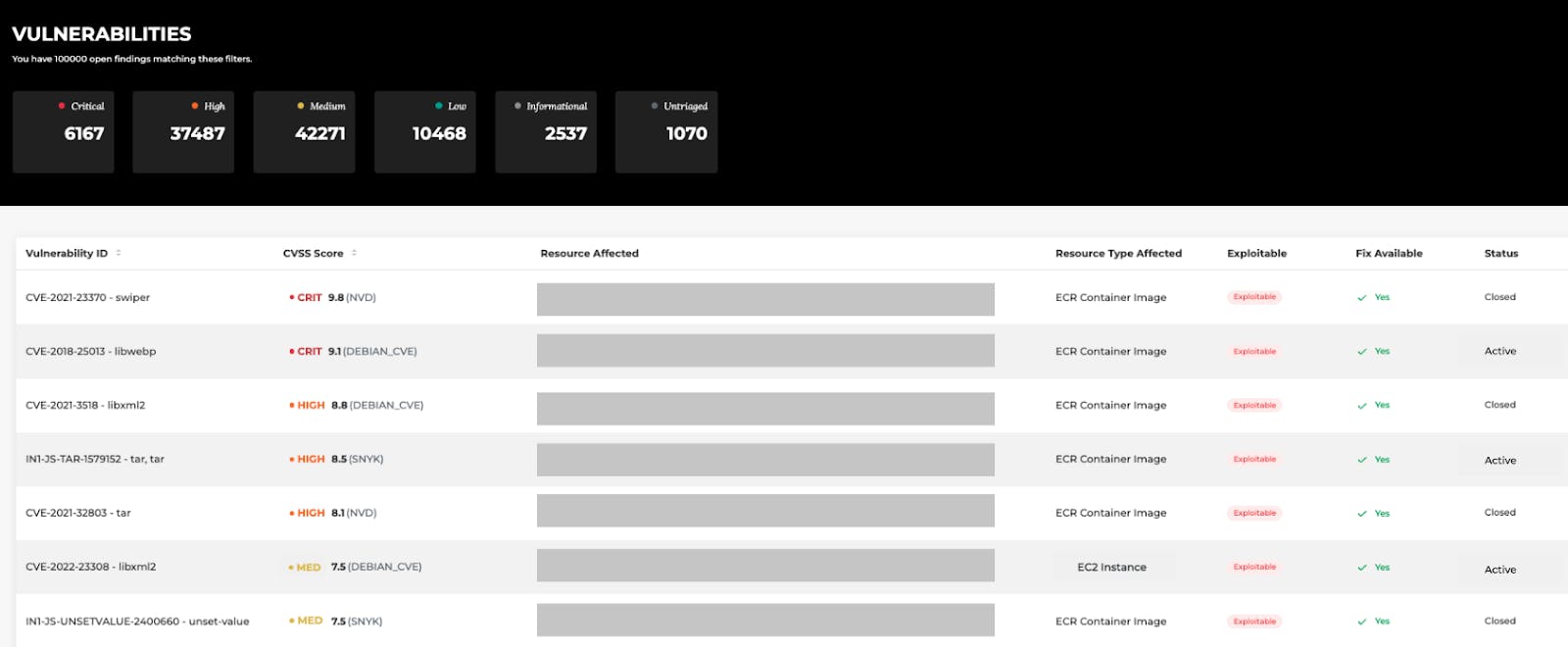
Warden's integration allows users to consolidate all their security findings from AWS Inspector and Horangi Warden in one place. This consolidation simplifies security operations, ensuring that everyone is looking at the same source of truth. With a unified view, organizations can effectively manage and respond to security vulnerabilities.
- Prioritize through context correlation:
In addition to consolidating findings, Warden provides context correlation across different security findings. This capability allows users to gain a more holistic understanding of their cloud infrastructure, encompassing both the cloud configuration and workload layers. By prioritizing security efforts based on contextual information, organizations can focus on critical assets and take targeted remediation actions.
Getting Started
Existing Horangi Warden customers can seamlessly integrate their Amazon Inspector subscription without any additional setup or configuration. The integration leverages the pre-existing AWS Identity and Access Management (IAM) role that was provisioned for Horangi Warden. Simply reach out to your customer success representative to enroll in the open beta program and unlock the enhanced capabilities.
If you have not yet used AWS Inspector, setting it up is a straightforward process, well-documented in the official AWS guide. Take the opportunity to leverage this powerful tool in combination with Warden to fortify your cloud security.
Conclusion
Unleash the full potential of your multi-cloud platform security with Warden, the comprehensive cloud security solution encompassing Cloud Infrastructure Entitlement Management (CIEM), Cloud Security Posture Management (CSPM), Real-Time Threat Detection, Vulnerability Remediation, and Compliance Automation capabilities. If you are excited to learn more about securing your cloud infrastructure, we encourage you to reach out and connect with us. You can read our blogs here or drop us a line here. Together, let's reinforce your cloud security and stay one step ahead of emerging threats.




