As your organization moves more operations to the cloud, it’s high time you consider how to use existing and new instruments to protect against advanced threats.
While cyber threats were arguably “simpler” before, many cybersecurity veterans would agree that today’s threat landscape has become more complex and sophisticated.
For example, some ransomware threat actors have banded together to launch Ransomware-as-a-Service (RaaS) to offer their tools and discovered vulnerabilities to interested parties keen on making a quick small fortune.
The good news is that Cloud Security Posturement Management (CSPM) tools, such as Horangi Warden, are still viable options for detecting and mitigating threats, regardless of how advanced they are.
Why use a CSPM?
Cloud Security Posture Management (CSPM) tools like Horangi WardenHorangi Warden may have been around for some time, but they are still critical to securing any organization's cloud infrastructure.
At the most basic level, CSPM tools help you understand your organization’s security posture and identify and remediate misconfigurations and vulnerabilities that attackers could exploit.
However, as the threat landscape evolves, so must your CSPM strategies.
While you’ve probably deployed traditional CSPM strategies to focus on identifying and addressing fundamental security issues, it’s time to look into advanced CSPM techniques to protect against the increasingly sophisticated threats facing cloud environments today.
What are these advanced threats?
We’ll look at some of the most common advanced threats facing your cloud environment today and offer suggestions on using a CSPM to overcome these challenges and neutralize the potential damages.
Malicious Insider Attacks
Insider attacks are not new, but they are growing in popularity.
They are carried out by disgruntled employees or, worse yet, disgruntled ex-employees who have been let go of by your organization.
The current economic situation where many organizations are letting go of employees is the perfect environment for such attacks if you do not entirely rescind the access rights of such employees correctly and in good time.
Disgruntled employees with legitimate access may use their privileges to access and steal sensitive information and even disrupt operations.
To counter this threat, organizations should use advanced CSPM strategies such as User and Entity Behavior AnalyticsUser and Entity Behavior Analytics (UEBA) and advanced threat detection to detect and respond to suspicious activity.
The UEBA in your CSPM helps baseline normal user behavior, so you can quickly spot errant user behaviors. This enables you to identify and investigate potential threats and break the attack chain before it has time to germinate.
For example, you can use UEBA to determine if a potential insider threat is an external party pretending to be an employee or an actual employee who presents a level of risk by identifying and flagging suspicious activity, such as accessing data on the corporate network from a different IP address.
A simple example would be a case where you suddenly notice that a local employee is accessing sensitive information from a location they are not known to be in or at very different times from their usual schedule.
Cloud-Native Threats
Cloud infrastructure is unique, and as with every new technology, they come with associated risks unique to the environment, platform, and related technologies.
Cloud-native threats are malicious activities that leverage cloud infrastructure capabilities to evade detection and cause harm.
You may have heard of some of these threats before but didn’t register them as cloud-native. Some of the top cloud-native threats include:
- Overprovisioned access
- Misconfigurations
- Application vulnerabilities
- Insecure APIs
- Malware
Advanced CSPM strategies such as continuous security validation and cloud workload protection (CWPP) are excellent tools for detecting and responding to these cloud-native threats.
Continuous security validation
Continuous security validation involves using automated tools to regularly scan your organization's cloud infrastructure for vulnerabilities and misconfigurations and then providing remediation recommendations.
This allows you to quickly identify and address security issues before attackers can exploit them.
Cloud Workload Protection (CWPP)
Gartner defines Cloud Workload Protection (CWPP) as a “workload-centric security solution that targets the unique protection requirements.”
What are workloads, then?
Essentially, workloads include physical servers, virtual machines (VMs), containers, and serverless workloads that provide the underlying computing, transport, and storage of the data that deliver application functionality.
Using a CWPP like the one available with Horangi Warden can help you identify and mitigate those vulnerabilities, making it harder for attackers to achieve anything from targeting your cloud infrastructure.
Threat Modeling
A CSPM does not only help you identify clear and present threats to your cloud environment.
Some users may not be aware of this, but CSPMs are also great for helping you identify potential threatspotential threats to your organization's cloud infrastructure and help you develop strategies to mitigate those threats.
For example, a CSPM may help you identify that a particular application is a potential target for attackers. You can then use that information to develop a security policy for that application by implementing additional security controls and monitoring for suspicious activity.
Threat Intelligence
Another critical aspect of advanced CSPM is threat intelligence.
You can use this approach to gather and analyze known and emerging threats and use this information to identify and mitigate potential security issues in your cloud environment.
For example, you can use threat intelligence feeds to identify and block known malicious IP addresses or domains or detect and respond to new attacks.
Automated Remediation
Closely related to threat intelligence is automated remediation.
Automated remediation involves using automated tools and processes to quickly and efficiently address security issues in cloud environments, such as configuring security settings or patching vulnerabilities.
For example, Horangi Warden has four types of remediation, and automated remediation is one of them. It has been helpful for most of our users to remediate threats they are unfamiliar with or for which they do not have the resources to remediate manually.
This advantage can help you quickly address security issues before attackers can exploit them and reduce the time and resources required to manage and secure cloud environments.
Finally, you can use automated remediation to reduce or eliminate the risk of human error and ensure that security issues are addressed quickly and consistently.
The Future
A look at new threats in the future won’t be complete without looking at upcoming technologies that are beginning to be included with Cloud Security Posture Management tools, such as artificial intelligence (AI) and machine learning (ML).
Unlike humans, ML and AI can analyze large amounts of security data relatively quickly, detect patterns that indicate a potential security issue or even automatically respond to security incidents in real-time.
They can also help to automate many of the manual processes involved in CSPM.
Imagine this: you can use AI and ML to analyze log data from your cloud infrastructure to identify unusual patterns of network traffic that could indicate a cyber attack.
By automatically identifying these patterns, AI and ML can help you respond quickly and effectively to potential threats.
Who is already using AI and ML?
AI and ML may be new to many of us, but some forward-looking companies have already incorporated them into their cybersecurity programs.
For example, Netflix uses a combination of AI and ML to analyze log data from its cloud infrastructure to identify potential security threats, and this has allowed Netflix to respond more quickly and effectively to potential threats.
Multi-Cloud Support
A look at fighting future threats cannot exclude multi-cloud support for your CSPM of choice.
Today, it is quite common to find organizations adopting a multi-cloud approach to take advantage of economies of scale, price variations, and platform-specific features and benefits.
In fact, according to a recent study by Oracle, a whopping 76 percent of organizations surveyed are using a multi-or hybrid cloud approach for their cloud strategy.
It doesn’t make sense that your CSPM of choice does not support the cloud platform you have or intend to implement. Worse yet, ensure you are not restricted to just a few cloud service providers, as your CSPM does not support them.
If you have not chosen a CSPM, ensure that it will support your cloud platform of choice and others that you have already decided to use.
Most CSPMs support a variety of cloud providers, e.g., Horangi Warden supports major cloud platforms such as Amazon Cloud, Microsoft Azure, Google Cloud, and even Asian platforms like Alibaba and Huawei Cloud.
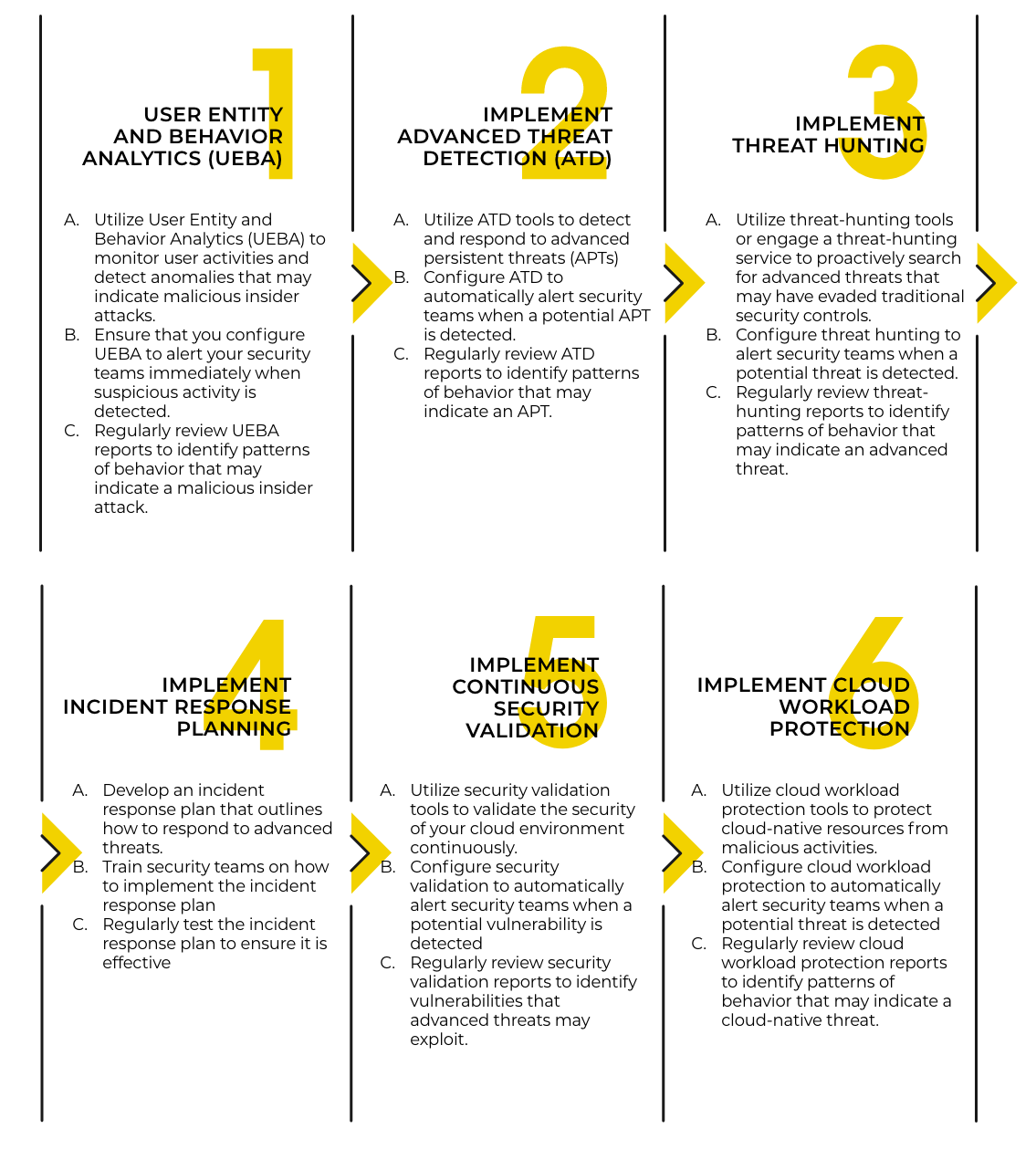
Step-by-Step instructions for implementing advanced CSPM strategies
Before we conclude this blog, here’s a summary you can take away to help your organization implement advanced CSPM strategies.
Conclusion
Today, threats facing your cloud environments are becoming more sophisticated and elusive.
Advanced CSPM strategies such as UEBA, ATD, threat hunting, incident response planning, continuous security validation, and cloud workload protection (CWPP) are critical for protecting your cloud environments, sensitive data, and systems from advanced and more sophisticated threats.
In the near future, you should consider using new technologies such as Artificial Intelligence (AI) and Machine Learning (ML) to remediate current threats and vulnerabilities better and be prepared for future dangers.
Finally, besides taking a proactive approach and selecting the right CSPM to secure your cloud environments, you should also ensure that your employees are trained on the latest security best practices and be mindful of establishing incident response procedures, conducting regular security audits, and be aware of compliance and regulatory requirements.
Ensuring your cloud environment is secure is a holistic exercise, and we are here to help. If you’d like a demo of the Horangi Warden CSPM or understand more about our other cybersecurity services, such as threat hunting, feel free to contact us today!




