Identity and Access ManagementIdentity and Access Management controls the permissions and access for users and cloud resources. IAM policies are sets of permission policies that can be attached to either users or cloud resources to authorize what they access and what they can do with it. You can read more about Warden IAM here.
In our previous blog, we talked about Access Graphs and how you can make the most of Warden IAM by using them to get a visual representation of who has access to what in your infrastructure. Now with these feature enhancements, Warden IAM can help you go an extra mile when it comes to managing dormant identities in your network.
Feature Update 1: Identifying Inactive and Unused Identities
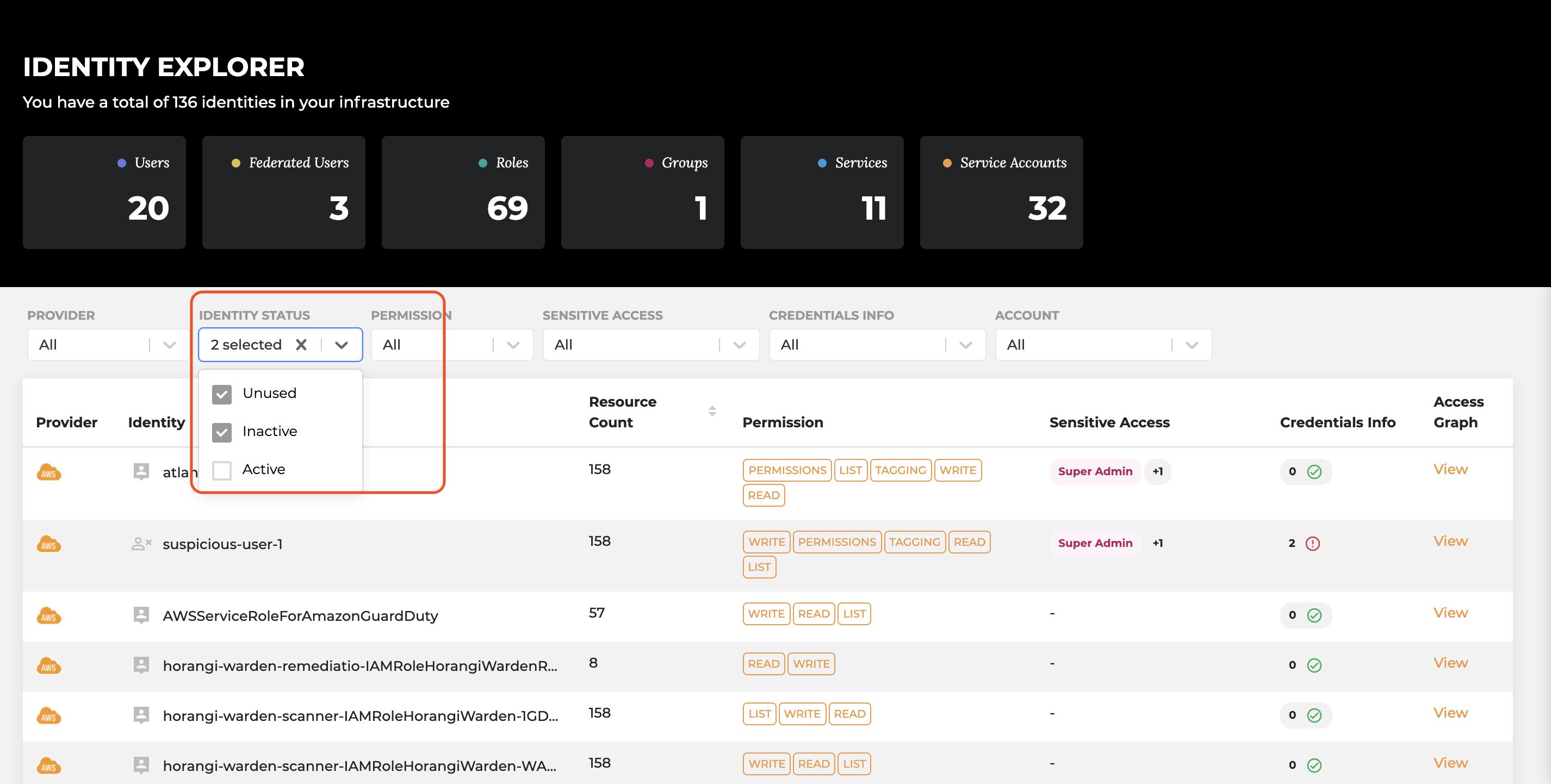
We recently introduced scoping and identification for 6 Additional Inactive and Unused Identities. Here’s what you can find on your dashboard now:
- Inactive Role: Roles that were last used more than 90 days ago
- Unused Role: Roles with no last used data, not used at all
- Inactive Group: Members in the group were last active more than 90 days ago
- Unused Group: Empty group, with no users in it
- Inactive Service Accounts: Service accounts that were last used more than 90 days ago
- Unused Service Accounts: Service accounts with no last used data, not used at all
Why is this feature needed?
- To assist Warden IAM users in reviewing dormant identities across their cloud accounts and providers (i.e. AWS, and GCP) on a unified dashboard and provide a seamless single-pane-of-glass experience
- A more complete list of roles, groups, and identities for better comprehensive security review
What value does it add for a security team user?
- Most cloud workloads have a huge number of dormant identities and it is nearly impossible to manually track and remove them. With Warden IAM, you can expect these inactive and unused identities shown on the IAM Dashboard and easily remediate them to your liking.
- You can also segregate and filter them by selecting “Inactive” or “Unused” identity status and quickly identify the dormant identities in Identity Explorer. This helps you put a pin on a specific identity and what access it has in your network. Something which can be beneficial while doing an in-depth security review.

Note: To review GCP service accounts inactivity on Warden IAM, you will need to add new permissions:
Step 1: Add GCP Role Activity Analysis Viewer to cloudscanner service account
Step 2: Enable policyanalyzer API here: https://console.cloud.google.com/apis/api/policyanalyzer.googleapis.com/overview
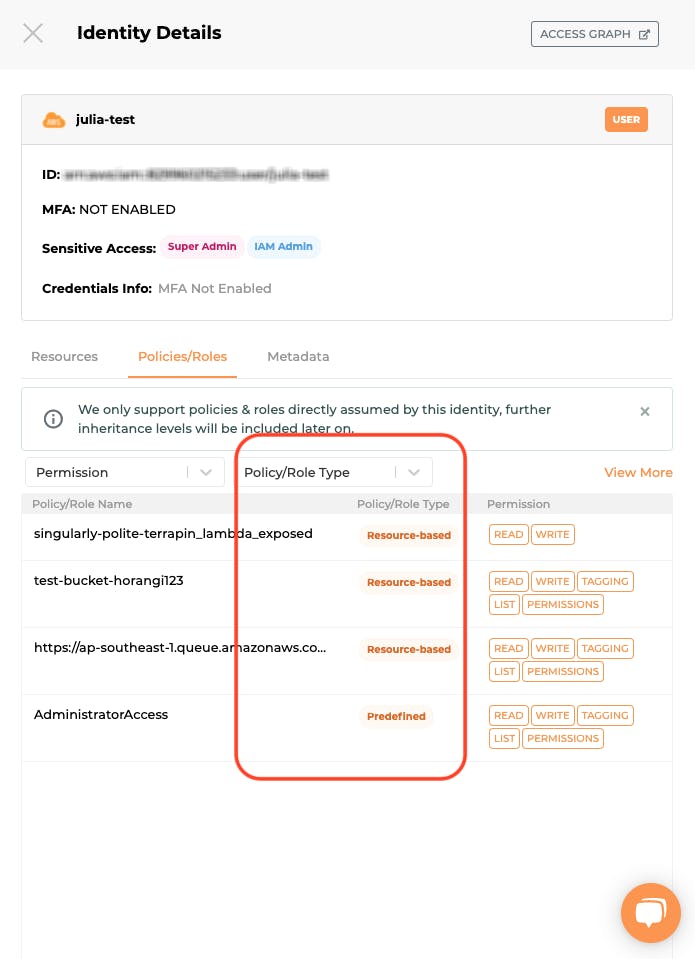
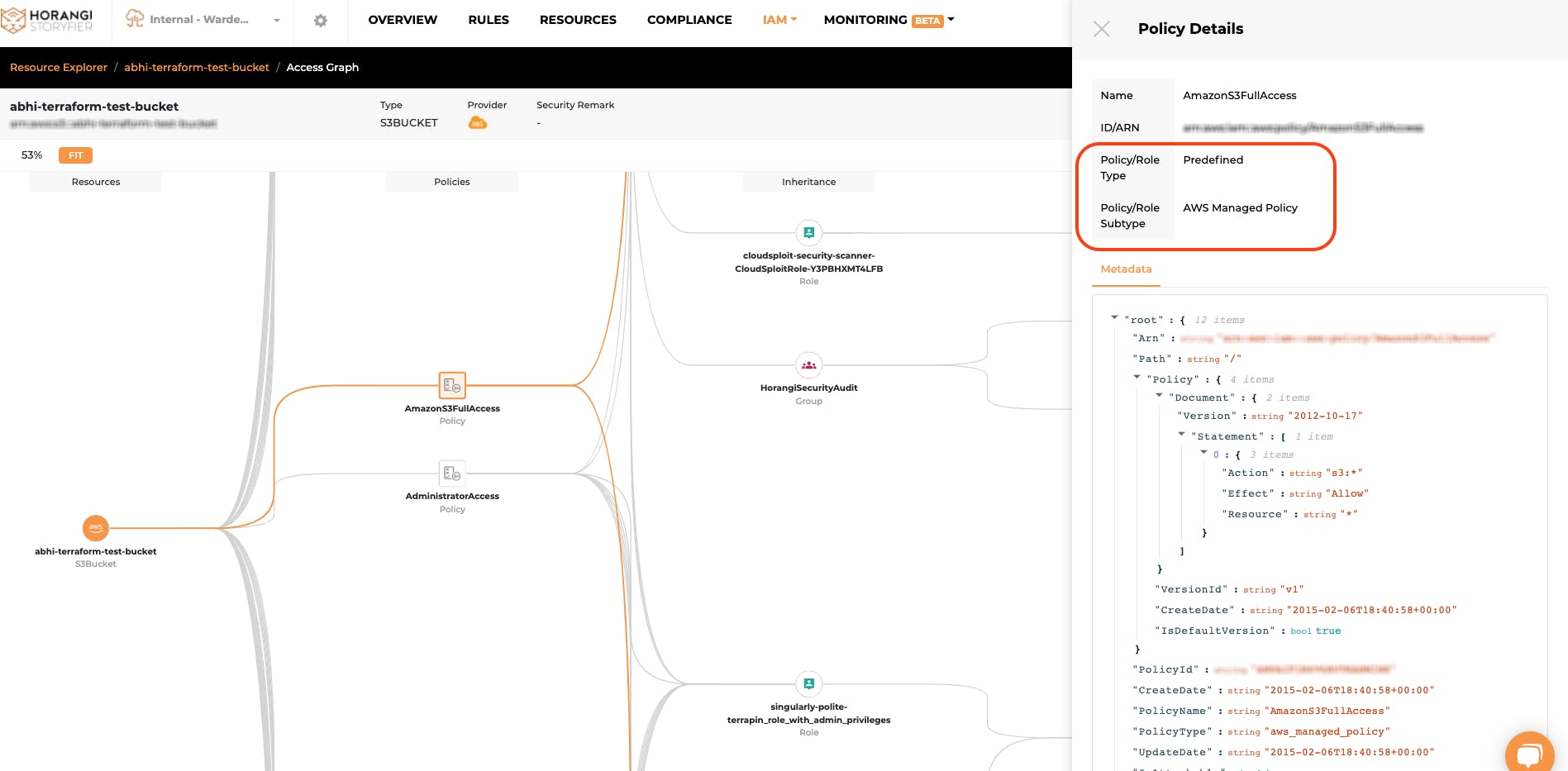
Feature Update 2: Introducing Policy/Role Type Information
Warden IAM now has “policy/role type” listed as a category for easier understanding of where the policy or role was initially set up and managed.
- Predefined: Predefined entitlements created by cloud service providers (i.e. “AWS Managed Policy”, “GCP Basic Roles”, “Predefined Roles”)
- Custom: Custom entitlements created by customers (i.e. “AWS Customer Managed policy”, “GCP Custom Roles”)
- Identity-based Inline: Custom entitlements embedded to the identity (i.e. “AWS Identity Inline Policy”)
- Resource-based: Custom entitlements embedded to the resource (i.e. “AWS Resource-based policy” )
Why is this feature needed?
Policy/Role type information was a highly requested feature from most of the Warden IAM customers. This feature is needed to filter and categorize the long list of policies granted to the users, which were earlier ‘uncategorized’ and created a lot of noise and overhead in the reviewing process.
What value does it add for a security team user?
- With this feature add-on, Warden IAM users can quickly understand where the policy 'comes from' that granted access for the identities and resources in the Identity Drawer, Resource Drawer, and in the Access Graph
- Users can now filter the Policy/Role Tab with focussed attention and don’t get overwhelmed with the findings
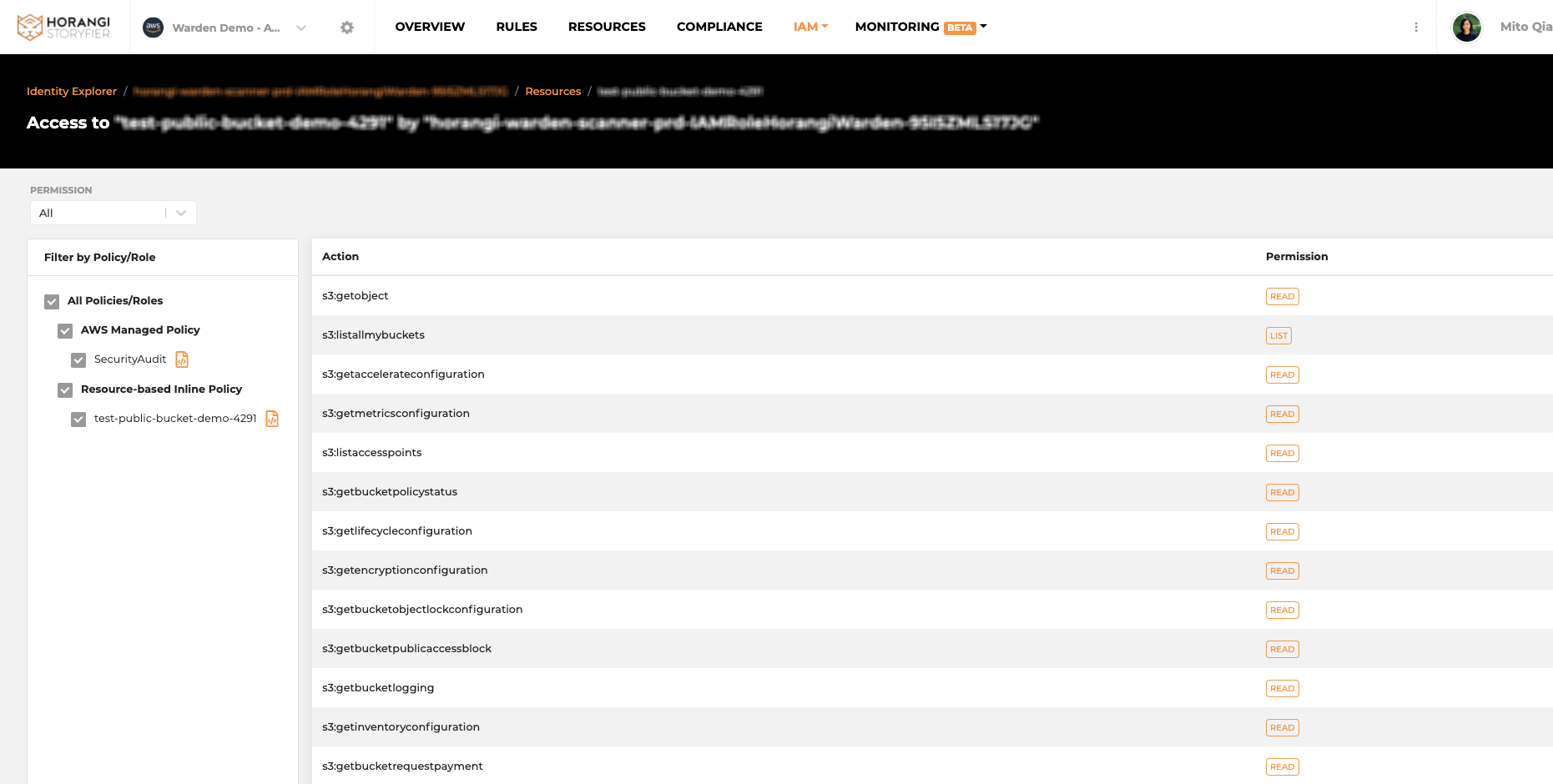
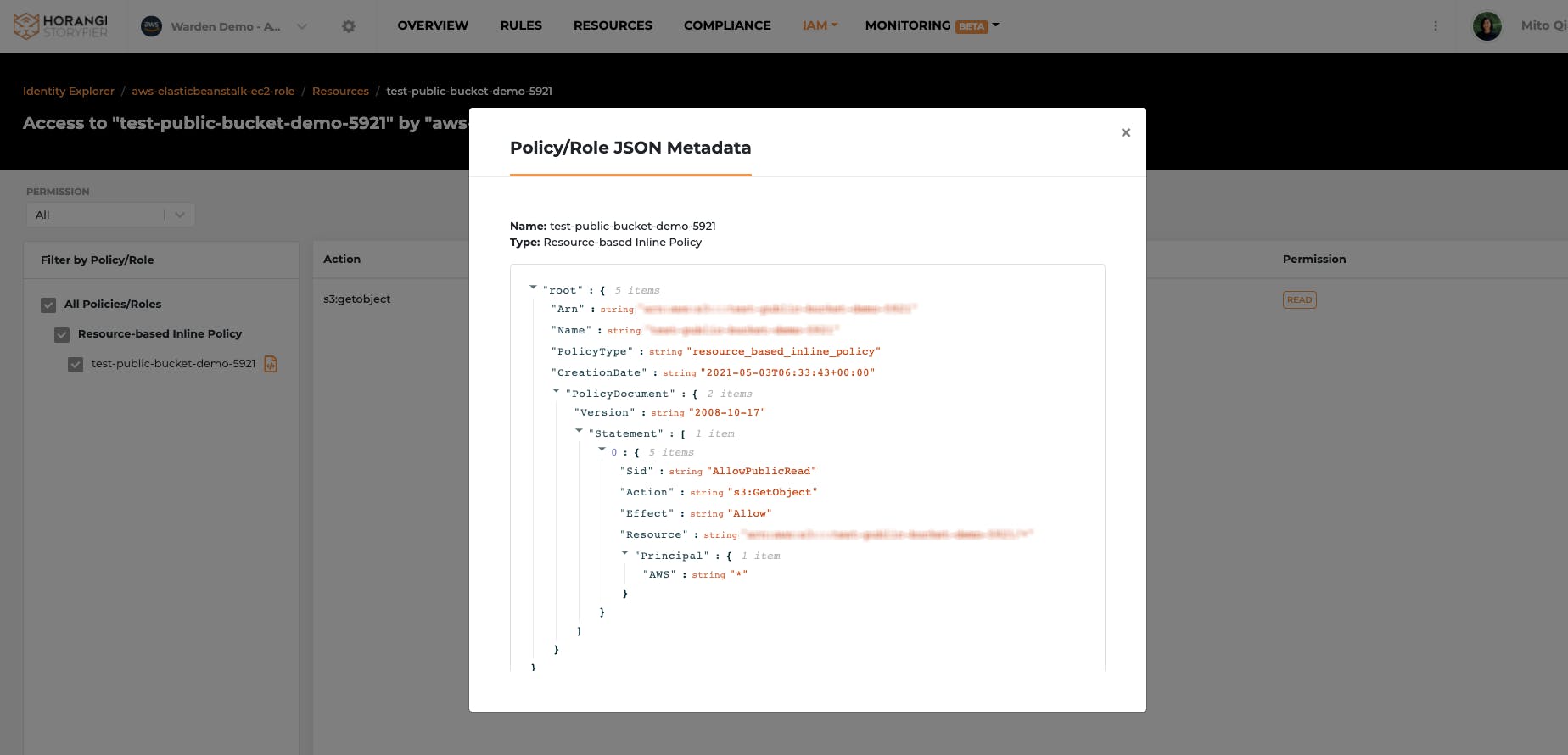
Feature Update 3: Permissions Action Page Reimagined
We reimagined the look and feel of the Permissions action page for the IAM dashboard. With this revamp, users have more filtering options and preview scope for policy details. We have also included an accurate and flattened view of exactly what permission has been granted to a specific identity on a specific resource instance.
Why is this feature needed?
- With these enhancements, we expect an increase in the accuracy of the data presented on the page
- This will also help users to narrow down a specific policy that grants certain unintended actions, so users can determine which policy requires rightsizing and do so.
What value does it add for a security team user?
- The action list on this enhanced interface is more accurately presented for users to take action
- Users can further filter by the policy name or type to shorten the list for review
- Users can easily review the policy details to understand how the access was initially granted
Conclusion
We hope that this blog post will help you make the most of your Warden IAM. In case you haven’t taken Warden for a spin yet and you are having trouble answering “who has access to my crown jewels and how did they get the access?” then get in touch with a Horangi Specialist for a quick demo of Warden, a comprehensive cloud security tool with IAM, Threat Detection, and Posture Management capabilities.




