Cybersecurity authorities in the United States., the United Kingdom, and Australia recently issued a joint advisory to warn organizations that ransomwareransomware threat actors are showing increasing “technological sophistication” that poses an “increased threat to organizations globally.”
Instead of just double extortions that first steal then encrypt sensitive data, ransomware threat actors are now using triple extortion to extract a ransom from organizations by:
- Threatening to publicly release the stolen data,
- Disrupting the victim organization’s internet access, and
- Making the breach known to the organization’s partners, shareholders, and suppliers.
The Bad News Doesn’t Stop There.
A recent survey by Hitachi ID uncovered a worrying trend: ransomware actors are increasingly targeting inside help for their ransomware attacks.
65% of large U.S.-based IT enterprises surveyed between December 7, 2021, and January 4, 2022, admitted that ransomware attackers have approached their employees to sabotage their networks from the inside.
Insider threats are instrumental to the success of a ransomware attack — a compromised account that has administrative privileges is a surefire way for cybercriminals to gain access to sensitive information.
IBM’s Cost of Insider Threats report places the overall cost of insider threats at just under US$11.5 million dollars. Criminal insiders, or turncloaks, cost organizations about US$4 million.
What can you do to combat these increasing threats?
Here Are 4 Ways To Defend Against Insider Threats And Ransomware
1. Employee Training
Humans remain the weakest link in any organization’s defense against ransomware despite advances in cybersecurity technologies.
If you haven’t already done so, it’s time to conduct anti-phishing training on a regular basis for your employees. You should also put in place a way for employees to report suspicious or dubious emails and encourage them to err on the side of caution.
An additional step you can take is to conduct a spear phishingspear phishing campaign, a deliberate, highly realistic simulation of phishing attacks that helps you assess if your employees are vigilant and resilient to phishing attempts.
2. Engage a Managed Threat Hunting Service
Threat hunting looks into your network to identify and suss out hidden threats that are already in your network.
You can build your own threat hunting team by redeploying existing manpower with the requisite skills from your IT or Internal Security teams.
However, that takes time and will mean additional overheads. And with the lack of cybersecurity professionals worldwide, the hiring process may take longer than you’d like, and it can be expensive to hire the best.
You can consider engaging a managed threat hunting service if you lack the resources to form a dedicated team for threat hunting.
Here are a few things you need to ask about the service:
- Does their team have the required certifications and whether they have the relevant experience as white hackers?
- What tools do they use? Do they deploy industry-recognized monitoring and EDR (Endpoint Detection and Response) instruments?
- Do they offer flexible engagements and are their programs tailored to your business needs and goals or is it a one-size-fits-all solution?
3. Right-Size with IAM
Rightsizing basically means provisioning just the right permissions to the right person(s) so that they can perform their work unhindered.
It’s just like what you would do in the physical world where you would give an engineer from the IT administration team access to the server room, but not for a colleague from, say, the sales team.
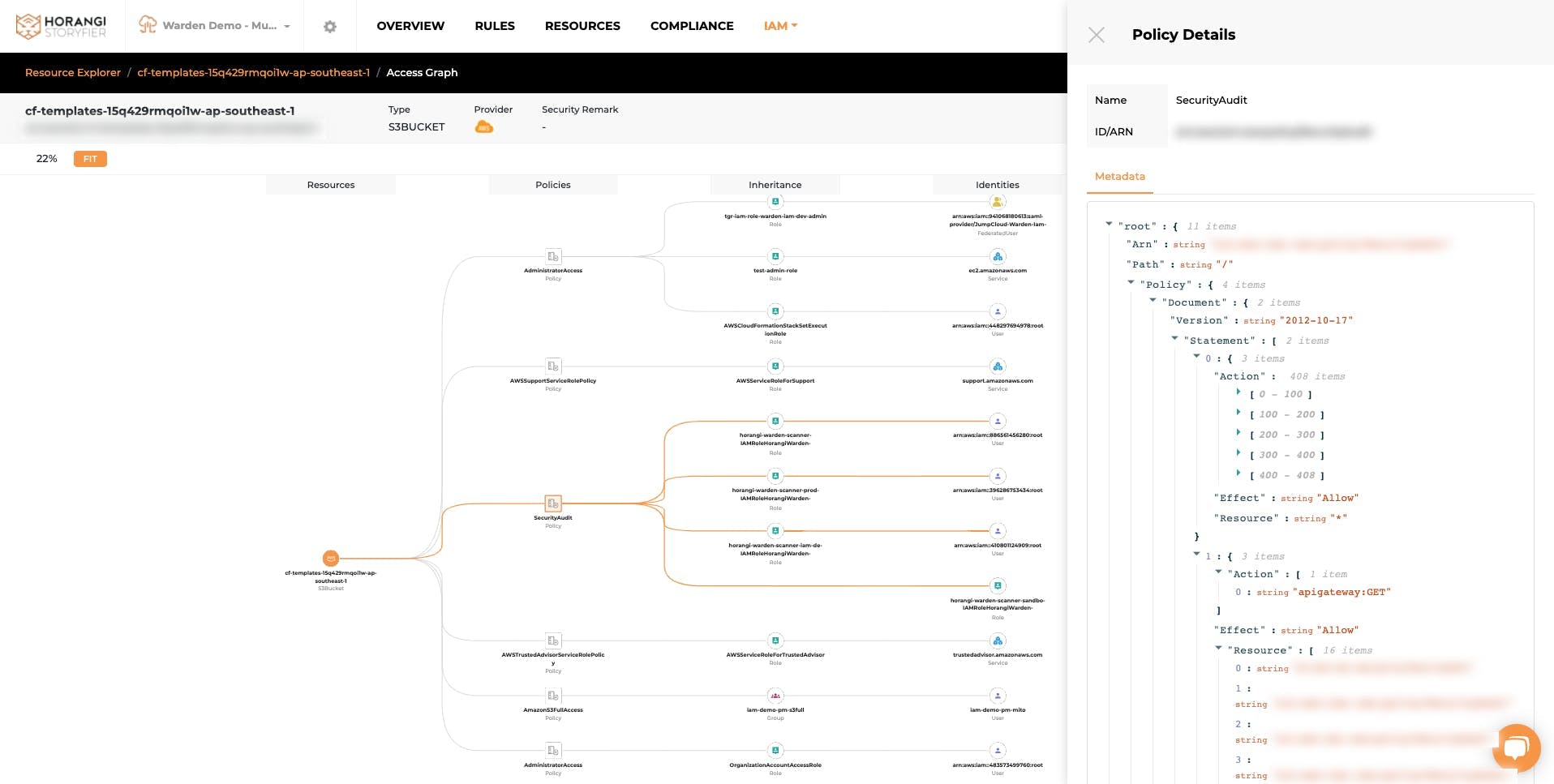
Use an IAM solution that has a graph visualizationgraph visualization so you can quickly see access paths and perform rightsizing in a matter of clicks.
A good IAM solution with graph visualization helps you easily identify excessive permissions (for example, by using colors to highlight them), and allows you to view impacted identities if and when you make any changes.
4. Yeeba-yeeba UEBA!
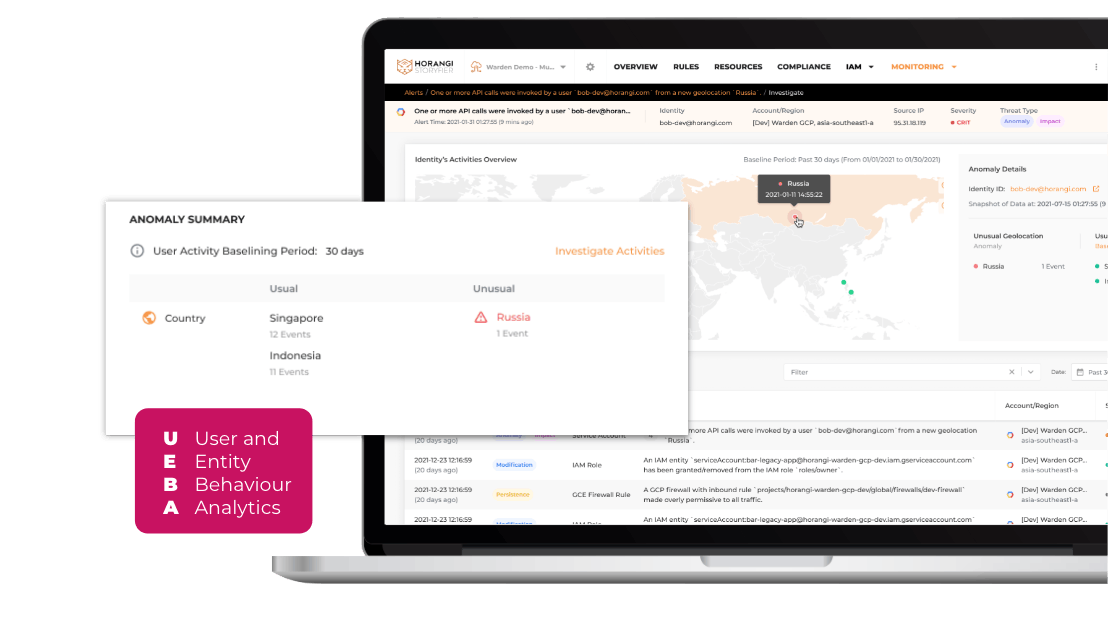
User and Entity Behavior AnalyticsUser and Entity Behavior Analytics (UEBA) is fast gaining traction as a useful and necessary tool to complement IAM (Identity and Access Management) and Threat Detection.
Why? What does UEBA do?
UEBA analyzes behavior patterns to recognize and understand normal user behavior patterns, then uses the information as a baseline to spot and flag suspicious behavior that may be indications of potential threats and attacks.
UEBA is usually packaged with most security automation tools like Cloud Security Posture ManagementCloud Security Posture Management (CSPM) tools.
If you are already using a CSPM tool, check to see if they have UEBA baked in, or if you are utilizing the UEBA module.
If not, here are some pointers for choosing a good CSPM tool with UEBA (or go ahead and downloaddownload our free guide to choosing a good CSPM):
- Is it cloud-native and agentless? You don’t want to install the monitoring tool on every single server. Ideally, you want a CSPM that’s quick and easy to install, so much so that even a non-technical employee can do it!
- Does it provide end-to-end visibility of all your cloud assets? Good cloud security hygiene begins with visibility — you can’t secure what you can’t see or don’t know is there.
- Does it help you comply with industry standards? Reaching compliancecompliance with industry and international compliance standards helps with ensuring that your customers and your data are protected. Some industries, such as Financial Services, require that you meet compliance standards before you can operate.
- Does it offer Threat DetectionThreat Detection and Vulnerability RemediationVulnerability Remediation?. Does it help you prioritize threats and offer quick remediation for threats? Can it help educate your IT staff so they can upskill and be more competent and confident to deal with future threats?
- Does it integrate with your current DevSecOpsDevSecOps? If not, is it easy to do so using, say, an APIAPI?
- Is the pricing reasonable? Can it be right-sized for your organization? It’s wasteful if you have to pay for an enterprise plan when you are a startupstartup or an SMB.
- Is it customizable, or one-size-fits-all? Your business is unique and in a unique space. Can the CSPM tool vendor provide customization?
Protection From Insider Threats And Ransomware Requires A Holistic Approach
Ransomware threat actors are using more sophisticated techniques and approaches to attack organizations. Implementing these four recommendations will help you better protect your organization from insider threats and ransomware.
If you are unsure of where or how to start strengthening your defenses against ransomware, come talk to us.